 Rhand Leal
Rhand Leal
August 23, 2016
Implementation, maintenance, training, and knowledge products for Information Security Management Systems (ISMS) according to the ISO 27001 standard.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
All required policies, procedures, and forms to implement an ISMS according to ISO 27001.
Train your key people about ISO 27001 requirements and provide cybersecurity awareness training to all of your employees.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance and training products for critical infrastructure organizations for the European Union’s Network and Information Systems cybersecurity directive.
All required policies, procedures, and forms to comply with the NIS 2 cybersecurity directive.
Company-wide training program for employees and senior management to comply with Article 20 of the NIS 2 cybersecurity directive.
Compliance and training products for financial entities for the European Union’s DORA regulation.
All required policies, procedures, and forms to comply with the DORA regulation.
Company-wide cybersecurity and resilience training program for all employees, to train them and raise awareness about ICT risk management.
Accredited courses for individuals and DORA professionals who want the highest-quality training and certification.
Compliance and training products for personal data protection according to the European Union’s General Data Protection Regulation.
All required policies, procedures, and forms to comply with the EU GDPR privacy regulation.
Train your key people about GDPR requirements to ensure awareness of data protection principles, privacy rights, and regulatory compliance.
Accredited courses for individuals and privacy professionals who want the highest-quality training and certification.
Implementation, training, and knowledge products for Quality Management Systems (QMS) according to the ISO 9001 standard.
All required policies, procedures, and forms to implement a QMS according to ISO 9001.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for Environmental Management Systems (EMS) according to the ISO 14001 standard.
All required policies, procedures, and forms to implement an EMS according to ISO 14001.
Accredited courses for individuals and environmental professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 14001 and the EMS using Advisera’s proprietary AI-powered knowledge base.
Implementation and training products for Occupational Health & Safety Management Systems (OHSMS) according to the ISO 45001 standard.
All required policies, procedures, and forms to implement an OHSMS according to ISO 45001.
Accredited courses for individuals and health & safety professionals who want the highest-quality training and certification.
Implementation and training products for medical device Quality Management Systems (QMS) according to the ISO 13485 standard.
All required policies, procedures, and forms to implement a medical device QMS according to ISO 13485.
Accredited courses for individuals and medical device professionals who want the highest-quality training and certification.
Compliance products for the European Union’s Medical Device Regulation.
All required policies, procedures, and forms to comply with the EU MDR.
Implementation products for Information Technology Service Management Systems (ITSMS) according to the ISO 20000 standard.
All required policies, procedures, and forms to implement an ITSMS according to ISO 20000.
Implementation products for Business Continuity Management Systems (BCMS) according to the ISO 22301 standard.
All required policies, procedures, and forms to implement a BCMS according to ISO 22301.
Implementation products for testing and calibration laboratories according to the ISO 17025 standard.
All required policies, procedures, and forms to implement ISO 17025 in a laboratory.
Implementation products for automotive Quality Management Systems (QMS) according to the IATF 16949 standard.
All required policies, procedures, and forms to implement an automotive QMS according to IATF 16949.
Implementation products for aerospace Quality Management Systems (QMS) according to the AS9100 standard.
All required policies, procedures, and forms to implement an aerospace QMS according to AS9100.
Implementation, maintenance, training, and knowledge products for consultancies.
Handle multiple ISO 27001 projects by automating repetitive tasks during ISMS implementation.
All required policies, procedures, and forms to implement various standards and regulations for your clients.
Grow your business by organizing cybersecurity and compliance training for your clients under your own brand using Advisera’s learning management system platform.
Accredited Lead Auditor and Implementer courses for DORA and ISO standards and advanced courses to help consultants grow their business, increase recurring revenue, and stand out from bigger competitors.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Find new clients, potential partners, and collaborators and meet a community of like-minded professionals locally and globally.
Implementation, maintenance, training, and knowledge products for the IT industry.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), NIS 2 (critical infrastructure cybersecurity), and DORA (cybersecurity for financial sector).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance, training, and knowledge products for essential and important organizations.
Documentation to comply with NIS 2 (cybersecurity), GDPR (privacy), ISO 27001 (cybersecurity), and ISO 22301 (business continuity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for manufacturing companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for transportation & distribution companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for schools, universities, and other educational organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for telecoms.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for banks, insurance companies, and other financial organizations.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with DORA (cybersecurity for financial sector), ISO 27001 (cybersecurity), ISO 22301 (business continuity), and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for local, regional, and national government entities.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for hospitals and other health organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the medical device industry.
Documentation to comply with MDR and ISO 13485 (medical device), ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the aerospace industry.
Documentation to comply with AS9100 (aerospace), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the automotive industry.
Documentation to comply with IATF 16949 (automotive), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for laboratories.
Documentation to comply with ISO 17025 (testing and calibration laboratories), ISO 9001 (quality), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
 Rhand Leal
Rhand Leal
Cloud solutions are attractive answers for those who look for cost savings and quick demand response infrastructure, and Internet searches can show you how these kinds of solutions are rapidly growing and being adopted by organizations of all sizes, especially by small and medium-sized organizations.
However, their very nature requires customers and providers to share management and operational activities to some extent, and the lack or failure to observe the responsibilities regarding these activities may bring significant damage to interested parties.
This article will present how information security activities should be viewed in cloud environments and how ISO 27001 and ISO 27017 (a code of practice for information security for cloud services) can help organizations to properly define responsibilities in cloud environments and ensure information protection.
