DORA Training & Awareness
Train your employees and third-party ICT service providers about DORA and RTS requirements and provide company-wide cybersecurity and resilience awareness.
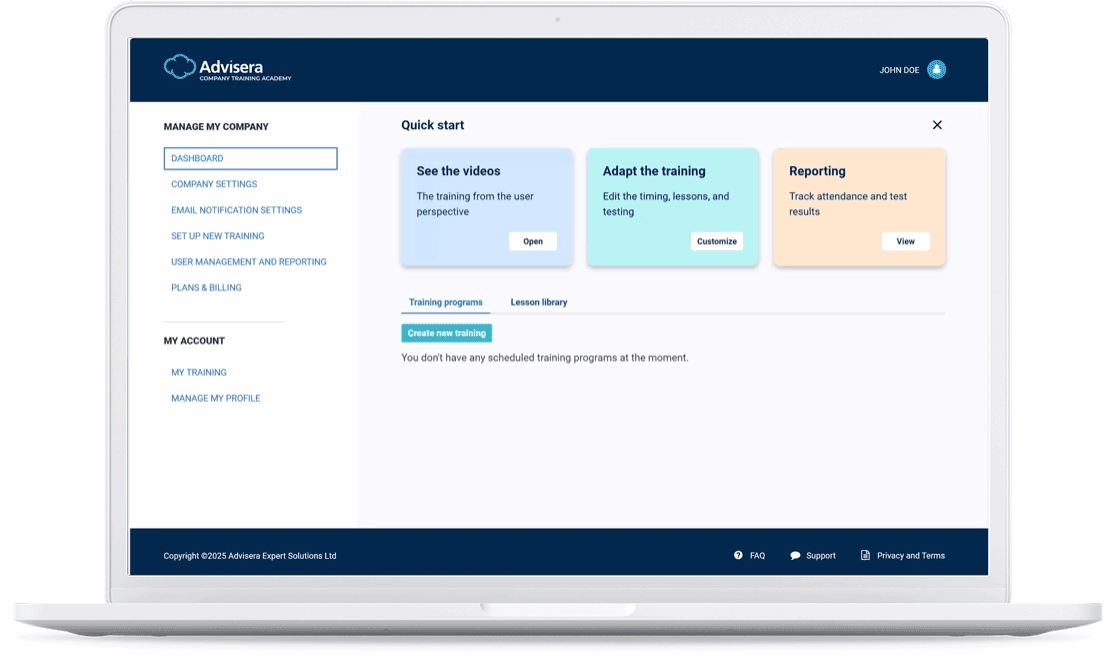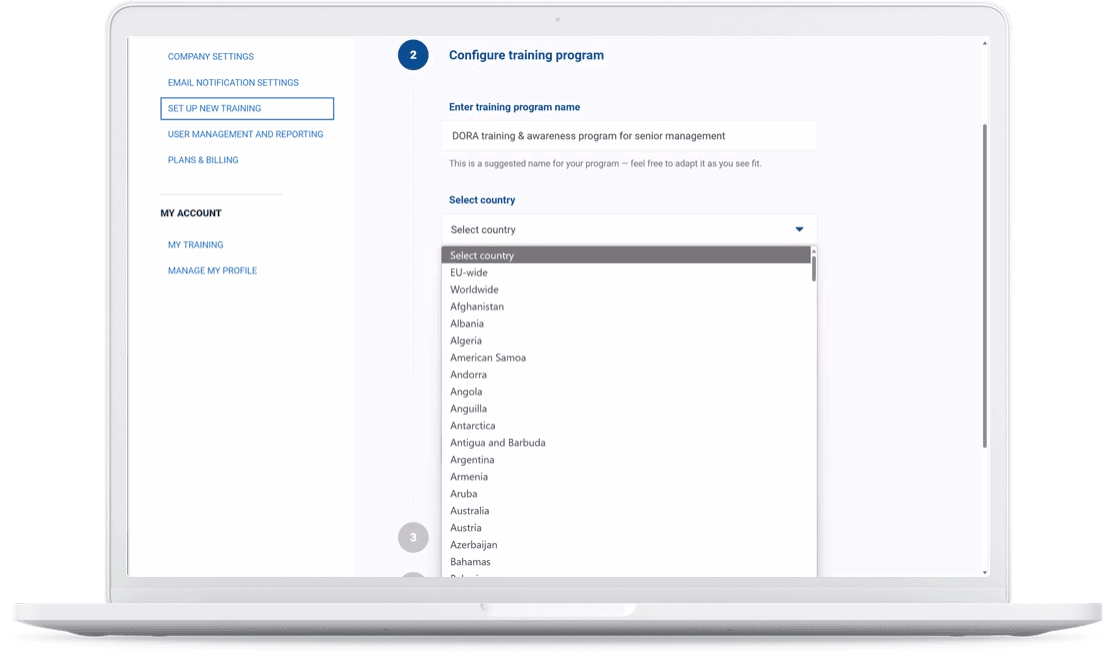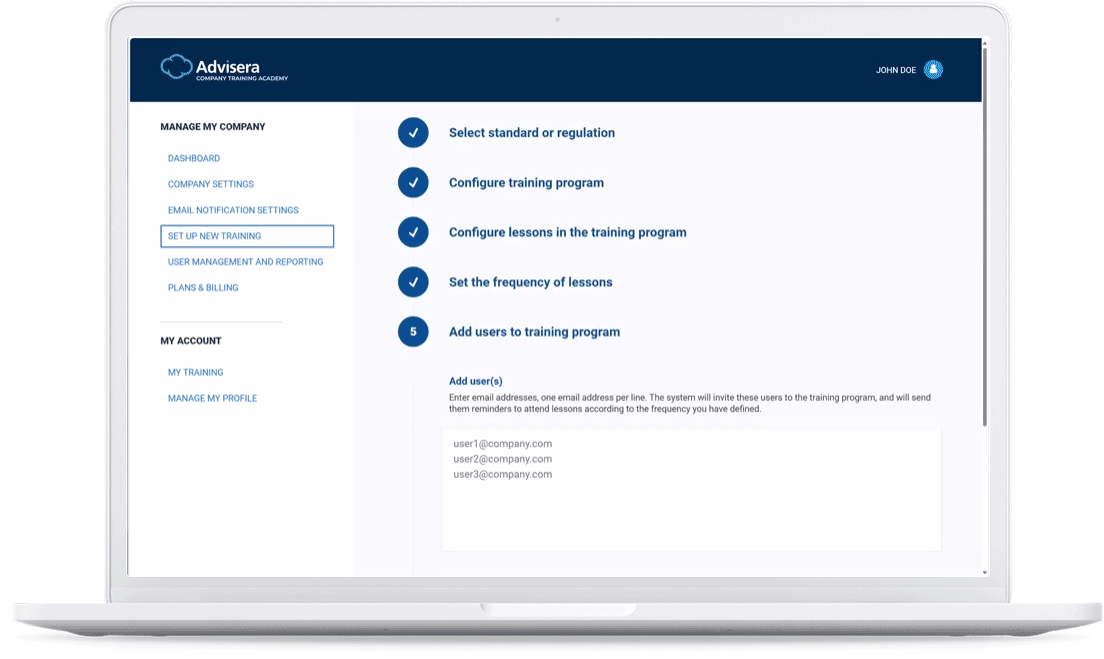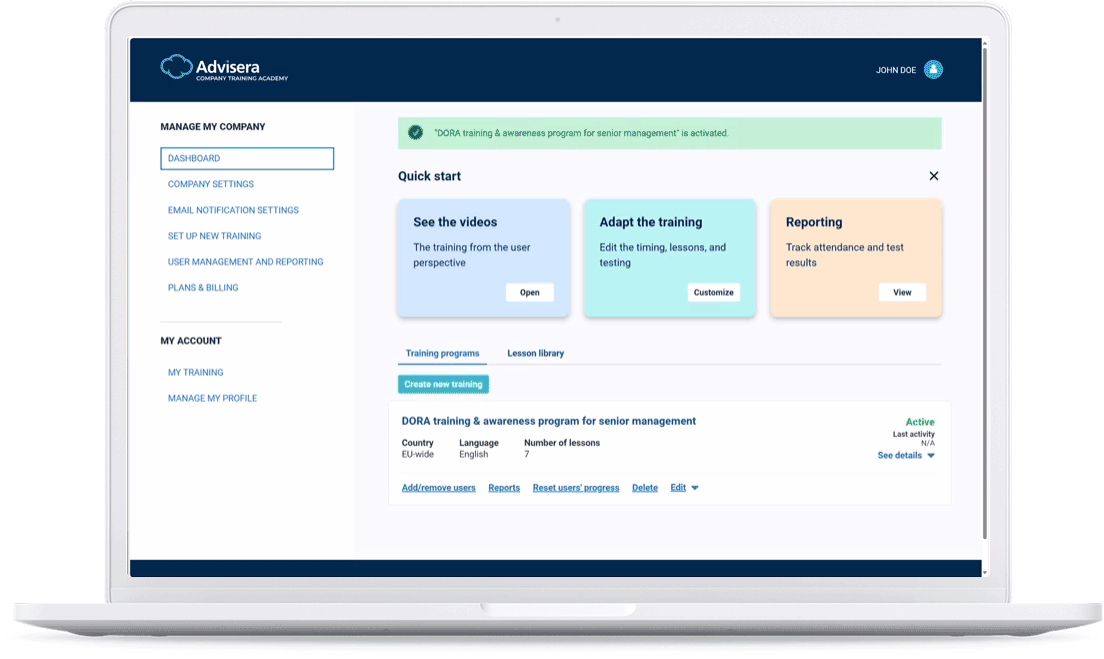
The quickest route to company-wide training
A set of 58 videos that explain all aspects of DORA and related regulatory technical standards (RTS), and that cover all key topics for cybersecurity and resilience for financial entities and for third-party ICT service providers — configure the whole training & awareness program in a couple of minutes, and enable each employee to watch videos on their devices.
