Today’s business processes require faster responses and greater productivity, and sometimes they involve a lot of monotonous and repetitive work. To minimize the risks of error or failure related to such conditions, the automation of certain activities should be carefully considered by organizations.
In this article, you’ll learn how to consider what can be automated during the implementation, operation, and maintenance of security policies based on ISO 27001, the leading ISO standard for information security.
- Purpose;
- Scope of the application;
- Audience;
- Definition;
- Means of communication;
- Means of implementation and enforcement;
- Performance evaluation;
- Evidence of application and results;
- Review.
What is a security policy, and why do you need it?
You can think of a security policy as a set of rules and guidelines to define the expected behavior of people and systems, as well as constraints to prevent unexpected, undesired, or unauthorized behavior.
Security policies are needed to address risks or to ensure compliance with legal requirements (e.g., laws, regulations, or contracts). Additionally, security policies and procedures are used to standardize the activities to be performed, i.e., to define rules of behavior with regards to security.
For example, to address risks related to compromised passwords, or to fulfill a contractual clause with a customer, a password policy can set rules for the definition of passwords that are hard to crack, periodic password changes, and account locking after a number of unsuccessful access attempts.
What is included in a security policy?
A robust security policy should include at least the following elements:
- Clear purpose (e.g., treat risks, fulfill legal requirements, etc.);
- Clear scope of application (e.g., department, process, building, etc.);
- Clear audience (e.g., management, technical staff, end users, etc.);
- Clear definition of roles, responsibilities, and authorities for all people involved with and affected by it (e.g., management, technical staff, end users, etc.);
- Means for it to be communicated to all relevant parts (e.g., by use of newsletters, presentations, trainings, etc.);
- Means for it to be implemented and enforced within all necessary elements (e.g., people, systems, facilities, etc.) in its scope of application (see details in the next section);
- Means to evaluate its performance (e.g., by use of key performance indicators, monitoring, and measurement);
- Means to provide evidence of its application and results (e.g., use of logs and reports);
- Means to ensure its review (e.g., by time, by event, etc.).
These elements can help a security policy to fulfill its intended purposes and remain fit for use, and some of them are good candidates for automation, contributing to reducing the administrative effort and cost for security policy management.
How are security policies implemented?
Security policies are implemented effectively by means of technical, physical, and/or human-related controls, according to their intended purposes.
Technical controls are primarily implemented in information systems, by means of software, hardware, and firmware components added to systems, e.g., backup, antivirus software, etc.
Physical controls are primarily implemented by means of equipment or devices that have a physical interaction with people and objects, e.g., CCTV cameras, alarm systems, locks, etc.
Human resource controls are implemented by means of awareness, training, and education activities, e.g., security awareness training, ISO 27001 internal auditor training, academic education, etc.
The monitoring and measurement of such controls are key elements to evaluate a security policy’s performance, and both activities are good candidates for automation.
ISO 27001 security policy automation with Conformio
Conformio is Advisera’s Software-as-a-Service solution for the implementation and operation of an ISO 27001 Information Security Management System (ISMS). Its policy automation features are defined during Conformio’s first setup and with subsequent data entry, guided by one of Conformio’s document wizards, which can assist with security policy automation and policy management in the following ways:
Purpose: Conformio uses the information you previously provided about risks, laws, regulations, and contracts to automatically suggest policies and procedures that can help you fulfill them.
Scope of application: Business units you create in Conformio are automatically suggested by the Document Wizard to be included in the scope of policies or procedures that may be related to them.
