Just like your need to implement access control to your sensitive information throughout the company, you also need to control access to the information related to your ISO 27001 project. In such a project, there are several people with different needs, lots of tasks and activities, and many types of information shared. It can easily become a mess, and information that should be kept only by a few people ends up becoming common knowledge, causing the system to be burdened with problems to be dealt with.
In this article, you will learn how Conformio, a Software-as-a-Service for implementation and maintenance of an ISO 27001 Information Security Management System (ISMS), can be used to implement access control and access rights management during the implementation project.
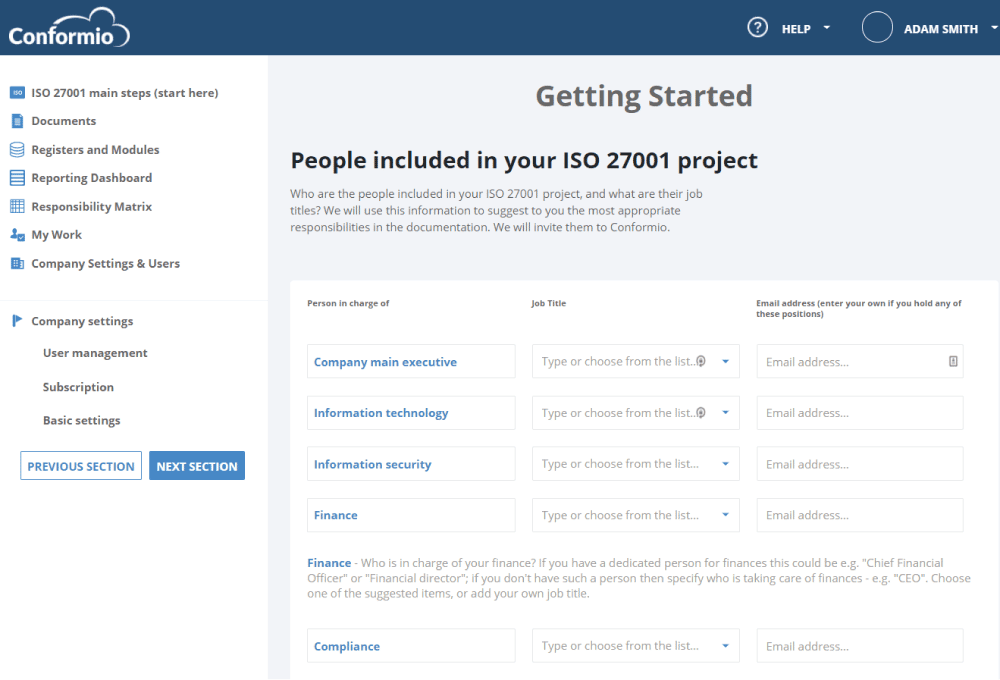
What user profiles would typically participate in an ISO 27001 project?
In an ISO 27001 project, you will normally find these kinds of user profiles:
Managers: people with authority over project results, resource allocation, documentation approval, and conflict resolution. Common organizational roles with this profile are the Chief Executive Officer (when the ISMS scope includes the entire organization), department heads, and the Chief Financial Officer (when this role is the decision maker about financial resource allocation).
Project team: people designated for the coordination and execution of project tasks, elaborating documents, facilitating meetings, and providing training. This can be a team of five, or more persons for bigger or more complex organizations. The organizational roles in this profile will vary depending on the ISMS scope.
Other key employees: people who can affect or be affected by information security activities and who need to be consulted during ISO 27001 implementation. Common roles in this profile are the managers of business units, processes owners, and key users (i.e., people with the most understanding about process execution).
End users: people who need to be aware of the policies, procedures, and controls implemented, so they can perform their activities in a secure manner, as planned.
These general profiles can help define the requirements of access control and access to information.
For more information, see the article RACI matrix for ISO 27001 implementation project.
What are different ways to add users to Conformio?
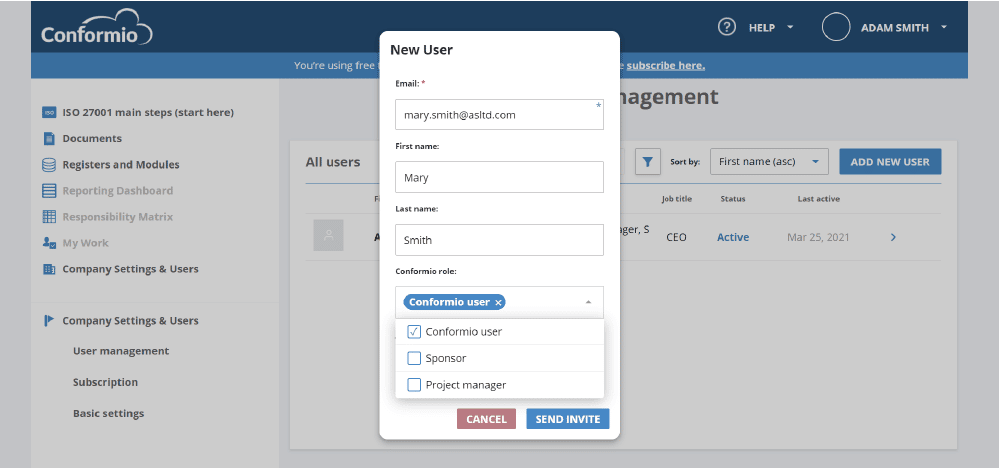
Users can be added to Conformio during platform initial setup, or any time later during Conformio usage.