On the left-hand side, you can see one of the videos from the DORA Training & Awareness available in Advisera’s Company Training Academy.
DORA lessons library
- What is DORA? (3:46)
EU regulation for digital resilience in financial sectorWhole DORA
- Who needs to comply with DORA? (2:41)
Which financial institutions and other companies must comply?Whole DORA
- Which IT providers need to comply with DORA and how? (3:49)
Securing ICT Supply Chains for Financial ResilienceWhole DORA
- What are DORA-related regulations? RTS, CDR, and CIR (3:13)
Additional Requirements Through Regulatory Technical StandardsCDR 2024/1502, CDR 2024/1505, CDR 2024/1772, CDR 2024/1773, CDR 2024/1774, CIR 2024/2956
- What are the main requirements specified in DORA? (3:45)
Summary of 9 Most Important RequirementsWhole DORA
- DORA implementation steps (4:54)
Optimal Steps for DORA Compliance Project ImplementationWhole DORA
- Writing DORA documentation (3:30)
Structure and Content of DORA DocumentationCDR 2024/1774, DORA Article 2
- DORA: Organizing training and awareness (2:57)
Key training & awareness requirements and how to comply with themDORA Articles 5, 13, 16, and 30
- DORA: Penalties and fines (3:08)
Who Enforces Them and How Do They Look Like?DORA Articles 50, 51, and 54
- DORA: Governance responsibilities for senior management (2:30)
Implementing Internal Governance & ICT Risk OversightDORA Article 5
- DORA: Key elements of ICT risk management framework (3:42)
Description of Overall Activities in ICT Risk Management FrameworkDORA Article 6, CDR 2024/1774 Article 3
- DORA: Developing top-level information security policy (1:54)
Content of the Top-level PolicyDORA Article 9; CDR 2024/1774 Article 29
- DORA: How to write Digital operational resilience strategy (3:06)
Key Elements of the StrategyDORA Article 6
- DORA: Identifying ICT-supported business functions and assets (1:36)
ICT Function Mapping & Asset Lifecycle ManagementDORA Article 8; CDR 2024/1774 Article 4
- DORA: Performing risk assessment (2:43)
Mandatory Elements of ICT Risk AssessmentDORA Article 8; CDR 2024/1774 Articles 3 and 5
- DORA: Learning and evolving (2:40)
Methods for Continuous Cybersecurity EvolutionDORA Article 13
- DORA: Measurement, monitoring, and controlling the ICT systems (1:14)
Elements of Continuous Measurement, Monitoring, and ControllingDORA Articles 9 and 13; CDR 2024/1774 Articles 2 and 31
- DORA: Internal audit of ICT risk management framework (1:23)
Performing Internal Audit for ICT Risk ComplianceDORA Article 6
- DORA: Follow-up and corrective actions (2:16)
The Purpose and Content of the Follow-upDORA Articles 6, 13, and 17
- DORA: Report on the review of ICT risk management framework (2:23)
Details of the Annual Review and ReportingDORA Article 6; CDR 2024/1774 Article 27
- DORA: Main elements of simplified ICT risk management framework (6:42)
Requirements for Small Financial EntitiesDORA Article 16; CDR 2024/1774 Articles 28 to 41
- DORA: Policies and procedures for ICT operations security (1:40)
The Content of Operational Security DocumentsDORA Article 9; CDR 2024/1774 Article 8
- DORA: Capacity and performance management (1:39)
Optimizing ICT Capacity and Performance for Operational ResilienceDORA Articles 7 and 9; CDR 2024/1774 Article 9
