 Antonio Jose Segovia
Antonio Jose Segovia
July 6, 2015
Implementation, maintenance, training, and knowledge products for Information Security Management Systems (ISMS) according to the ISO 27001 standard.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
All required policies, procedures, and forms to implement an ISMS according to ISO 27001.
Train your key people about ISO 27001 requirements and provide cybersecurity awareness training to all of your employees.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance and training products for critical infrastructure organizations for the European Union’s Network and Information Systems cybersecurity directive.
All required policies, procedures, and forms to comply with the NIS 2 cybersecurity directive.
Company-wide training program for employees and senior management to comply with Article 20 of the NIS 2 cybersecurity directive.
Compliance and training products for financial entities for the European Union’s DORA regulation.
All required policies, procedures, and forms to comply with the DORA regulation.
Company-wide cybersecurity and resilience training program for all employees, to train them and raise awareness about ICT risk management.
Accredited courses for individuals and DORA professionals who want the highest-quality training and certification.
Compliance and training products for personal data protection according to the European Union’s General Data Protection Regulation.
All required policies, procedures, and forms to comply with the EU GDPR privacy regulation.
Train your key people about GDPR requirements to ensure awareness of data protection principles, privacy rights, and regulatory compliance.
Accredited courses for individuals and privacy professionals who want the highest-quality training and certification.
Implementation, training, and knowledge products for Quality Management Systems (QMS) according to the ISO 9001 standard.
All required policies, procedures, and forms to implement a QMS according to ISO 9001.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for Environmental Management Systems (EMS) according to the ISO 14001 standard.
All required policies, procedures, and forms to implement an EMS according to ISO 14001.
Accredited courses for individuals and environmental professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 14001 and the EMS using Advisera’s proprietary AI-powered knowledge base.
Implementation and training products for Occupational Health & Safety Management Systems (OHSMS) according to the ISO 45001 standard.
All required policies, procedures, and forms to implement an OHSMS according to ISO 45001.
Accredited courses for individuals and health & safety professionals who want the highest-quality training and certification.
Implementation and training products for medical device Quality Management Systems (QMS) according to the ISO 13485 standard.
All required policies, procedures, and forms to implement a medical device QMS according to ISO 13485.
Accredited courses for individuals and medical device professionals who want the highest-quality training and certification.
Compliance products for the European Union’s Medical Device Regulation.
All required policies, procedures, and forms to comply with the EU MDR.
Implementation products for Information Technology Service Management Systems (ITSMS) according to the ISO 20000 standard.
All required policies, procedures, and forms to implement an ITSMS according to ISO 20000.
Implementation products for Business Continuity Management Systems (BCMS) according to the ISO 22301 standard.
All required policies, procedures, and forms to implement a BCMS according to ISO 22301.
Implementation products for testing and calibration laboratories according to the ISO 17025 standard.
All required policies, procedures, and forms to implement ISO 17025 in a laboratory.
Implementation products for automotive Quality Management Systems (QMS) according to the IATF 16949 standard.
All required policies, procedures, and forms to implement an automotive QMS according to IATF 16949.
Implementation products for aerospace Quality Management Systems (QMS) according to the AS9100 standard.
All required policies, procedures, and forms to implement an aerospace QMS according to AS9100.
Implementation, maintenance, training, and knowledge products for consultancies.
Handle multiple ISO 27001 projects by automating repetitive tasks during ISMS implementation.
All required policies, procedures, and forms to implement various standards and regulations for your clients.
Grow your business by organizing cybersecurity and compliance training for your clients under your own brand using Advisera’s learning management system platform.
Accredited Lead Auditor and Lead Implementer courses for ISO standards and DORA, and an advanced course to help consultants grow their business.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Find new clients, potential partners, and collaborators and meet a community of like-minded professionals locally and globally.
Implementation, maintenance, training, and knowledge products for the IT industry.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), NIS 2 (critical infrastructure cybersecurity), and DORA (cybersecurity for financial sector).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance, training, and knowledge products for essential and important organizations.
Documentation to comply with NIS 2 (cybersecurity), GDPR (privacy), ISO 27001 (cybersecurity), and ISO 22301 (business continuity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for manufacturing companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for transportation & distribution companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for schools, universities, and other educational organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for telecoms.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for banks, insurance companies, and other financial organizations.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with DORA (cybersecurity for financial sector), ISO 27001 (cybersecurity), ISO 22301 (business continuity), and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for local, regional, and national government entities.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for hospitals and other health organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the medical device industry.
Documentation to comply with MDR and ISO 13485 (medical device), ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the aerospace industry.
Documentation to comply with AS9100 (aerospace), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the automotive industry.
Documentation to comply with IATF 16949 (automotive), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for laboratories.
Documentation to comply with ISO 17025 (testing and calibration laboratories), ISO 9001 (quality), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
 Antonio Jose Segovia
Antonio Jose Segovia
Updated: March 28, 2023, according to the ISO 27001 2022 revision.
Security in project management is an important part of ISO 27001 – many people are wondering how to set it up, and whether their projects should be covered with this control at all. Read this article to find the answers…
It is likely that you’ve heard that “the security of the information not should be seen as a product; it should be seen as a process.” This implies, among other things, that the security of the information is present in any establishment of the organization, being a pillar of the same, and serving as a cross support to the entire organization.
Beware: it is not the same to say that we are going to establish a methodology to manage projects in the field of information security (for example, use a methodology such as PRINCE2 project management to implement a project of ISO 27001), as to say that we are going to establish a methodology to treat the security of information in project management (for example, to use a risk management methodology to analyze security risks of the information relating to a project).
