DORA is a regulation that is focused on cybersecurity and resilience of financial organizations in the European Union — however, for these organizations to be safe, DORA pays special attention to supply chain security, in particular to the IT companies that provide services to financial organizations.
In effect, such IT companies must comply with certain elements of DORA — this article explains which IT companies fall under the scope of DORA, and what exactly is required of them.
DORA requires IT companies that provide their services to financial organizations in the European Union to be compliant with security standards, and to follow specific contractual requirements. If an IT provider is considered critical, then DORA specifies much stricter requirements.
Which IT companies must comply with DORA?
In its Article 3, DORA specifies the following terms and definitions:
- ICT — “information and communication technology”
- ICT services — “digital and data services provided through ICT systems to one or more internal or external users on an ongoing basis, including hardware as a service and hardware services which includes the provision of technical support via software or firmware updates by the hardware provider, excluding traditional analogue telephone services”
- ICT third-party service provider — any company (whether independent or part of a financial group) providing ICT services to financial entities
Therefore, all IT and telecom companies that provide their services to financial entities on an ongoing basis (with the exception of analogue telephone services) must be compliant with DORA.
What must ICT service providers comply with?
All ICT third-party service providers that provide services for financial organizations must comply with the following:
Compliance with security standards. According to Article 28, financial organizations can use services only from companies complying with appropriate information security standards — even through DORA does not say which standards, this will probably go in the direction of ISO 27001 and the European Cybersecurity Certification Scheme.
Contractual obligations. According to Article 30, financial organizations need to include the following clauses in contracts with ICT service providers:
- provisions on availability, authenticity, integrity and confidentiality in relation to the protection of data, including personal data
- provisions on ensuring access, recovery and return in an easily accessible format of personal and non-personal data processed by the financial entity
- the obligation of the ICT third-party service provider to provide assistance to the financial entity
- the participation of ICT third-party service providers in the financial entities’ ICT security awareness programmes and digital operational resilience training
What are critical ICT service providers?
According to Article 31, a critical ICT third-party service provider is designated as such according to the following criteria:
- the systemic impact on the stability, continuity or quality of the provision of financial services
- the systemic character or importance of the financial entities that rely on the relevant ICT third-party service provider
- the degree of substitutability of the ICT third-party service provider, and
- the reliance of financial entities on the services provided by the relevant ICT third-party service provider in relation to critical or important functions of financial entities.
According to Article 3 of DORA, a critical or important function is “a function, the disruption of which would materially impair the financial performance of a financial entity, or the soundness or continuity of its services and activities, or the discontinued, defective or failed performance of that function would materially impair the continuing compliance of a financial entity with the conditions and obligations of its authorisation, or with its other obligations under applicable financial services law.”