- DORA: Data and system security (2:12)
Comprehensive Data and System Security Procedure RequirementsDORA Article 9; CDR 2024/1774 Article 11
- DORA: Network security management (1:58)
Main Methods for Ensuring Network SecurityDORA Article 9; CDR 2024/1774 Article 13
- DORA: Securing information in transit (1:39)
Ensuring Secure Data Transmission and ConfidentialityCDR 2024/1774 Article 14
- DORA: Encryption and cryptography (2:02)
Management of Encryption and Cryptographic KeysDORA Article 9; CDR 2024/1774 Articles 6 and 7
- DORA: Human resources policy (1:31)
HR's Role in Digital Operational ResilienceDORA Articles 5 and 13, CDR 2024/1774 Article 19
- DORA: Identity management and authentication (1:13)
Requirements for Identity Policies and Authentication MechanismsDORA Article 9; CDR 2024/1774 Article 20
- DORA: Access control (2:38)
Regulatory Requirements and Best Practices for Access ControlDORA Article 9; CDR 2024/1774 Article 21
- DORA: Physical and environmental security (1:36)
Physical and Environmental Security Policy for ICT AssetsCDR 2024/1774 Article 18
- DORA: ICT systems acquisition, development, and maintenance (2:36)
ICT Systems Lifecycle Security Policy and TestingCDR 2024/1774 Article 16
- DORA: ICT project management (1:24)
Rules for Managing ICT ProjectsCDR 2024/1774 Article 15
- DORA: ICT change management (2:16)
Elements of Change Management for Secure ICT SystemsDORA Article 9; CDR 2024/1774 Article 17
- DORA: Logging (1:14)
Logging Procedures for Recording Critical EventsCDR 2024/1774 Article 12
- DORA: Detecting anomalous activities (1:40)
Elements of Collecting and Analyzing ActivitiesDORA Article 10; CDR 2024/1774 Article 23
- DORA: Vulnerabilities, patch management, and updates (2:11)
Vulnerability Management and Patch Processes for ICT SystemsDORA Article 9; CDR 2024/1774 Article 10
- DORA: Incident management process (2:51)
Systematic Incident Handling and Rapid ResponseDORA Article 17; CDR 2024/1774 Article 22
- DORA: Classification of ICT incidents and threats (4:05)
Detailed Classification CriteriaDORA Article 18; CDR 2024/1772 Articles 1 to 10
- DORA: Reporting major incidents and cyber threats (3:05)
Types of Incident Reports for AuthoritiesDORA Article 19
- DORA: ICT business continuity policy (2:13)
Elements of the Top-level Business Continuity DocumentDORA Article 11; CDR 2024/1774 Article 24
- DORA: Business impact analysis, RTO, and RPO (1:44)
The Purpose of RTOs and RPOs for Business ContinuityDORA Articles 11 and 12; CDR 2024/1774 Article 24
- DORA: Backup and restoration of data (2:01)
Detailed Rules for Setting Up Backup and RestorationDORA Article 12
- DORA: Secondary processing site (1:36)
Alternative Site Requirements for Central CounterpartiesDORA Article 12; CDR 2024/1774 Article 24
- DORA: ICT response and recovery plans (2:02)
Requirements for the Content of the PlansDORA Article 11; CDR 2024/1774 Article 26
- DORA: Testing business continuity and recovery plans (3:03)
Detailed Requirements for Plan TestingDORA Article 11; CDR 2024/1774 Article 25
- DORA: Crisis management and communication (1:33)
Elements of Handling CrisisDORA Articles 11 and 14
- DORA: Main elements of digital operational resilience testing (2:07)