The ISO 27001:2022 standard talks about the second issue, and this will be what we will focus on, but we should take into account the order of the words – as you have seen, it is not the same.
The operation of each company is determined by the constant execution of projects in the short, medium, and long term (internal projects to maintain the structure of the organization, and external projects to provide services to customers).
Projects require collecting and processing data and generating information. They are becoming increasingly dependent on information systems that usually contain vulnerabilities and security flaws. When vulnerabilities are exploited, the success of the projects can be adversely affected. The level of information security in project management dictates how safe your project will be. To maximize long-term return on investment (ROI) with a project’s delivery, taking information security into account with all aspects is essential.
But security is something that is usually forgotten in projects; i.e., when a project is addressed in an organization, it does not usually take into account that it should be led according to the principles of information security project management. However, I’ve found some organizations, mainly large companies, that have included the information security in their projects as just one more activity (for example, running a risk assessment, focused on information security, at the beginning of any project to identify threats/vulnerabilities and risks).
And this is basically what ISO 27001 requests in Annex A.5.8 Information security in project management: Information security shall be addressed in project management, regardless of the type of the project. This control can be applied to all kinds of projects, from a minor IT implementation to a major business change project. Information security should be a part of ‘business as usual’ and, therefore, information security risks and objectives should be considered at the outset of each project.
All projects basically need resources, activities to develop, and established time objectives. Information security in project management can be integrated in several ways:
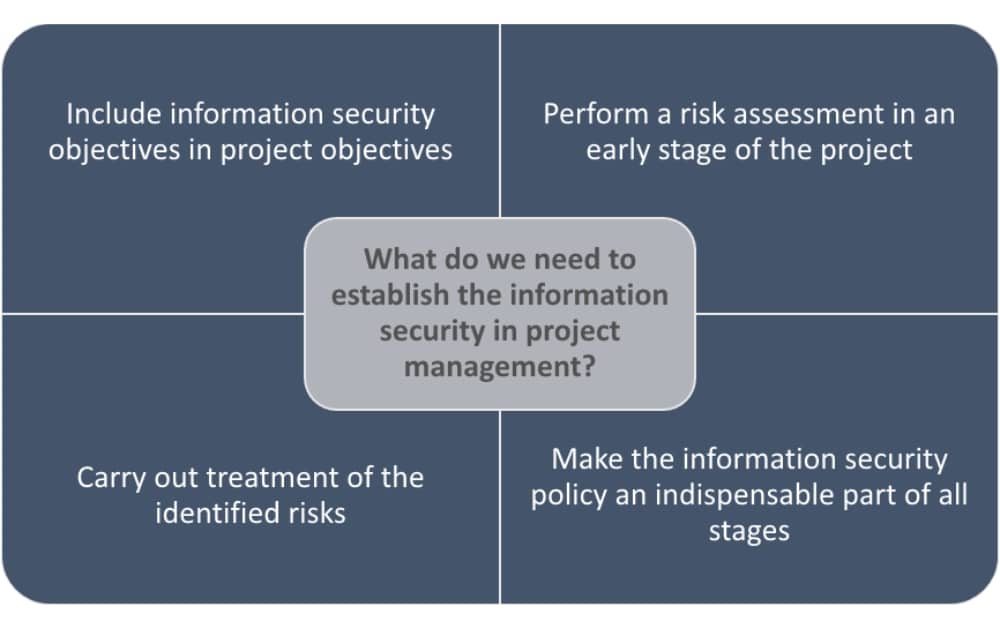
It’s particularly important (independent of the size of the organization) to include information security in project activities for those projects, e.g., which deal with or target integrity, availability, and confidentiality of the information.
In this way, information security will always be a component of the management of any project in the organization, and the organization will also comply with the requirement established by ISO 27001. So, let’s get a closer look into the benefits of information security project management.
ISO 27001 helps to manage the information security of all projects gathered under one roof. From project initiation to the protection from different threats such as data breaches and cyber-attacks, companies can anticipate risks, react accordingly, and secure their information. Documents, databases, devices, cloud servers, etc. remain safe within the project, which becomes resilient thanks to the implementation of ISO 27001.
This control also helps to provide greater importance and presence to the information security in the project management of the organization, which is always positive for this sector, since it is not seen as a simple requirement of a standard, but as a critical parameter in addressing and implementing any project in the organization.
Information security is probably not in place in the management of all projects in your organization. Many times, this is due to lack of knowledge, but after reading this article, that should no longer be an excuse. Also, keep in mind that when information security has more presence in your organization, you will be more important and you will be better valued.
To learn how to become compliant with every clause and control from Annex A and get all the required policies and procedures for controls and clauses, sign up for a free trial of Conformio, the leading ISO 27001 compliance software.


Tolga Aktaş has been working in various disciplines of management systems for more than 15 years. Tolga is an accredited lead auditor for the ISO 9001, 14001, 18295, 22301, 27001, 27701, 37001, and 55001 standards and has conducted audits as a freelancer for internationally accredited conformity assessment companies. He is also an accredited lead auditor trainer for ISO 22301, 27001, and 27701. He conducts workshops and webinars, and provides consultancy services on management systems to organizations mainly in Turkey, the UK, the EU, Qatar, UAE, Germany, and Japan. Tolga holds a Master of Business Administration degree.
You may unsubscribe at any time. For more information, please see our privacy notice.