The NIST Cybersecurity Framework offers a comprehensive framework for managing cybersecurity, regardless of industry, organizational size, or current cybersecurity maturity level. But just because it’s not mandatory (for most) doesn’t mean that it should be dismissed. Cybersecurity threats are everywhere, and an attack could leave your systems compromised and bring your operations to a halt. The NIST CSF advocates a preventative, proactive approach to dealing with threats. Here’s everything you need to know about how to implement it.
The NIST CSF can be used at all levels inside an organization to manage cybersecurity risks, and to seamlessly integrate with other practices, frameworks, and standards. Understanding its structure — including the Core, Profiles, and Tiers — and how to use it helps organizations protect their network security, detect vulnerabilities, and develop system contingencies.
What is the NIST CSF?
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is a framework for managing cybersecurity risks. The latest update of the CSF (edition 2.0) was made on February 26, 2024, and it provides guidance to understand, assess, prioritize, and communicate an organization’s cybersecurity efforts relating to:
- Data protection
- Network security
- Incident response
- Vulnerability detection
- System recovery
Anyone with a digital online presence can use the CSF. It’s not region-specific, nor is it only applicable to certain industries or large organizations.
That said, in the U.S., Executive Order 13800 (Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure) made the NIST CSF mandatory for federal government agencies. However, it’s not mandatory for other U.S. and non-U.S. organizations.
What does NIST CSF 2.0 consist of?
NIST CSF 2.0 consists of several elements, most notably the CSF Core, which outlines the fundamental cybersecurity activities and outcomes that organizations should focus on to strengthen their cybersecurity.
In addition to the Core, there are Profiles and Tiers, both of which serve to compare and analyze gaps between an organization’s current cybersecurity status versus where it intends to be.
The CSF Core groups cybersecurity objectives into six “Functions” (further detailed in “Categories” and “Subcategories”):
- Govern (GV) – Establishing cybersecurity risk strategy, policies, and monitoring.
