 Rhand Leal
Rhand Leal
November 16, 2015
Update 2022-04-25.
If your company is delivering services in the cloud, you probably have more and more customers asking you how their personal data is protected. ISO 27001 is certainly a good way to do it; however, some enlightened customers might ask you for even more – compliance with ISO 27018, the standard that is specialized in personal data protection in the cloud. In this article, learn what ISO 27018 is and whether ISO 27018 certification is possible.
By the way, there is another cloud security standard in the ISO 27k series – ISO 27017. This standard provides general security guidelines for cloud providers and cloud customers. Learn more here: ISO 27001 vs. ISO 27017 – Information security controls for cloud services.
So, let’s answer the basic question first – what is ISO 27018? Its full name is ISO/IEC 27018 Code of practice for protection of personally identifiable information (PII) in public clouds acting as PII processors. IS0 27018 was first released in 2015, and reconfirmed in 2019 without any changes.
It focuses on protecting the personal data in the cloud, and it is published by the International Organization for Standardization (ISO), in partnership with the International Electrotechnical Commission (IEC). Both are leading international organizations that develop international standards. It adds additional cloud controls on top of the controls listed in ISO 27001/ISO 27002.
ISO 27018 is part of the set of ISO 27k series of standards developed to handle information security. Its purpose is to provide guidelines and guidance to help organizations, of any size or any industry, and to protect the information of natural persons under their responsibility in cloud environments. It can be used integrated with ISO 27002 (as a set of best practices) or integrated with an ISO 27001 Information Security Management System (ISMS).
ISO 27018 works in two ways: (1) it augments existing ISO 27002 controls (ISO 27002 provides a detailed explanation of ISO 27001 security controls) with specific items for cloud privacy, and (2) it provides completely new security controls for personal data.
Now that we’ve learned what ISO 27018 is, let’s see more about the options for ISO 27018 certification and what ISO 27018 compliance is. As a code of practice, ISO 27018 is not certifiable. Only ISO standards that define requirements for management systems, like ISO 27001, ISO 9001, and ISO 14001, are certifiable.
What happens in practice is that some certification bodies, as part of a broader ISO 27001 certification process, declare that the company is also compliant with ISO 27018 requirements. In such cases, an unofficial ISO 27018 certificate is created on top of the ISO 27001 certificate.
Although it was created as a part of the ISO 27k family of standards, as a code of practice, ISO 27018 can be used with other ISO management systems that cover cloud environments in their scopes.
For example, it can be used together with ISO 22301 to ensure business continuity in terms of availability and security of personal data. When used with ISO 9001 or ISO 20000, the ISO 27018 controls can improve processes efficiency by optimizing personal data protection.
The way to link ISO 27018 with these management standards is by means of their risk assessment requirements, i.e., the identification and treatment of risks to the standards and business core processes operated in cloud environments that can be related to personal information.
Let’s first see to what degree ISO 27018 suggests that existing controls should be augmented:
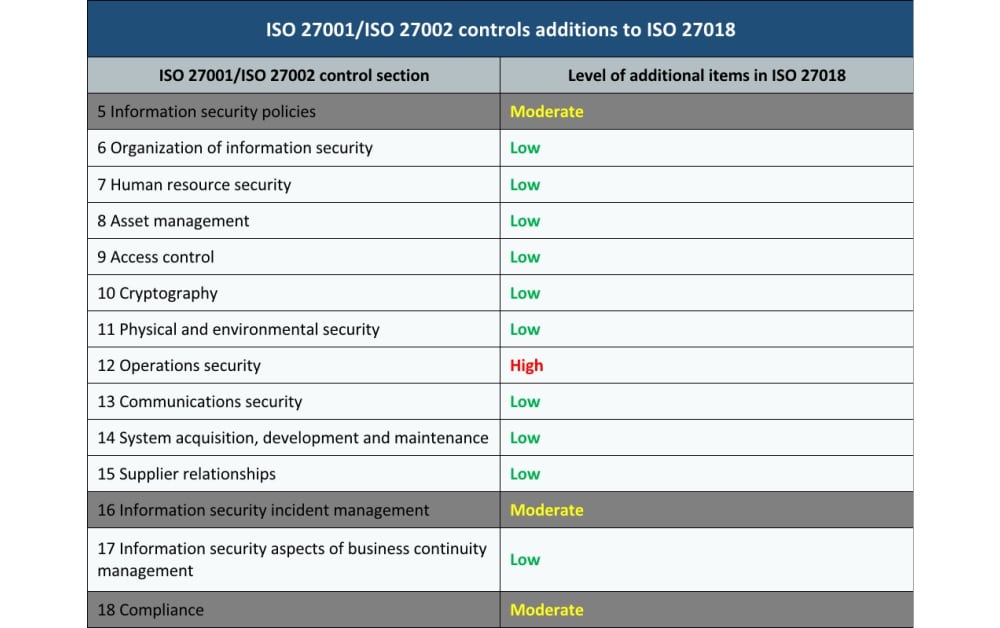
As you can see, ISO 27018 suggests the biggest additions in section 12 Operations security – this is mainly for the controls 12.1.4 Separation of development, testing and operational environments (when personal data is used for testing); 12.3.1 Information backup (multiple copies of data; procedures for the backup, recovery and erasure; providing information to the customer); and 12.4.1 Event logging (process for reviewing logs; recording changed privacy information; providing information to the customer).
Besides 12 Operations security, the additional items in other sections are surprisingly small.
Annex A of ISO 27018 lists the following additional controls (that do not exist in ISO 27001/27002) that should be implemented in order to increase the level of protection of personal data in the cloud:
All this is common sense, and I found it quite useful to have all these controls listed in a single document. Of course, ISO 27018 provides a detailed explanation for each of these bullets.
One client asked me recently whether they should go for ISO 27001 or ISO 27018 when operating a cloud service – I answered that this is both a marketing and a security question. From a marketing point of view, ISO 27001 is better because you will get a certificate that you can show to your clients; from a security point of view, ISO 27018 is much better because it provides detailed guidance.
However, the conclusion here is not to choose between the two standards, but to implement them together – ISO 27001 provides the best framework for the security management (with crucial emphasis on risk management), while ISO 27018 provides excellent cloud-specific security details. Simply start with ISO 27001 and add bits and pieces from ISO 27018 as you progress in your implementation project.
To learn how to comply with ISO 27001, while also implementing privacy and cybersecurity controls, sign up for a 14-day free trial of Conformio, the leading ISO 27001 compliance software.