 Rhand Leal
Rhand Leal
November 2, 2015
Update 2022-09-06.
Think about a house, or office, with only one big space where you can arrange all your loved and precious things the way you think most appropriate. Tempting, isn’t it? The flexibility to use the space and ease of seeing everything right away seems like a big deal. Now, imagine this house, or office, being broken into. Now, what about your loved and precious things?
This situation is very similar to many network implementations made worldwide. By searching for an easy and uncomplicated network management, or by lack of knowledge, many organizations end up with hundreds, or thousands, of pieces of equipment connected in a single and gigantic network. Beyond performance problems, this kind of situation can bring havoc in case of an attack or unintentional error.
Network security management, one of the main security categories of ISO 27001, states as its objective “to ensure the protection of information in networks and its supporting information processing facilities.” To achieve the stated objective, one of its proposed controls is A.13.1.3 – Segregation in networks, and in this article, we will review its recommendations detailed in ISO 27002. We will also answer the questions about why network segregation is important and what its benefits are, and learn more about network segregation vs. segmentation in ISO 27001.
Network segregation is the act of splitting a network into smaller parts called subnetworks or network segments. It is another good example of application of the strategy “Divide and Conquer” we saw in the article ISO 27001 project management: Implementing complex security controls using Work Breakdown Structure (WBS).
Reviewing the house / office example, you can think of segregation as rooms like a living room, dining room, meeting room, archive room, etc. The most important thing here is thinking about spaces reserved for specific purposes.
The segregation of networks is important, because you will not want anyone to reach your system and have access to your files – hostile or accidental. To minimize the impact of such network intrusion, it should be difficult for the intruder to move undetected around the network and to access your information. Segregation is about identifying which systems you use and determining which networks need isolating. For example, you may have sensitive data, such as your organization’s financial records and business process workflows. These files do not need to be stored in the location where you process customer inquiries. Instead, you place them in another room in the network, and you define access rules for devices that are used only by managers of related departments.
Another scenario: Think of a hacker who wants to access your sensitive information, hosts, and services. This hacker may seek to create a remote connection to a server, use legitimate network admin tools, and execute a malicious code on that server. A well-planned network segmentation comes handy here, being a key security measure for preventing such activities from occurring. In this case, segregating the network and disallowing remote desktop connections or the use of admin tools from user computers, as well as configuring servers to limit the sharing of files, will be helpful.
Network segregation according to ISO 27001 also helps information security personnel with their jobs. With the rules determined, a segregated environment will allow them to establish better auditing and alerting strategies for attacks. They could identify a network intrusion and timely response to incidents.
Let’s learn more about the benefits of network segregation in ISO 27001.
Enhanced performance: with fewer hosts per subnetwork, there is less signaling traffic, and more bandwidth can be used for data communication.
Improved security: with less signaling traffic going through all network segments, it is more difficult for an attacker to figure out the network structure, failures in one segment are less likely to propagate, and better access control can be established considering visitors’ access or access to sensitive information / assets.
On the other hand, the segregation effort requires:
Specialized knowledge: networks may house hundreds of devices, with organizations defining complex policies with dozens of rules, so the network staff must be properly educated and trained to ensure the network segmentation keeps the business working securely and in compliance.
Administrative effort: changes in infrastructure, like new business applications and new technologies, can multiply the time required to make proper changes and ensure the integrity of network segments.
Investments in equipment / software: segregation may require more equipment, new equipment with advanced functionalities, or specific software to deal with multiple segments, and those requirements should be considered during budget planning.
Control A.13.1.3 – Segregation in networks, states that groups of information services, users, and information systems should be segregated on networks. ISO 27002, which provides guidance on ISO 27001 controls implementation, make some recommendations:
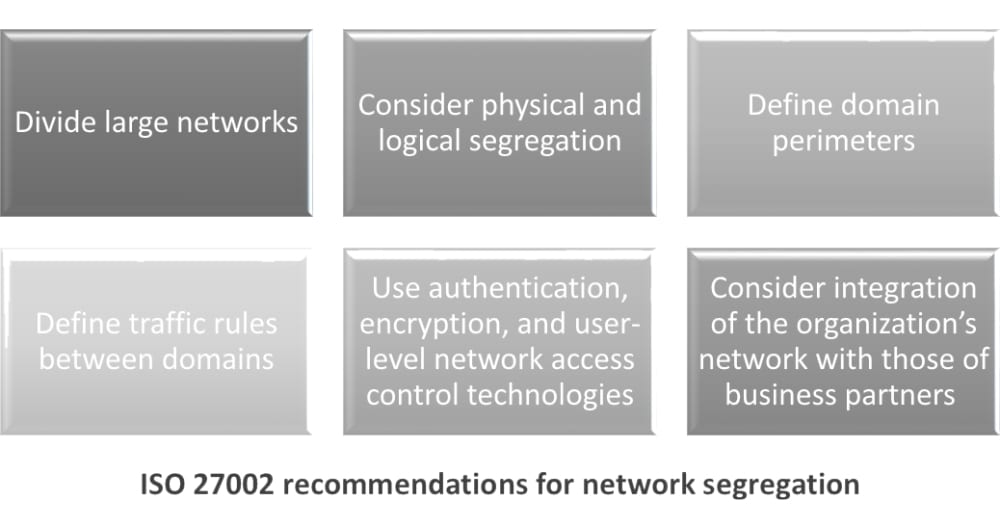
To fulfill the recommendations for network segregation, you can consider the following models for network segmentation:
Criteria-based segmentation: Pre-defined rules to establish perimeters and create new segments can reduce future administration efforts. Examples of criteria are trust level (e.g., external public segment, staff segment, server segment, database segment, suppliers segment, etc.), organizational unit (e.g., HR, Sales, Customer Service, etc.), and combinations (e.g., external public access to Sales and Customer Service).
Use of physical and logical segmentation: Depending upon the risk level indicated in the risk assessment, it may be necessary to use physically separated infrastructures to protect the organization’s information and assets (e.g., top-secret data flowing through a fiber dedicated to management staff), or you may use solutions based on logical segmentation like Virtual Private Network (VPN).
Access rules for traffic flowing: Traffic between segments, including those of allowed external parties, should be controlled according to the need to transmit/receive information. Gateways, like firewalls and routers, should be configured based on information classification and risk assessment. A specific case of access control applies to wireless networks, since they have poor perimeter definition. The recommendation is to treat wireless communication as an external connection until the traffic can reach a proper wired gateway before granting access to internal network segments.
Single networks for startups or small businesses may seem like a good deal, and in most cases, they are. They are easy to manage and save money needed to keep the business going. However, you must think like a strategic manager, and differentiate yourself from ordinary managers by thinking ahead, by being ready to evolve your network when it begins to represent a drawback to business.
You do not need to implement segregation of networks at the beginning of your new business, but if you believe your business will be successful, you must be prepared.
To learn how to become compliant with every clause and control from Annex A, and to get all the required policies and procedures for controls and clauses, sign up for a free trial of Conformio, the leading ISO 27001 compliance software.