Comprehensive Testing Program for ICT Risk ResilienceDORA Article 24
- DORA: Resilience testing of ICT tools and systems (1:31)
Types of Resilience TestsDORA Article 25
- DORA: Threat-Led Penetration Testing TLPT (3:15)
Requirements for TLPT and for TestersDORA Articles 26 and 27
- DORA: Key elements ICT third-party risk management (4:30)
Governance, Assessment, Contracts, and Exit StrategiesDORA Article 28; CDR 2024/1773 articles 1 to 4
- DORA: Selecting critical ICT service providers (3:29)
Critical ICT Provider Designation and Oversight FrameworkDORA Article 31; CDR 2024/1502 Articles 1 to 6
- DORA: Risk assessment of ICT service providers (3:02)
Assessing Suppliers Before Signing ContractsDORA Article 29; CDR 2024/1773 articles 5, 6, and 7
- DORA: Contracts with ICT service providers (4:32)
Standardized Security Clauses for Protection of ICT ServicesDORA Article 30; CDR 2024/1773 Article 8
- DORA: Register of information (3:43)
Standardized Register for ICT Contractual OversightDORA Article 28; CIR 2024/2956
- DORA: Monitoring, inspection, and audit of ICT service providers (2:17)
Independent Review and Ongoing MonitoringDORA Articles 28 and 30; CDR 2024/1773 Article 9
- DORA: Exit strategies for ICT services (3:48)
Enabling a Smooth Transition Away From a Service ProviderDORA Article 28; CDR 2024/1773 Article 10
- DORA: Government oversight of critical ICT service providers (2:56)
The Tasks and Powers of the Lead OverseerDORA Articles 33 to 43
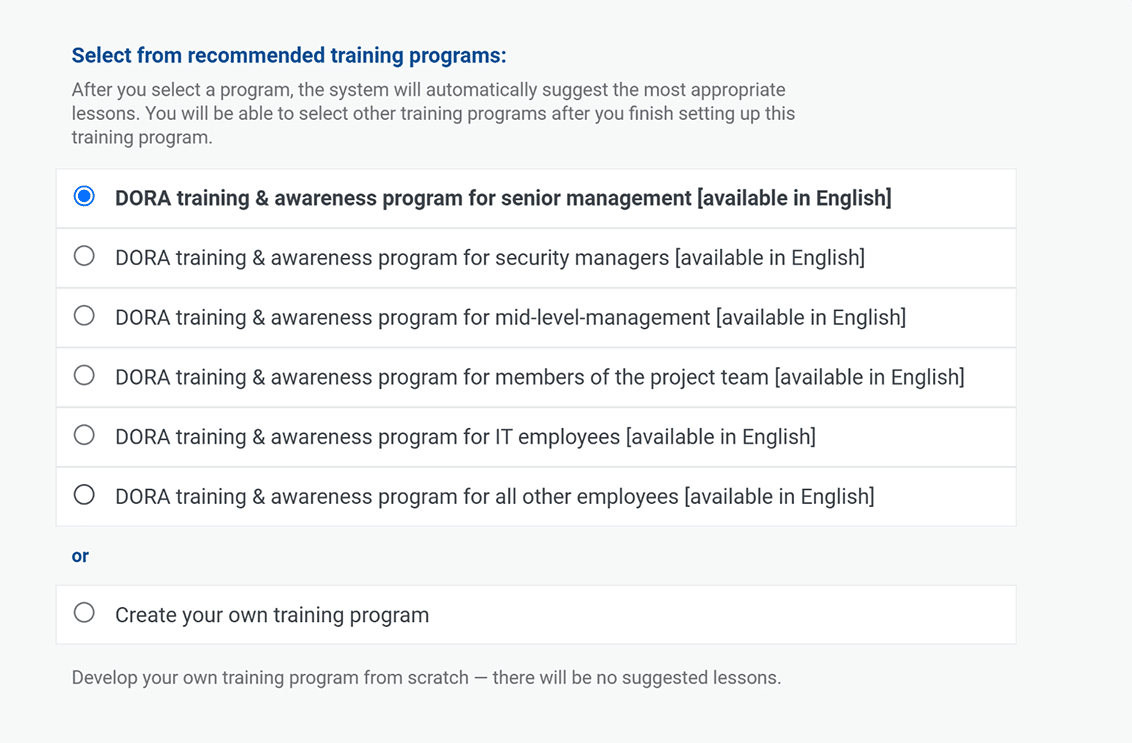
Training adjustable for different audiences
Instead of showing the same videos to everyone, you can configure the system so that senior management will see only the videos appropriate for them, IT employees will see different videos, the rest of the employees something else, etc.
Advisera’s Company Training Academy will suggest the most appropriate videos for different audiences, but you’re in control — you define who gets to see what.
Automate training delivery and tracking
You don’t have to torture yourself with organizing a live training that lasts longer than anyone wants to attend. Instead, use Advisera’s Company Training Academy to define how often employees need to watch videos, automatically send email invitations to watch them, track who watched each video, send reminders, and create attendance reports for audit purposes
Thousands of Successful Customers
Made for easy learning
Let’s face it — people don’t have time to learn about cybersecurity, and most have a hard time understanding techy or lawyer language.
This is why our videos are between 2 and 10 minutes long, and our DORA experts explain the topics using easy-to-understand language.
Several languages available
We’re translating the videos into all major languages so that any employee in your company can easily understand them.
Besides English, we have videos in German, French, Italian, Dutch, Spanish, Portuguese, Croatian, and we’re adding more.
Custom-made videos
Do you have specific cybersecurity policies or procedures that you’d like to present in a video? No problem! As part of selected plans, we can create custom videos exclusively for your company — personalization has never been easier.