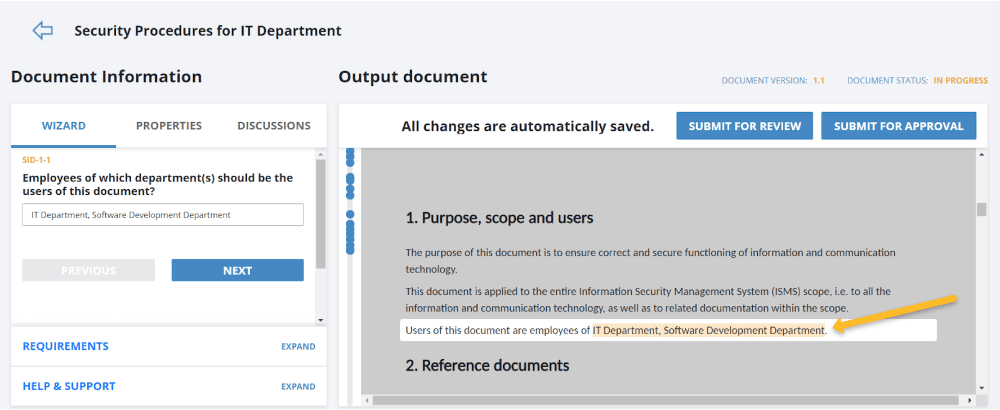
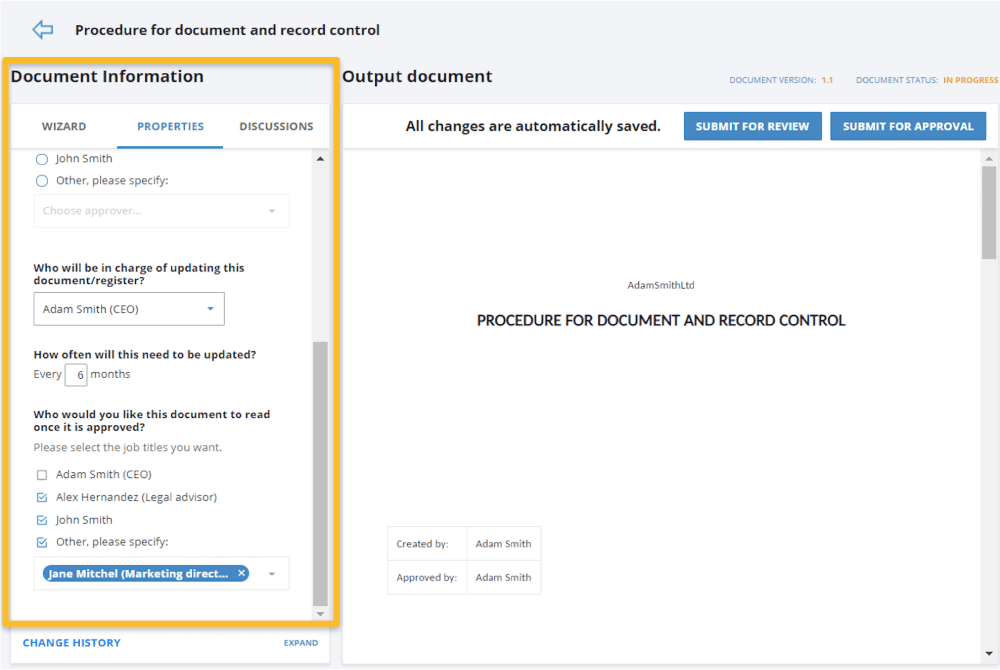
Audience: During policy elaboration, you can identify which persons need to be made aware of the policy, and they will be automatically informed via email when the policy is released.
Figure 3 – Identification of users that need to be made aware of documents.
Roles, responsibilities, and authorities: Roles you create for security management are automatically available when you need to define who needs to perform an activity or make a decision.