How often should user access rights be reviewed?
Good practice recommends that user access review be performed either at regular intervals (the more critical the access right, the smaller the interval between reviews) or when a significant situation occurs (e.g., change in employment situation, change in organization’s hierarchical structure, etc.).
During access rights review, the user’s access must be confirmed or updated according to the new conditions, and special care must be taken with privileged access, i.e., access that can change or bypass security controls – for example, admin users.
User access management through Conformio
In Conformio, users’ access can be given at different levels: access to Conformio’s basic settings (e.g., language, time settings, etc.), access to information security processes’ features (e.g., security objectives setting), and access to folders and documents. Access to Conformio’s settings and information security processes’ features can be given during initial setup, or later during the project through its user management screen by updating Conformio user roles.
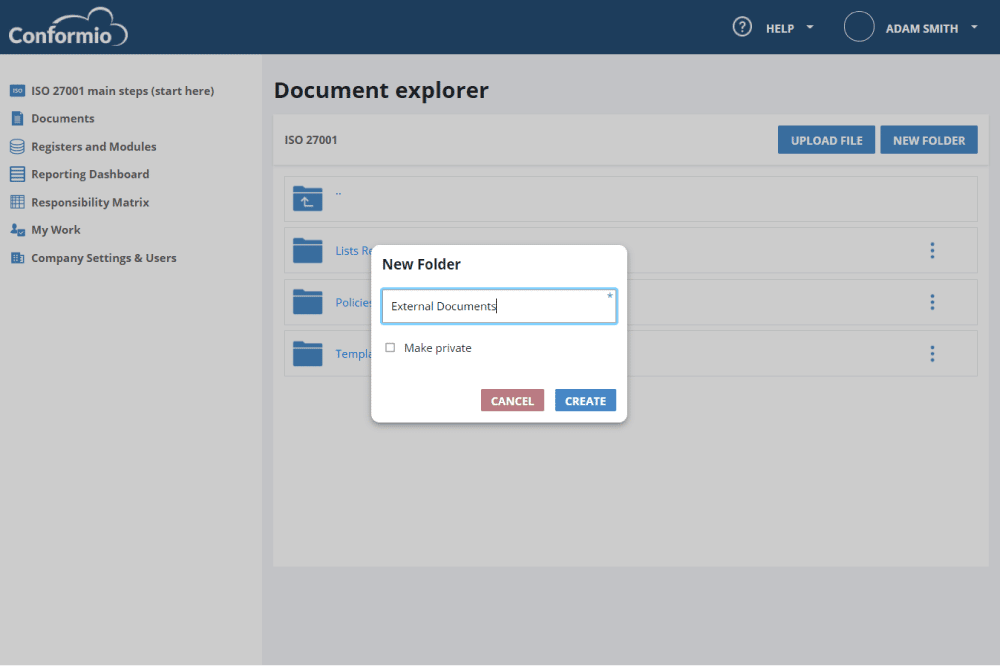
For folders, Conformio offers the ability to create private folders and define who has access to them. Further, you can define which level of access each user has, so if you want to preserve the integrity of files, you can approve only the reading rights. Access to folders and documents can be given at any time through the Document explorer screen.
Information security starts with how you treat the data during the project
Access control is one of the main building blocks of information security, and it must be adopted in its earliest stages of implementation, especially when using software solutions, which makes it easier to communicate and share information.
Considering access management features in the software solution you choose to manage your implementation project (like Conformio) brings at least two benefits. First, you take advantage of lesser management effort needed, provided by automation capabilities, to ensure that information is only seen by those who needs to use it. And second, which would be your greatest asset, you start your information security implementation with a strong message to the organization that information security is to be taken seriously.
To see how employees can collaborate on ISO 27001 ISMS implementation steps, documents, and all the necessary tasks, sign up for a 14-day free trial of Conformio, the leading ISO 27001 compliance software.

 Rhand Leal
Rhand Leal