You can also upload the videos you created to complement Advisera’s training videos.


Upload Your Own Training Materials
You can upload your own materials and turn them into engaging lessons. Combine your company’s internal documents, videos, or policies with Advisera’s learning system to build a personalized training experience for your employees.
For all use cases
Do you want to organize initial cybersecurity training for your project team? Or do you want regular, continuous training for your whole workforce? Or perhaps onboarding for new employees?
With the Company Training Academy, you can cover all of these cases by setting up separate training programs.

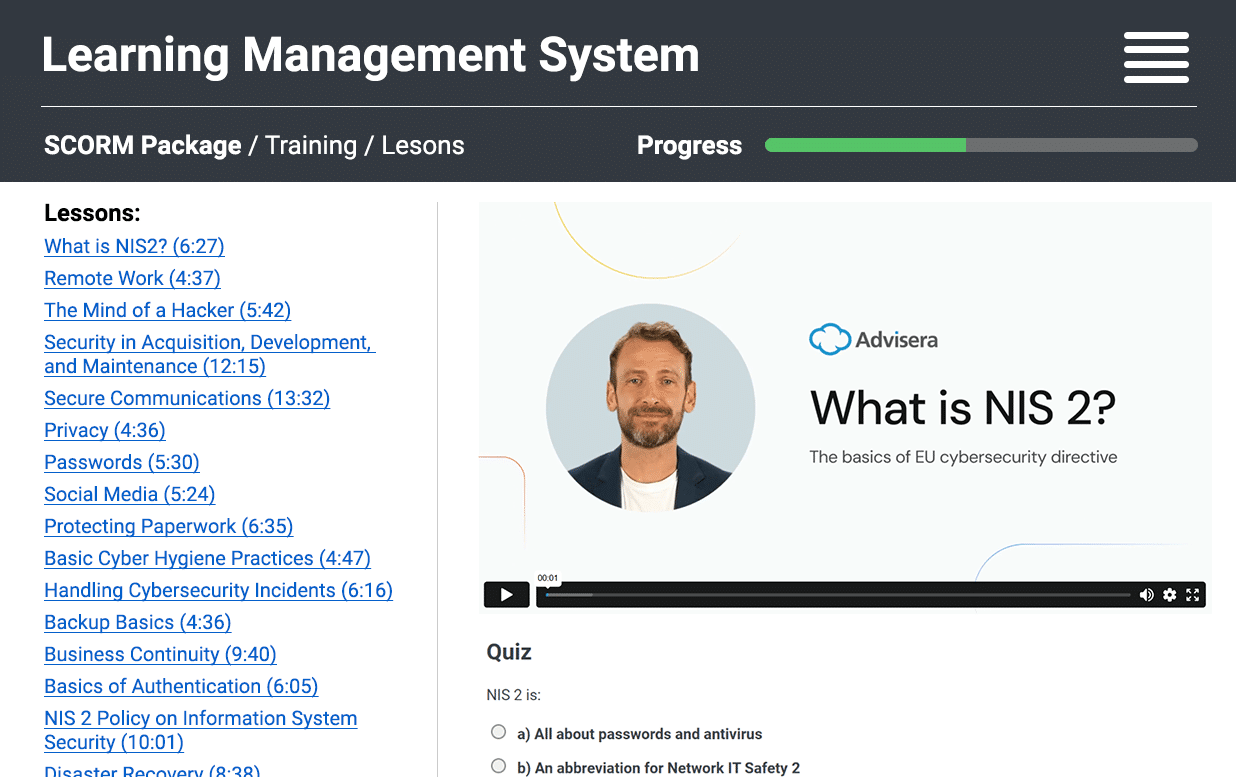
SCORM compatibility for your LMS
Use our training videos in your own learning management system (LMS) — all lessons are available as SCORM packages, including videos, quizzes, and progress tracking. Stay in control while delivering content through your existing platform.