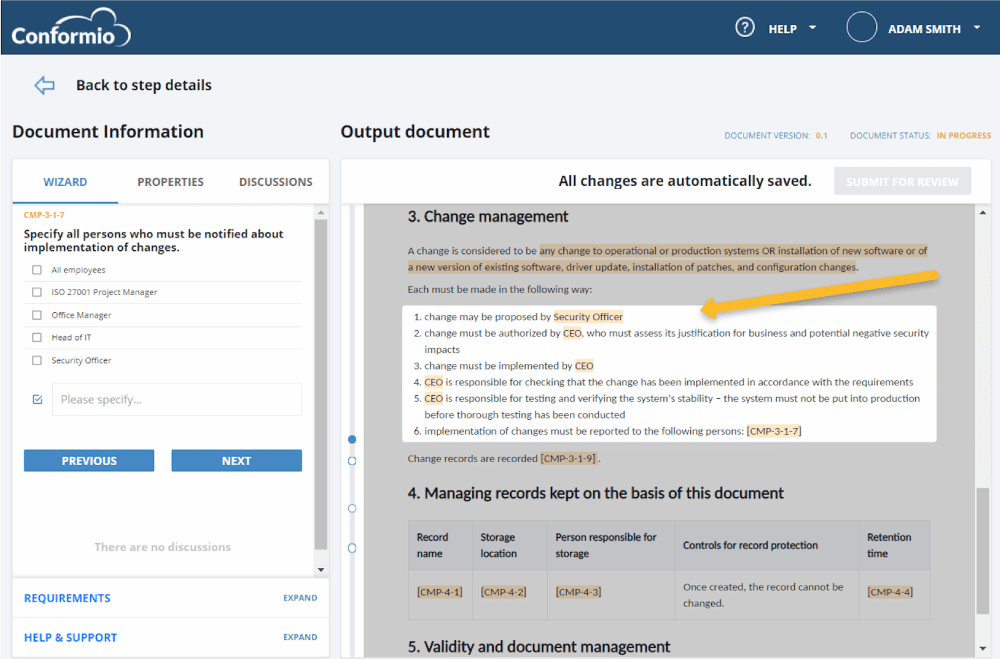
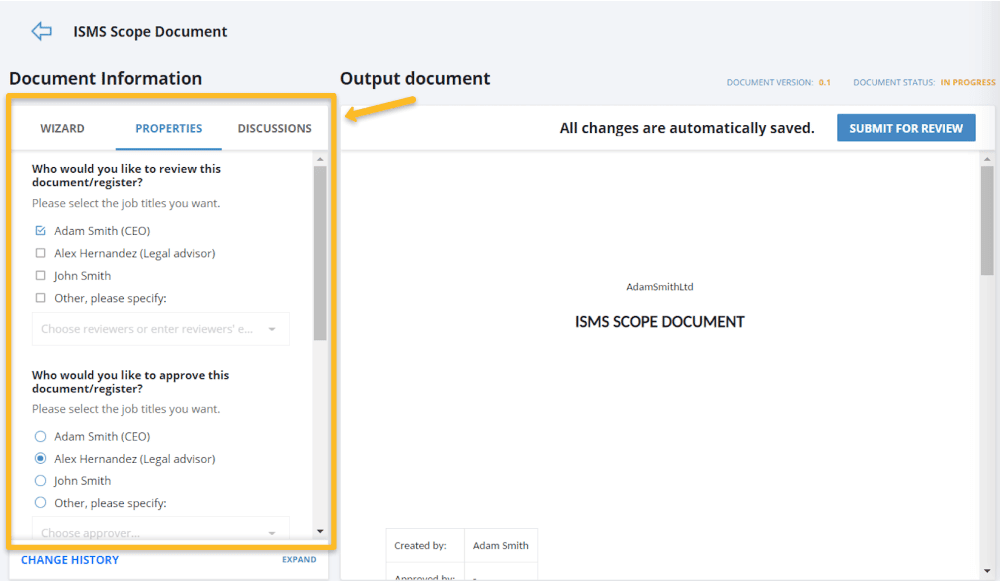
Means of communication: Once a policy is under review or approval, involved persons will be automatically notified via email when they need to take action.Once a policy is released, all personnel identified as needing to be aware of it (see Figure 3) will be notified automatically.
Means of implementation and enforcement: When the policy is being developed, Conformio will show sections where you define specific roles and tasks regarding how the policy will be implemented.