- Identify (ID) – Ensuring understanding of the organization’s risks, assets, and suppliers.
- Protect (PR) – Implementing measures to handle cybersecurity risks.
- Detect (DE) – Detecting cybersecurity incidents or compromises.
- Respond (RS) – Managing, analyzing, mitigating, and reporting cybersecurity incidents.
- Recover (RC) – Restoration of operations and assets post-cybersecurity incident.
Functions are at the top of the hierarchy and encompass broad cybersecurity objectives. Categories branch off from Functions, representing more detailed cybersecurity outcomes. Further down the hierarchy, Subcategories provide granular technical and management descriptions.
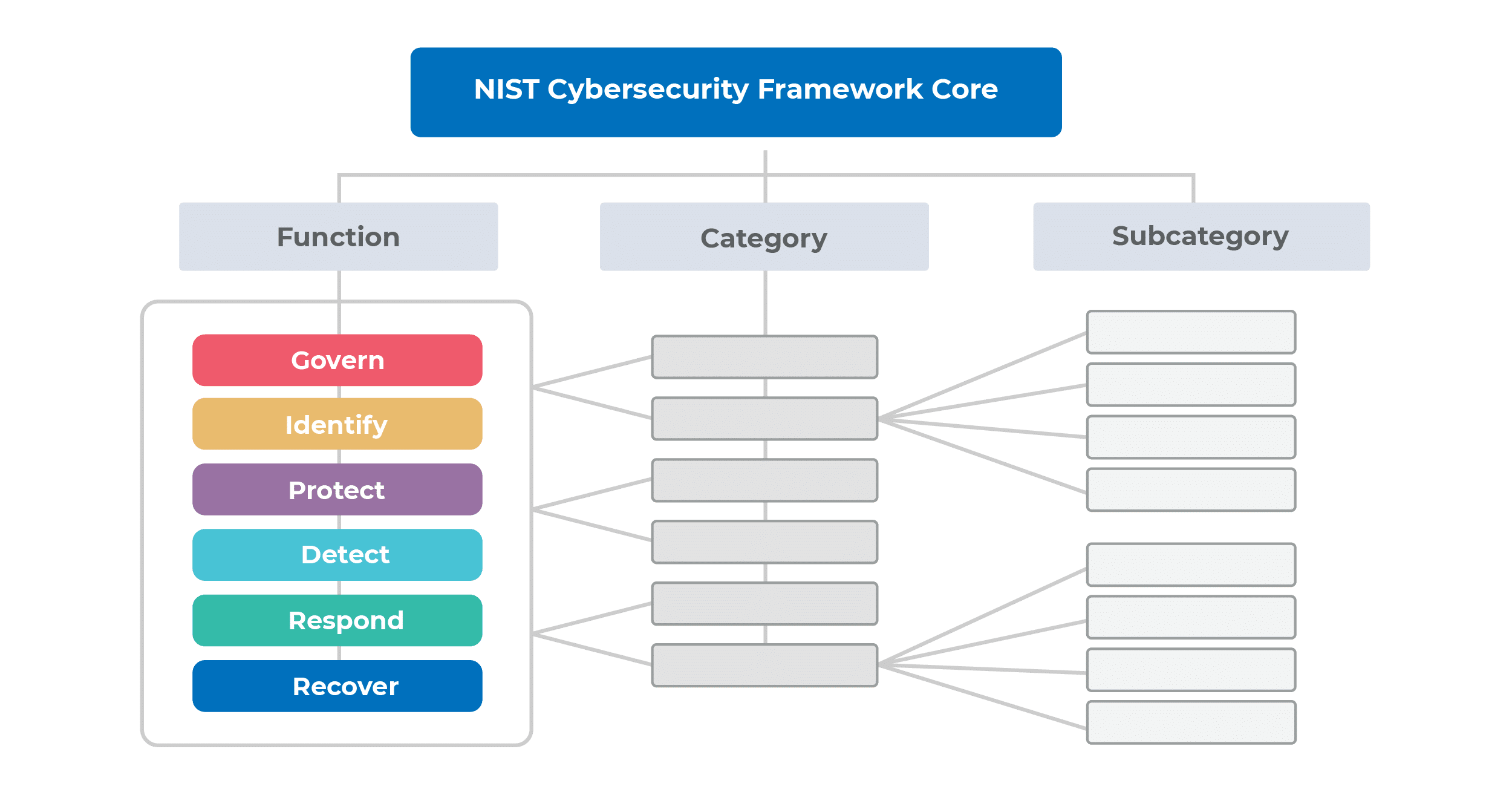
The arrangement and magnitude of Functions, Categories, and Subcategories in the CSF Core do not suggest a particular order or level of significance.
CSF Core contains, as the name implies, core elements needed for implementation. Here’s a quick example of CSF Core mapping and how it illustrates specific Functions, Categories, and Subcategories:
- Function – Protect (PR): Safeguards to mitigate the organization’s cybersecurity risks.
- Category – Awareness and Training (PR.AT): Cybersecurity awareness and training for all personnel.
- Subcategory – Awareness and Training (PR.AT-01): Training using security tools and resources, covering phishing awareness, password management, and data-handling practices.
Once all the known outcomes have been mapped, an organization can proceed to mitigate these actions. In the above example, they could:
- Provide continuous cybersecurity awareness and training to internal stakeholders.
- Periodically assess or test users on their understanding of basic cybersecurity practices.
- Regularly monitor and assess the effectiveness of mitigation actions.
| The content of the NIST CSF 2.0 Core | ||
| Cybersecurity Framework Core | Functions | 6 |
| Categories | 22 | |
| Subcategories | 106 | |
| Implementation example | 363 | |
CSF organizational profiles
When the CSF Core has been fully mapped out, the organization should then complete a CSF organizational profile to illustrate their existing or desired cybersecurity status.
- Current profiles outline the cybersecurity outcomes already achieved.
- Target profiles define the desired cybersecurity outcomes.