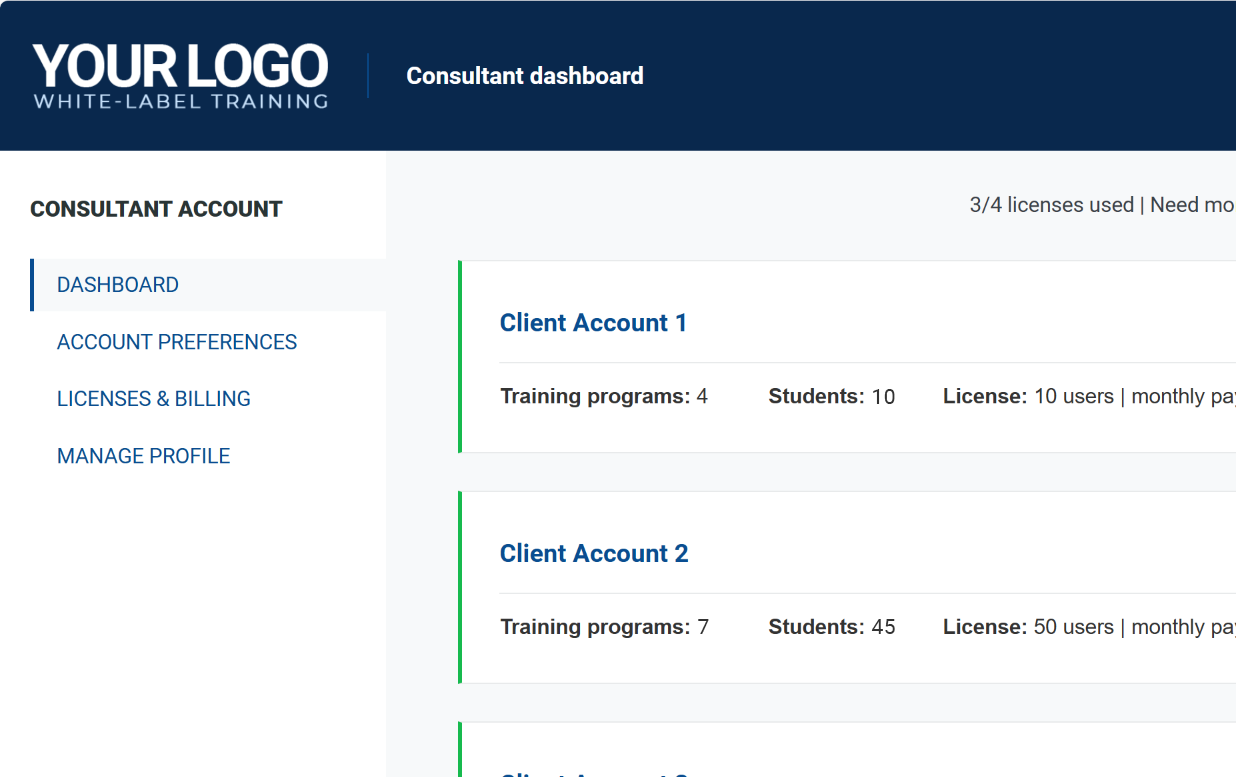
White-label platform for consultants
Grow your business by offering branded cybersecurity and compliance training to your clients. With Advisera’s platform, you can set up and manage training programs for multiple clients — all from one dashboard.
Monthly plan 10 users included
€14
/ month
$15
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 25 users included
€28
/ month
$29
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 50 users included
€56
/ month
$59
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 100 users included
€95
/ month
$99
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 200 users included
€189
/ month
$199
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 300 users included
€285
/ month
$299
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 400 users included
€380
/ month
$399
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Monthly plan 500 users included
€475
/ month
$499
/ month
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available only in yearly plan)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available only in yearly plan)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 10 users included
€154
/ year
$162
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 25 users included
€298
/ year
$313
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 50 users included
€605
/ year
$637
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
(available in yearly plans with 100 or more users)
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 100 users included
€1016
/ year
$1069
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
1 video per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 200 users included
€2042
/ year
$2149
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
2 videos per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 300 users included
€3068
/ year
$3229
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
3 videos per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 400 users included
€4094
/ year
$4309
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
4 videos per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
(available in yearly plans with 500 or more users)
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Yearly plan 500 users included
€5120
/ year
$5389
/ year
Unlimited access to all videos
Access to any training and awareness video about cybersecurity, ISO 27001, NIS2, DORA, GDPR, or ISO 42001 in any language, for any of your employees
Access to translated videos
Currently, all NIS2 and cybersecurity videos are translated and available in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian.
Country-specific videos
When a particular EU country publishes its own laws and regulations based on, e.g., NIS 2, we will create videos that address those additional requirements.
Adapt training for audiences
Create separate training programs for senior management, mid-level management, IT employees, all other employees, etc. so that each group watches only the videos relevant to them.
Set training schedule
Choose daily, weekly, monthly, or other frequencies of watching training videos.
Automatic notifications
Configure automatic email notifications sent to employees about upcoming and overdue training videos.
Track employees’ progress
See exactly who has attended which training video, who is late, and the testing results; download reports in PDF.
Quizzes and tests
Decide for each training program how you want to test the attendees.
Upload your own materials
Upload your own videos and documents, and add them to existing training programs.