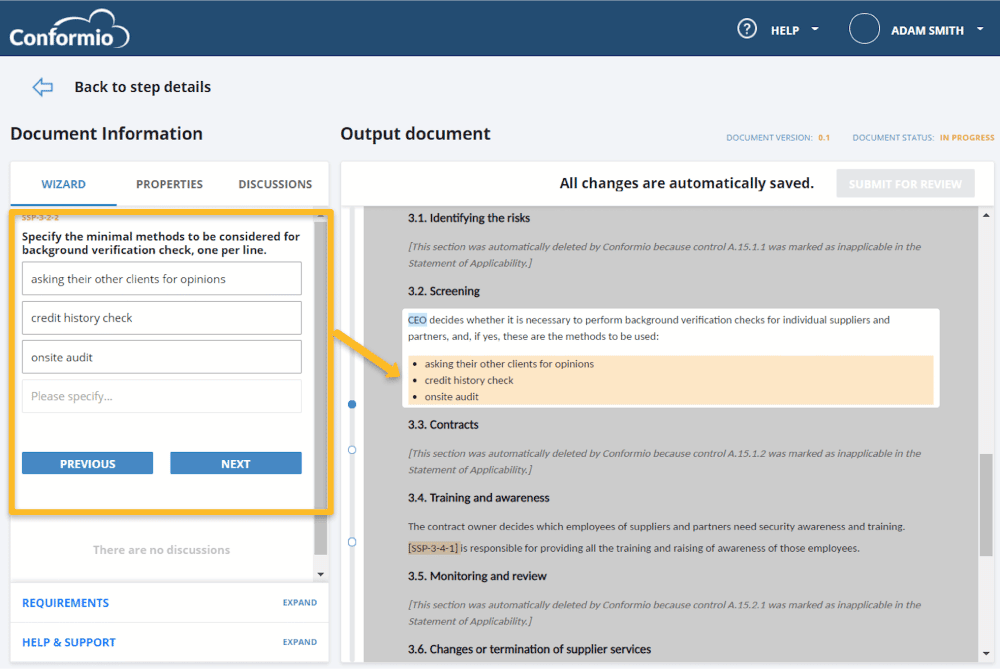
Regarding documentation, once a policy is released, relevant staff members will be notified and will need to acknowledge their understanding of the policy content.
Performance evaluation: Conformio helps you define key performance indicators and audit programs, and reminders for such actions, to help you monitor and measure implementation, as well as check its conformance. Gathered data is used to automatically generate reports to help you analyze, evaluate, and present information to decision makers.
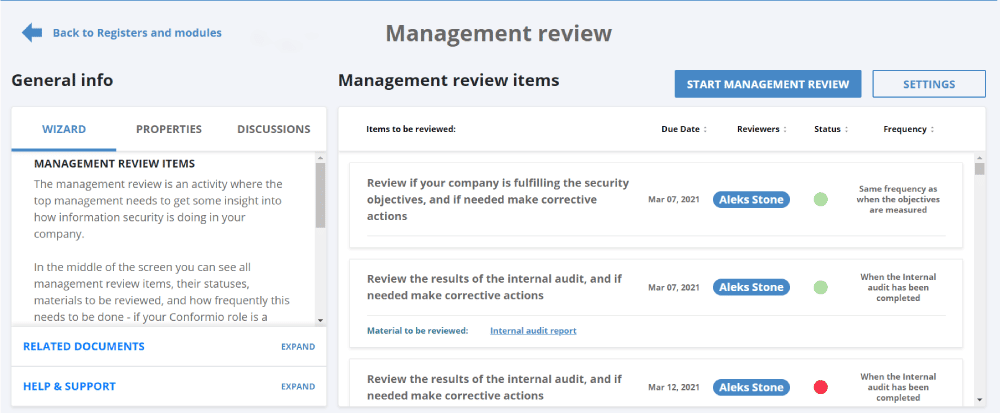
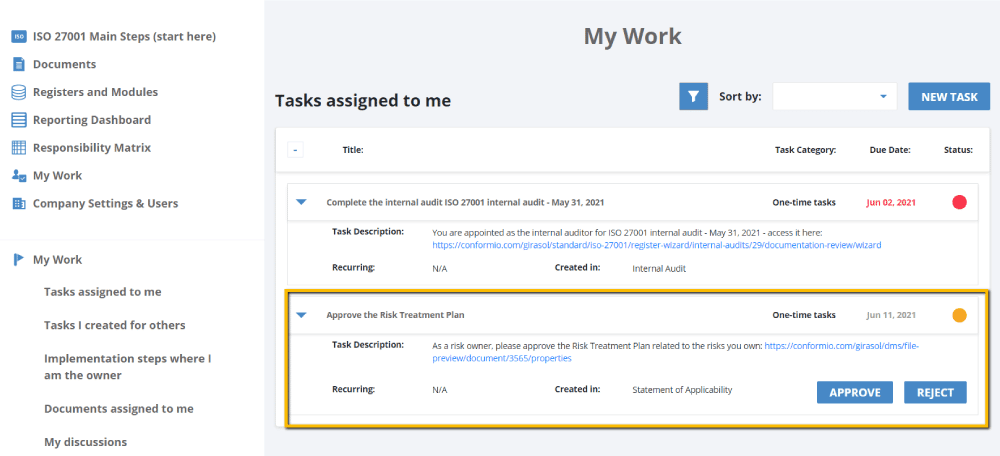
Evidence of application and results: The activities performed, and the results achieved (e.g., the risk assessment and treatment report, as well as the risk treatment plan, are expected results of performing risk assessment and risk treatment) are automatically recorded, and reminders for when an action is required from you will make it easier for you to have all the evidence you need.
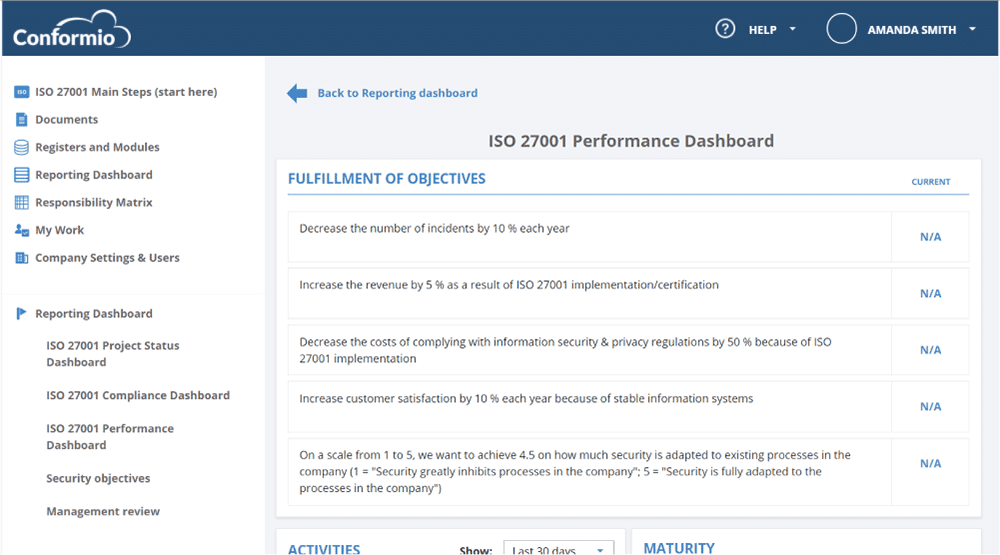
Review: Dashboards and reports based on gathered data will make it easier and faster to present information to decision makers about the conformance of policies and the results achieved.
Improve quality and speed of results through automation
As you can see, the management of security policies involves lots of activities like data gathering, data analysis, writing, coordinating, reviewing, approving, and distribution of the documents – all of these can be quite frustrating.
By automating the security policy, you keep people away from the tedious activities related to document development and management, and closer to where they can add more value: identifying how security policies can better support the business and protect the organization’s assets.
To get the templates for all mandatory documents and the most common non-mandatory documents, along with the wizard that helps you fill out those templates, sign up for a 14-day free trial of Conformio, the leading ISO 27001 compliance software.

 Rhand Leal
Rhand Leal