Information security professionals who are new in ISO 27001 very often tend to think this standard requires a very centralized and very detailed definition of roles and responsibilities. Actually, this is not true.
Please don’t get me wrong: assigning and communicating roles and responsibilities is important, because that is how all employees in the company will know what is expected of them, what their impact is on information security, and how they can contribute. But, ISO 27001 allows you to do it in a way that is natural for your business, and that does not introduce additional overhead – let’s see how…
What does ISO 27001 require?
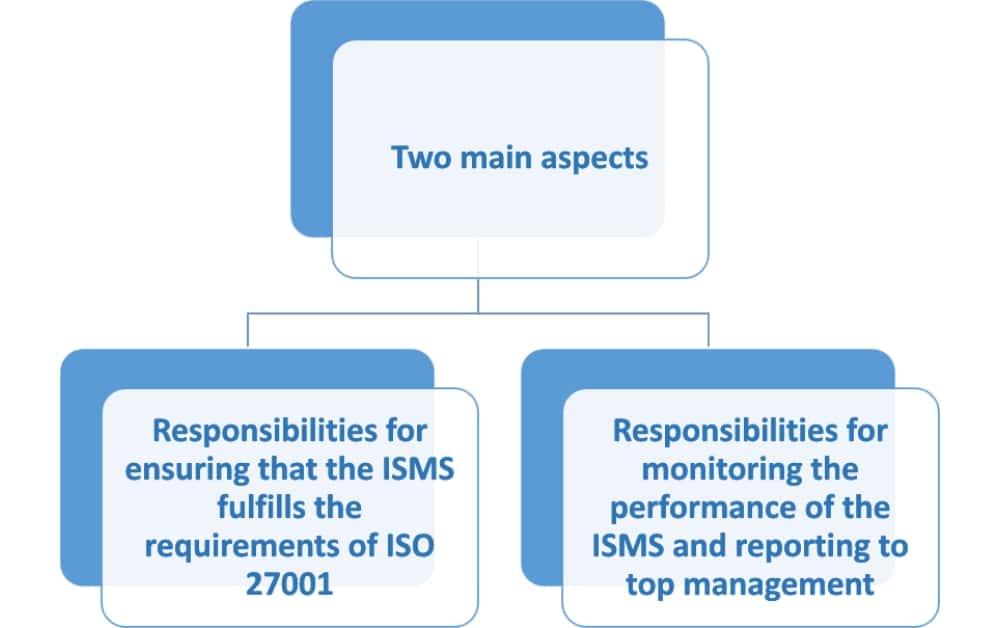
Clause 5.3 says that top management should assign top-level responsibilities and authorities for two main aspects:
- First are the responsibilities for ensuring that the ISMS fulfills the requirements of ISO 27001.
- And second are the responsibilities for monitoring the performance of the ISMS and reporting to top management.
The responsibilities for the implementation of controls should be documented through the Risk treatment plan, see this article for details: Risk Treatment Plan and risk treatment process – What’s the difference?
Further, ISO 27001 mentions responsibilities in several places (e.g. controls and subsections A.6.1.1, A.7.1.2, A.7.3.1, A.9.3, A.12.1, A.16.1.1, A.18.2.2) however it does not define how those responsibilities should be documented – this basically means you’re free to define them in any way you feel is appropriate.
Options for top-level responsibilities
The top-level responsibilities and authorities can be given to one or more people in the company, depending on what is the most appropriate. For example, for small companies with a simple ISMS, it is logical to assign one person to be responsible for implementing all the requirements from ISO 27001 and reporting the performance of ISMS to top management. This is usually the CISO; see also: What is the job of Chief Information Security Officer (CISO) in ISO 27001?
For bigger companies with a more complex ISMS, it might be more practical to have one person responsible for implementing the requirements and another for reporting. Another option would be to have one person for ensuring implementing the requirements and reporting for one segment of the ISMS, for example HR security, and another person for incident management, etc.
Where to document roles and responsibilities
You can document the general information security roles and responsibilities in job descriptions, or as part of the organizational chart, or in the Information Security Policy.
Of course, you should document specific security roles and responsibilities more detailed in various policies, procedures, plans, and other documents that you will develop as part of the ISO 27001 implementation.
So in practice, on the lower organizational level, security roles and responsibilities will be assigned as regular tasks – e.g., Backup policy will define initiating backup at a particular time of the day. These tasks should be given to the people who are probably already doing them, only now these roles and responsibilities will more formal. Monitoring and reporting should be done also through regular channels – typically, the direct superior of particular employees is in charge of monitoring them, and reporting about their results.
In other words, there is no need to have one document that would centrally define all detailed security roles and responsibilities. Such document wouldn’t be practical because of the redundancy – any time you would change some role or responsibility in a particular procedure, you would have to change it also in this central document. Sooner or later, a discrepancy would occur, and believe me – such situation is quite a big problem when dealing with the documentation.
ISMS documentation should serve you, not the other way around
So, to conclude: creating documents only for the purpose of showing them to the certification auditor does not make sense – you should be creating documents to help you do your job.
In other words, ISO 27001 documentation should be your tool for improving your security activities – therefore, when you define roles and responsibilities you should write them in a way that it is easy to understand, and write them in a place that is logical to find.
To see how employees can collaborate on ISO 27001 ISMS implementation steps, documents, and all the necessary tasks, sign up for a 14-day free trial of Conformio, the leading ISO 27001 compliance software.

 Dejan Kosutic
Dejan Kosutic