Custom-made videos
Based on your script, we will produce training videos (up to 10 minutes per video) that you can use within the Company Training Academy.
5 videos per year
In-house live online training
Customized interactive webinar delivered by our expert for your company – up to 1 hour, up to 500 attendees.
1 training per year
SCORM packages
Get SCORM versions of our training programs to run them in your own LMS. All content — videos, quizzes, and progress tracking — included and ready for integration.
(available only in custom plan)
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
Contact us for pricing
Custom number of users
Unlimited access to all videos
Access to translated videos
Country-specific videos
Adapt training for audiences
Set training schedule
Automatic notifications
Track employees’ progress
Quizzes and tests
Upload your own materials
Custom-made videos
In-house live online training
SCORM packages
For all company sizes, all industries
All videos were created to be relevant for small, medium, and large entities, and also for all industries — no matter if your organization is a small brokerage house or a large bank, your employees will find these videos very appropriate.
In other words, any company complying with DORA regulation will find these videos to be the right fit.
Frequently Asked Questions
What is the Company Training Academy?
The Company Training Academy is a company-wide cybersecurity training platform that enables you to configure various training and awareness programs for your entire workforce for, e.g., NIS2, DORA, ISO 27001, GDPR, ISO 42001, security awareness, etc.
How long does it take to set up company-wide training and awareness?
Opening a client account takes less than a minute. The wizard will then guide you through the process of setting up your first training and awareness program, which usually takes 5–10 minutes.
How does the free trial work?
During the 14-day free trial, you will get access to all training & awareness videos, but you will be limited to 10 users. Some more advanced features will be accessible when you upgrade your account. No credit card required.
What forms of payment do you accept?
We accept payment via any major credit or debit card; for a larger number of users, you can pay via wire transfer from your bank account.
How does the Company Training Academy compare to Advisera’s courses?
Advisera’s courses are intended for individuals who want to get in-depth knowledge about a particular framework, while the Company Training Academy is intended for companies that want to automate training and awareness for all of their employees, and track their progress.
Which standards and regulations are covered in the Company Training Academy videos?
Currently, the videos cover NIS2, DORA, ISO 27001, GDPR, ISO 42001, and cybersecurity awareness training.
We’re working on adding videos for other standards and regulations.
Are videos available in languages other than English?
Besides English, we currently have videos in German, French, Italian, Dutch, Spanish, Portuguese, and Croatian. We are working on adding more languages at the moment; please contact us to learn about available languages.
Can we use these videos in our own Learning Management System (LMS)?
Yes. Our training is available as SCORM packages, including videos, quizzes, and progress tracking, for easy integration into your Learning Management System (LMS) – contact us to request the SCORM packages.
Can I upload our own materials to the Company Training Academy?
Yes. You can upload your company’s own training materials and create lessons from them. Supported formats include documents (PDF, DOCX, PPTX, XLSX, etc.), videos (YouTube, Vimeo), and text-based lessons you can create directly in the editor.
Is there a time limit for attending the training?
No, your users can spend as much time as they like attending the lessons, as long as your subscription is active.
What will the users need to access the lessons?
Your users can access the lessons using PC, Mac, or mobile devices, using any major browser (e.g., Chrome, Mozilla, Edge, Safari); a broadband Internet link will also be needed.
What is the format of the training, and how long does it take?
The lessons are a combination of video lectures, quizzes, and test questions. The average time needed per lesson is between 5 and 10 minutes. You can configure your training program to include only a couple of lessons, or several dozen lessons.
What prior knowledge is needed to attend the training?
None. The lessons are created in such a way that a beginner can easily understand them. They are very easy to follow for any type of employees — senior or mid-level management, non-IT employees, tech people, etc.
How can I upgrade my account if I need more users?
Simply click the purchase button for the required number of users in the pricing table, and, after the payment is processed, your Company Training Academy will be upgraded automatically.
Please make sure you use the same email address that you use for your existing account, because it is the only way this process can be done automatically. If you decide to make the purchase with a different email address, make sure you contact our support at support@advisera.com so we can upgrade your account manually.
Is it necessary to purchase training and awareness certificates?
No — you can use a Company Training Academy without purchasing certificates.
There are so many videos — how will I find what is the most appropriate for us?
The Company Training Academy will suggest the most appropriate videos based on the framework you’re interested in (e.g., NIS2), and based on your audience (e.g., senior management).
Further, you can filter all the videos in the Library by country, language, relevant clauses and articles of the framework, and other criteria.
Schedule a Demo
Want our expert to walk you through the product? Schedule a short call. We respond quickly.