Before an information security assessment can be made, we must first understand how cloud services may be provided to customers. The most common cloud service models available in the market, in order of increasing complexity, are:
Infrastructure as a Service (IaaS): model that offers only basic computing infrastructure (e.g., physical and virtual machines, location, network, backup, etc.).
Platform as a Service (PaaS): model that offers, beyond computing infrastructure, a development environment for application developers (e.g., operating systems, programming-language execution environment, databases, etc.).
Software as a Service (SaaS): model that offers to final users access to application software and databases (e.g., email, file sharing, social networks, ERPs, etc.).
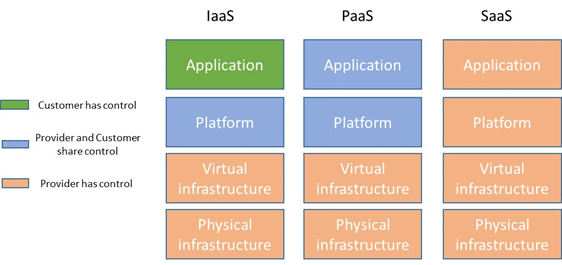
Note that, as complexity increases from IaaS to SaaS, the assets under the control of the organization start to go under the control of the provider; however, in terms of information security, some activities must still remain under the control of the customer organization, as we will see in the next section.
From an information security point of view, the main concerns involving the above-mentioned cloud models, and what you should have the common sense to consider in terms of security, are:
Information classification, labeling, and handling. The data stored and processed in provided cloud environments ultimately belong to, or are under the responsibility of, the customer organization, so the final decision about how they must be classified, labeled, and handled must always be made by the customer. So, even if all assets are under the control of the provider, like in the SaaS model, is a good thing that its responsibility regarding information security covers only the implementation of the controls related to the classification given by the customer organization.
Identity management. In PaaS and SaaS models, depending upon the information system considered (e.g., an ERP), users’ groups may be divided into users required to maintain the running of the system (operational activities), often under the provider’s control; and users required to manage access to systems’ functionalities (e.g., ERP’s financial and HR functions) and final users, these last two often under the customer organization’s control. So, in a similar system, it is a good thing to maintain strict control over which users can belong to which groups.
Monitoring. Regardless of the cloud model adopted, monitored data can be related to assets’ performance (e.g., bandwidth, throughput, etc.) or data processing (e.g., registries accessed, users’ activities, user login time, etc.), and in the latter case, sensitive information may be compromised through monitored data, so it is a good thing to define which data the provider can monitor and which data must be made available only to the customer organization.
Privacy. This is perhaps the most critical information security aspect related to cloud services adoption, since the service provider, by controlling the basic infrastructure, can access all data that are in the cloud at any time. Besides that, the locations from where the cloud provider operates may have laws and regulations that can pose risk to information confidentiality.
The “commons sense” we saw in the previous section is already considered in a formal way in ISO security standards. While ISO 27001 provides controls to ensure proper responsibilities definition regarding information security (e.g., A.6.1.1 – Information security roles and responsibilities and A.6.1.2 – Segregation of duties), ISO 27017 offers an integrated view, considering how customers and providers should approach the same control. See this article: ISO 27001 vs. ISO 27017 – Information security controls for cloud services.
So, considering this integrated view, the standard’s general recommendations about shared responsibilities in cloud environments can be described as:
Security policies: Customer organizations should state the cloud service’s relevance to its business activities and information security processes, and providers should state that cloud service customers’ requirements should be considered in the management of its own information security processes.
Contractual clauses: Customer organizations should include clauses in cloud SLAs regarding information security aspects to be fulfilled by the provider. These clauses should cover the organization’s requirements as well as those of its own clients, including privacy concerns. Providers should include clauses in their contracts with customers clearly specifying the capabilities they can offer regarding cloud services provided, and privacy-related information (e.g., where the provider operates and with which laws and regulations they must comply).
Access control and monitoring: Providers should make available functionalities to allow customers to manage, control, and monitor functionalities by themselves, without depending on the provider’s intervention (e.g., defining information classification, managing users, and monitoring resources performance).
Cloud services benefits have enabled many organizations, especially those with limited resources, to expand their activities and improve their chances of success, and it would be terrible to see all efforts compromised because of something so simple as failure to resolve responsibilities definition.
ISO 27001 and ISO 27017 controls and recommendations can be used to establish clear responsibilities for both providers and customers, minimizing the risks that undefined responsibilities may lead to information compromising and failure to achieve business objectives.
To implement ISO 27001 & ISO 27017 & ISO 27018 easily and efficiently, use our ISO 27001 & ISO 27017 & ISO 27018 Cloud Documentation Toolkit that provides step-by-step guidance and all documents for full ISO 27001 & ISO 27017 & ISO 27018 compliance.

Rhand Leal has more than 15 years of experience in information security, and for six years he continuously maintained а certified Information Security Management System based on ISO 27001.
Rhand holds an MBA in Business Management from Fundação Getúlio Vargas. Among his certifications are ISO 27001 Lead Auditor, ISO 9001 Lead Auditor, Certified Information Security Manager (CISM), Certified Information Systems Security Professional (CISSP), and others. He is a member of the ISACA Brasília Chapter.

You may unsubscribe at any time. For more information, please see our privacy notice.