 Antonio Jose Segovia
Antonio Jose Segovia
July 6, 2015
Updated: March 28, 2023, according to the ISO 27001 2022 revision.
Security in project management is an important part of ISO 27001 – many people are wondering how to set it up, and whether their projects should be covered with this control at all. Read this article to find the answers…
It is likely that you’ve heard that “the security of the information not should be seen as a product; it should be seen as a process.” This implies, among other things, that the security of the information is present in any establishment of the organization, being a pillar of the same, and serving as a cross support to the entire organization.
Beware: it is not the same to say that we are going to establish a methodology to manage projects in the field of information security (for example, use a methodology such as PRINCE2 project management to implement a project of ISO 27001), as to say that we are going to establish a methodology to treat the security of information in project management (for example, to use a risk management methodology to analyze security risks of the information relating to a project).
The ISO 27001:2022 standard talks about the second issue, and this will be what we will focus on, but we should take into account the order of the words – as you have seen, it is not the same.
The operation of each company is determined by the constant execution of projects in the short, medium, and long term (internal projects to maintain the structure of the organization, and external projects to provide services to customers).
Projects require collecting and processing data and generating information. They are becoming increasingly dependent on information systems that usually contain vulnerabilities and security flaws. When vulnerabilities are exploited, the success of the projects can be adversely affected. The level of information security in project management dictates how safe your project will be. To maximize long-term return on investment (ROI) with a project’s delivery, taking information security into account with all aspects is essential.
But security is something that is usually forgotten in projects; i.e., when a project is addressed in an organization, it does not usually take into account that it should be led according to the principles of information security project management. However, I’ve found some organizations, mainly large companies, that have included the information security in their projects as just one more activity (for example, running a risk assessment, focused on information security, at the beginning of any project to identify threats/vulnerabilities and risks).
And this is basically what ISO 27001 requests in Annex A.5.8 Information security in project management: Information security shall be addressed in project management, regardless of the type of the project. This control can be applied to all kinds of projects, from a minor IT implementation to a major business change project. Information security should be a part of ‘business as usual’ and, therefore, information security risks and objectives should be considered at the outset of each project.
All projects basically need resources, activities to develop, and established time objectives. Information security in project management can be integrated in several ways:
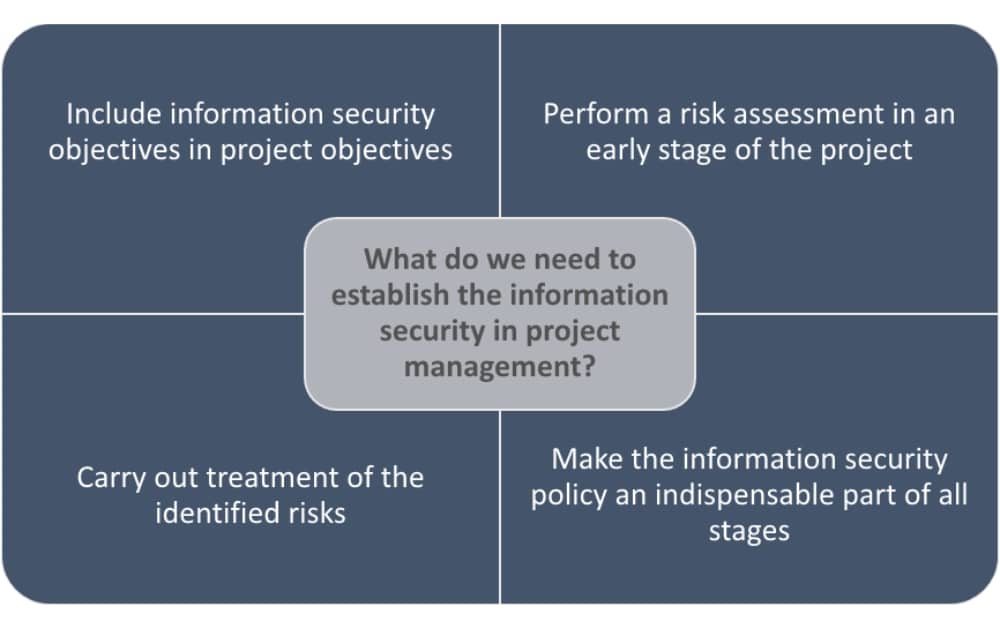
It’s particularly important (independent of the size of the organization) to include information security in project activities for those projects, e.g., which deal with or target integrity, availability, and confidentiality of the information.
In this way, information security will always be a component of the management of any project in the organization, and the organization will also comply with the requirement established by ISO 27001. So, let’s get a closer look into the benefits of information security project management.
ISO 27001 helps to manage the information security of all projects gathered under one roof. From project initiation to the protection from different threats such as data breaches and cyber-attacks, companies can anticipate risks, react accordingly, and secure their information. Documents, databases, devices, cloud servers, etc. remain safe within the project, which becomes resilient thanks to the implementation of ISO 27001.
This control also helps to provide greater importance and presence to the information security in the project management of the organization, which is always positive for this sector, since it is not seen as a simple requirement of a standard, but as a critical parameter in addressing and implementing any project in the organization.
Information security is probably not in place in the management of all projects in your organization. Many times, this is due to lack of knowledge, but after reading this article, that should no longer be an excuse. Also, keep in mind that when information security has more presence in your organization, you will be more important and you will be better valued.
To learn how to become compliant with every clause and control from Annex A and get all the required policies and procedures for controls and clauses, sign up for a free trial of Conformio, the leading ISO 27001 compliance software.