 Rhand Leal
Rhand Leal
October 19, 2015
What do diverse situations like the Battle of Trafalgar (1805), the Cooley–Tukey FFT algorithm (1965), and the multi-sided market competition have in common? They are all examples of big or complex problems divided into smaller and more manageable pieces to reach a winning solution. This is a strategy called “Divide and Conquer.”
Like war, signal processing, and marketing competition, information security also deals with a complex situation: protecting information in all its forms and in all locations where it is stored or passes through. In this article, I will present you with a concept based on “divide and conquer” that can be very useful, especially for bigger companies, while implementing ISO 27001 security controls: the Work Breakdown Structure (WBS).
Originating from project management practices, the Work Breakdown Structure (WBS) is defined by the Project Management Body of Knowledge (PMBoK) as “a deliverable-oriented hierarchical decomposition of the work to be executed by the team.”
A deliverable is any tangible or intangible object produced by a project that is intended to be delivered to a customer. Examples of deliverables are a product, a service, or data. Deliverables may be decomposed into multiple smaller deliverables, also called components (e.g., parts of a product, functionalities of a service, or chapters in a report).
Normally, a WBS is presented graphically in the form of a tree of elements, with the main deliverable at the top, the deliverable components in the middle part, and lists of activities to produce the deliverables at the bottom. Another way to present a WBS is as an indented list. See examples of these presentations at the end of the article
In terms of information, deliverables and components are specified in terms of requirements to be fulfilled, while activities are specified in terms of resources needed, like time, equipment, and cost.
In the ISO 27001 security controls context, we can have the following examples of deliverables:
While using a WBS to plan a security control, some rules should be followed to avoid excess or lack of detail, since both can negatively affect the implementation effort:
Some benefits associated with developing a WBS are:
Some problems you must be aware of:
Since nothing is better than a good practical example, let’s see a hypothetical WBS for implementing security controls in an information system:
Here it is in graphic form (actions are identified by the red font):
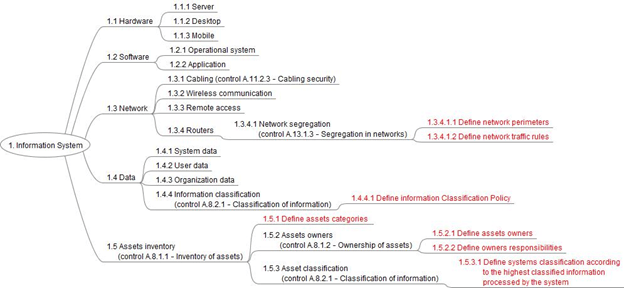
Implementing security may sound like a huge challenge. And it really is, but you don’t need to embrace it all at once. By doing it one piece at a time, you can optimize the effort to ensure each small piece is designed as strong as possible and implemented with all due care, minimizing the chance that all your efforts may be compromised by a situation you could have avoided.
Use this Conformio compliance software to guide you through your ISO 27001 project.