Update 2022-04-07.
The 2013 revision of ISO 27001 introduced a new concept: the risk owner. Since this concept brought quite a lot of confusion with information security practitioners, here’s an explanation of what the risk owner is, and whether the concept of asset owner from the old 2005 revision of ISO 27001 is still valid.
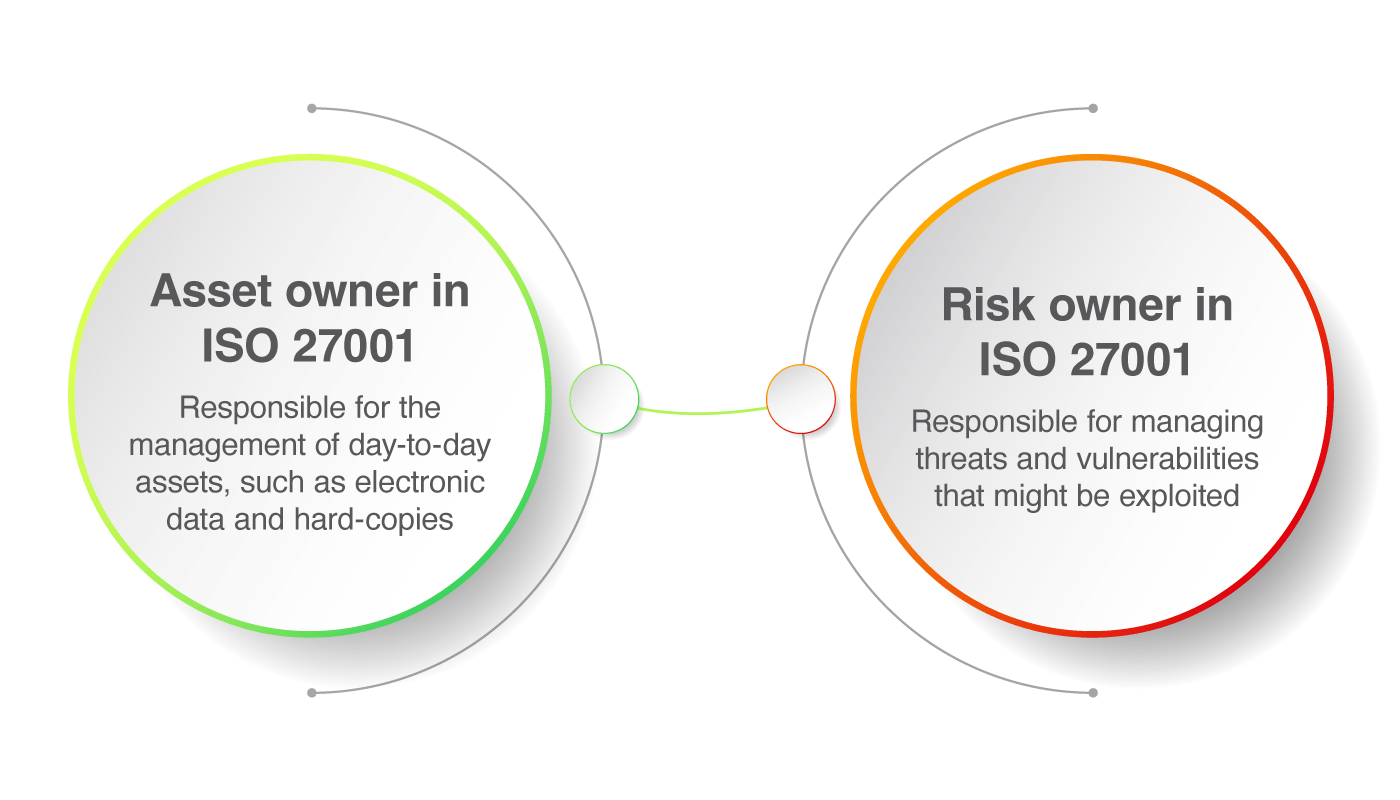
The asset owner in ISO 27001 is responsible for the management of day-to-day assets, such as electronic data and hard copies, as well as hardware, software, services, people, and facilities. The risk owner is responsible for managing threats and vulnerabilities that might be exploited.