An organizational profile can be documented in any worksheet or using a word processor. Whatever your preferred method, the comparison should include the following elements for both the current and target profile for each CSF outcome:
- Priority levels
- Outcome status
- Policies and procedures
- Internal practices
- Roles and responsibilities
By comparing current and target profiles, organizations can pinpoint areas needing improvement and develop action plans to address these gaps. This allows for prioritizing actions based on business needs and risk management strategies, targeting specific Categories or Subcategories.
CSF Tiers
Once the current and target organizational profiles have been established, an organization should then use CSF Tiers to rank the thoroughness of its cybersecurity risk governance and management practices captured within the profiles.
- Partial (Tier 1) – Risks are managed in an ad hoc manner.
- Risk Informed (Tier 2) – Management approves risk management practices, but they may not be formalized as policy across the entire organization.
- Repeatable (Tier 3) – The organization’s risk management practices are officially approved and established as formal policies.
- Adaptive (Tier 4) – The organization employs a comprehensive strategy to manage cybersecurity risks, utilizing policies and procedures that are informed by risk assessments.
Advancement to higher Tiers happens when there are increased risks, or when a cost-benefit analysis suggests that moving up a Tier could reduce cybersecurity risks.
How is NIST CSF 2.0 related to ISO 27001?
Although NIST CSF 2.0 doesn’t explicitly mention ISO 27001, they are related in many areas, meaning they can mutually support the implementation of one another. Here are the common areas of the NIST CSF and ISO 27001:
| NIST CSF 2.0 Reference | ISO 27001 Reference | |
| Roles, Responsibilities, and Authorities | Roles, Responsibilities, and Authorities (GV.RR): Cybersecurity roles, responsibilities, and authorities to foster accountability, performance assessment, and continuous improvement are established and communicated. | Clause 5.3 Organizational roles, responsibilities and authorities |
| Risk Assessment | Risk Assessment (ID.RA): The cybersecurity risk to the organization, assets, and individuals is understood by the organization. | Clause 6.1.2 Information security risk assessment |
| Awareness and Training | Awareness and Training (PR.AT): The organization’s personnel are provided with cybersecurity awareness and training so that they can perform their cybersecurity-related tasks. | Clause 7.2 Competence |
| Monitoring and Measurement | Continuous Monitoring (DE.CM): Assets are monitored to find anomalies, indicators of compromise, and other potentially adverse events. | Clause 9.1 Monitoring, measurement, analysis and evaluation |
| Incident Response | Incident Management (RS.MA): Responses to detected cybersecurity incidents are managed. | Control A.5.26 Response to information security incidents |
| Disaster Recovery | Incident Recovery Plan Execution (RC.RP): Restoration activities are performed to ensure operational availability of systems and services affected by cybersecurity incidents | Control A.5.29 ICT readiness for business continuity |
ISO 27001’s structured risk management complements the NIST CSF’s Identify function, offering a method to assess and treat identified risks. But what about certification? Some organizations need to ensure that they’re following stringent protocols and promoting best practices.
NIST CSF certification
NIST does not provide official certifications for products, implementations, or services related to the Cybersecurity Framework. Complying with the CSF is a voluntary practice, except for U.S. federal government agencies.
Even though organizations cannot be certified in the NIST CSF, there are several compelling reasons to implement it:
- Improved cybersecurity posture – The NIST CSF enhances the organization’s cybersecurity practices and resilience.
- Enhanced risk management – A risk-based approach to managing cybersecurity threats is central to the framework.
- Improved communication and collaboration – There is a common approach to cybersecurity risks and responsibilities between internal and external stakeholders.
- Continual improvement – Regular review and updates of the organization’s security practices offer opportunities for improvement.
Conclusion
The systematic and logical approach of NIST CSF 2.0 through the cascade of Functions, Categories, and Subcategories ensures a comprehensive approach to cybersecurity. Yet, focusing on outcomes rather than processes and related activities defines what needs to be done, leaving enough space for each organization to easily define how to approach cybersecurity on its own.
Download a free preview of the ISO 27001 Documentation Toolkit to see the structure for each document mentioned above.


 Branimir Valentic
Branimir Valentic