 Jean-Luc Allard
Jean-Luc Allard
March 23, 2015
Your information and IT assets aren’t located in the middle of nowhere. They need a roof, walls, doors, and adequate operating conditions. Just like human beings. Software has back doors (not always to be exploited for malevolent acts) just as any building has. Many IT security features are built on “old” physical security principles and solutions. As for IT, without proper physical security controls, our information assets are at risk.
Secure areas are sites where you handle sensitive information or shelter valuable IT equipment and personnel to achieve the business objectives. In the context of physical security, the term “site” means buildings, rooms, or offices that host all the services and facilities (electricity, heating, air conditioning).
The primary role of physical security is to protect your – material and less tangible – information assets from physical threats: unauthorized access, unavailabilities and damages caused by human actions, and detrimental environmental and external events.
The material assets are, of course, hardware and information media. Less tangible information assets are spoken words and shown data (on screens and posters).
Sites, buildings, public areas, work areas, and secure areas aren’t in the middle of nowhere or somewhere in the air. They are located at a place suitable for people. Three elements are to be taken into account as your physical context to decide for the appropriate protection:
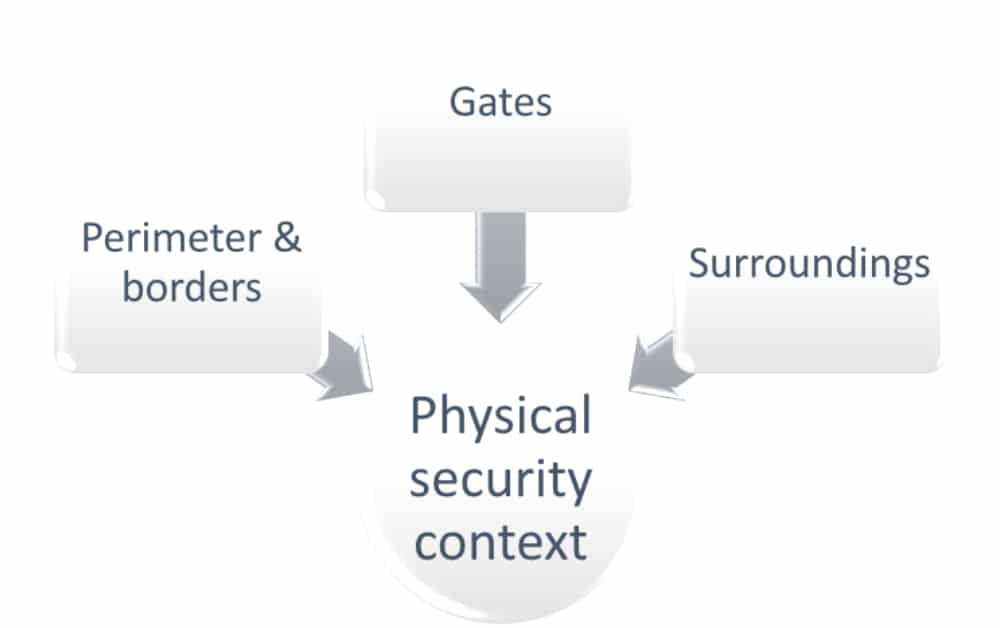
Perimeter & borders. We have up to four defense lines to take into account:
Gates. There is obviously a need to enter and exit the physical environment. The doors and windows are first thought of, but most people overlook the cable ducts, air inlets/outlets, etc.
Don’t forget the ways to and from the gates: access and exit ways, both normal and “emergency” – required by the safety regulations.
Surroundings. This concerns the corridors, paths, roads, green space, or parking areas that lay around the perimeters.
The physical environment, and especially the secure areas, should meet security expectations. This happens through providing the adequate level of strength as defined by the risk management activities to each of its elements. See also this article: ISO 27001 risk assessment: How to match assets, threats and vulnerabilities.
The first requirement is obvious: the strength of the perimeter should be adapted to its content.
Second: all six faces (4 walls + floor and ceiling) of the three last perimeters (floor, room, cabinet) should have the same strength. It serves little to have strong walls if you can get into the room via false ceiling or floor.
By “nature” (as it has always been the case in history), the most sensitive asset should be put within the strongest perimeter (“secure area”), which is protected by another one and so on (the “onion technique”).
The concept of “zoning” describes the different categories of “rooms” depending on what they contain and how they are located in relation with the others.
When it comes to working in a secure area, you may be required to control:
Control A11.5 also restricts the use of these secure areas. They should only be devoted to handling sensitive information and hosting valuable IT and facilities. They shouldn’t serve as storage places for paper, equipment, or other maintenance devices. Their location also shouldn’t ever be indicated to strangers.
For some parts of your facilities it shouldn’t even be authorized to take pictures.
When it comes to delivery and loading areas, you just have to make sure they don’t give direct access to the secure areas.
The doors and windows should have the same strength as the perimeter: a strong wall and a weak door or window (or reverse, as has already been seen) make little sense.
The gates should allow for an adequate level of access control of who wants to get in (or out). Again, the rights and rules are harmonized with the strength of the walls (and the value of what’s inside). For example, you could use a rule like this: For secure areas, an airlock (a security double door) could be necessary that makes sure to only authorize one person at a time (and prevents tailgating and piggybacking).
All gates should provide the necessary protection: if you need to let air (or cables) in and out, the aperture shouldn’t be big enough to let any animal (smart or not) inside, in relation with the damage it can cause.
The presence of a welcome desk where all visitors should come first is one possibility. Having personnel challenging the unknown persons or security guards patrolling is also a solution.
If you adequately protect the “normal” gate(s), it’d be wise to also design, install, and protect “emergency” gates (both for exit, obviously, and entrance – when the normal gate is blocked, to protect availability/accessibility of what’s inside).
All spaces around the perimeter(s) could be monitored (according to the value or sensitivity of what’s inside) to prevent, deter, and detect any attempts to enter (or exit) through alternative and specially made gates. Monitoring of surroundings is generally performed with cameras or patrols.
Securing your physical environment, and especially your secure areas, follows the same approach you use for your digital information: defining the context, assessing the risks, and implementing the most appropriate security controls: the highest the value and the risk, the highest your protection level. The necessary access control and monitoring activities follow the same rules as for digital information.
But, when speaking of physical security, this isn’t sufficient: you also need to secure the equipment and deal with environmental threats – but that’s a topic for another article.
To see all the necessary tasks for ISMS implementation and maintenance, and learn how to comply with ISO 27001 with less bureaucracy, sign up for a 14-day free trial of Conformio, the leading ISO 27001 compliance software.