What is the asset owner, according to ISO 27001?
The asset owner in ISO 27001 is responsible for the management of day-to-day assets, such as electronic data and hard copies, as well as hardware, software, services, people, and facilities.
Asset owners are usually lower in the organizational hierarchy than risk owners, since any issues they discover should be directed upwards and addressed by a more senior individual.
As an example, if the head of the IT department is responsible for the risks related to IT infrastructure, the asset owner of the servers containing the at-risk information would be the IT administrator.
Both the old 2005 and new 2013 revisions of ISO 27001 have the concept of asset owner as a control in Annex A – this is basically nothing but determining who is responsible for each asset in your company. In terms of information security, assets are not only the information in electronic and paper form, but also software, hardware, services, people, facilities, and everything else that provides value to an organization.
Why is this asset ownership important? Because if no one is responsible for an asset then no one will take care of it – only by strictly defining who is responsible for each document, each server, each external service, etc. will you make sure that each of those assets is properly protected and managed; not having owners of the assets would mean anarchy.
Asset-based risk assessment
Where the 2005 and 2013 revisions are different is that 2005 required the identification of asset owners both during the risk assessment process and as control A.7.1.2 in Annex A, whereas the 2013 revision doesn’t have this requirement in the risk assessment process and only as control A.8.1.2 in Annex A.
What’s more, the 2013 revision does not require so-called asset-based risk assessment, which would identify the risks based on assets, threats and vulnerabilities – according to ISO27001:2013, your company can identify risks using some other (less complicated) method.
However, my opinion is that asset-based risk assessment will continue to be a dominant method for risk assessment – especially if you choose to apply controls A.8.1.1 (identification of assets) and A.8.1.2 (assigning the owners to those assets). If you do list those assets, then you have already done a good part of asset-based risk assessment; in such case, even in the 2013 revision it makes sense to list assets (and their owners) during the risk assessment process.
What is the risk owner according to ISO 27001?
A risk owner in ISO 27001 is a person responsible for managing threats and vulnerabilities that might be exploited. Each identified risk may be managed by multiple personnel who have direct or indirect responsibility for, or oversight over, its management, and who work with the accountable risk owner to manage that risk.
So, for instance, an asset owner of a server might be the IT administrator, and a risk owner for risks related to this server might be his line manager or the head of IT. The IT administrator will manage the server on a day-to-day basis, while the head of IT will take care of, e.g., investing in better protection, or providing training to the IT administrator to reduce the overall risk.
In my opinion, the concept of risk ownership was introduced because very often, the asset owners did not have enough authority to resolve potential risks; besides, this concept also exists in ISO 31000, so this way ISO 27001:2013 was made compliant with ISO 31000.
How to choose the risk owners
When choosing risk owners, you should aim for someone who is closely related to processes and operations where the risks have been identified – it must be someone who will feel the “pain” if the risks materialize – that is, someone who is very much interested in preventing such risks from happening. However, this person must be also positioned highly enough so that his or her voice would be heard among the decision makers, because without obtaining the resources this task would be impossible. So, it seems to me that mid-level managers are often the best candidates for risk owners.
Even though the standard allows an entity to be a risk owner (e.g., a department or a business unit), I would not advise it – it is always better to have one individual who is in charge of resolving a problem than to have a group of people. For instance, if the head of the IT department is responsible for resolving the risk, it will be done much more quickly than if you had the whole IT department responsible for the same risk.
When it comes to appointing the risk owners, it is best done through the Risk treatment plan, since this is an action plan on how to resolve the risks – you should simply define for each risk who is responsible for implementing the controls. Read also Risk Treatment Plan and risk treatment process – What’s the difference?
To conclude, companies should determine both risk owners and asset owners when implementing ISO 27001 – the easiest way would be to determine them during the risk assessment process. And, by doing this properly, the implementation and operation of their information security will be a much easier job.
To see how to use the ISO 27001 risk register with catalogs of assets, threats, and vulnerabilities, and get automated suggestions on how they are related, sign up for a 14-day free trial of Conformio, the leading ISO 27001 compliance software.

 Dejan Kosutic
Dejan Kosutic