European Supervisory Authorities (ESAs) — meaning the European Banking Authority (EBA), European Securities and Markets Authority (ESMA), and European Insurance and Occupational Pensions Authority (EIOPA) — are the ones that determine for each ICT third-party service provider whether it is critical or not.
They decide who is critical based on the criteria listed above, and based on a document that describes these criteria in more detail: CDR 2024/1502 – The criteria for the designation of ICT third-party service providers as critical for financial entities.
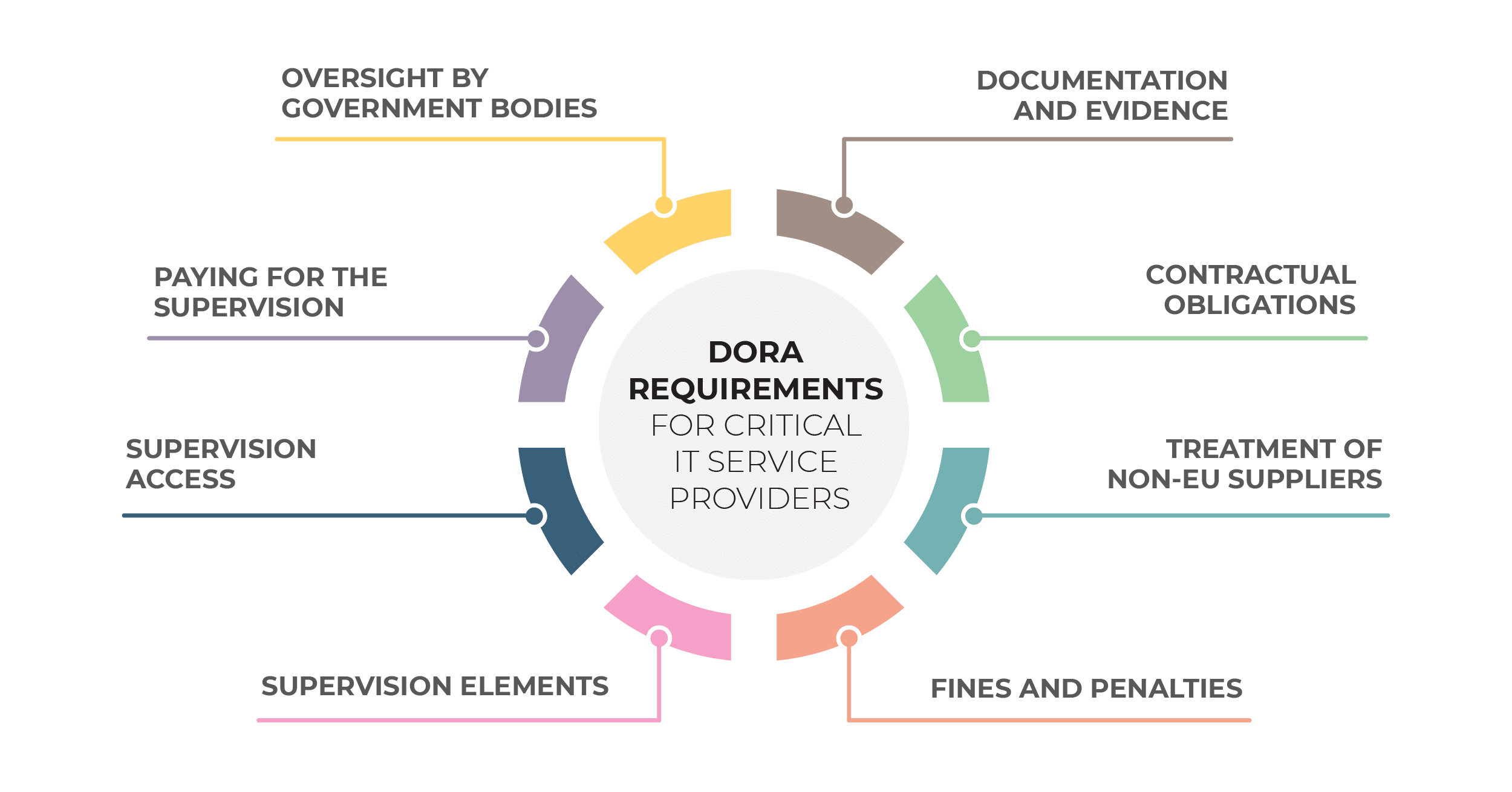
What additional DORA requirements exist for critical ICT service providers?
On top of the requirements specified above, DORA requires critical ICT service providers to comply with a lot more:
Oversight by government bodies. Article 31 specifies that critical service providers are subject to oversight activities by a Lead Overseer, which is appointed by European Supervisory Authorities (ESAs).
According to Article 33, the purpose of the Lead Overseer is to continually assess whether such an IT provider has in place “comprehensive, sound and effective rules, procedures, mechanisms and arrangements to manage the ICT risk which it may pose to financial entities.”
Paying for the supervision. Article 43 specifies that the supervision comes with a cost, and that the Lead Overseer calculates this cost every year. According to CDR 2024/1505 The amount of the oversight fees to be charged by the Lead Overseer to critical ICT third-party service providers and the way in which those fees are to be paid, the minimum annual fee is 50,000 euros.
Supervision access. According to Article 39, the IT service provider needs to allow the Lead Overseer to “enter in, and conduct all necessary onsite inspections on, any business premises, land or property of the ICT third-party service providers, such as head offices, operation centres, secondary premises, as well as to conduct off-site inspections.”
Supervision elements. According to Article 33, the Lead Overseer must check the following:
- ICT requirements to ensure the security, availability, continuity, scalability and quality of services
- ability to maintain at all times high standards of availability, authenticity, integrity or confidentiality of data
- the physical security contributing to ensuring the ICT security, including the security of premises, facilities, data centres
- the risk management processes, including Information Security Policy, ICT business continuity policy and ICT response and recovery plans
- the governance arrangements, including an organisational structure with clear, transparent and consistent lines of responsibility and accountability rules enabling effective ICT risk management
- the identification, monitoring and prompt reporting of material ICT-related incidents, the management and resolution of those incidents, in particular cyber-attacks
- the mechanisms for data portability, application portability and interoperability
- the testing of ICT systems, infrastructure and controls
- the ICT audits
- the use of relevant national and international standards applicable to the provision of its ICT services to the financial entities
Documentation and evidence. According to Article 37, the Lead Overseer may require the following documentation and evidence: “all relevant business or operational documents, contracts, policies, documentation, ICT security audit reports, ICT-related incident reports, as well as any information relating to parties to whom the critical ICT third-party service provider has outsourced operational functions or activities.”
Additional contractual obligations. Article 30 specifies that financial entities must sign agreements with specific clauses for critical service providers, including:
- precise quantitative and qualitative performance targets within the agreed service levels
- notice periods and reporting obligations
- implementing and testing business contingency plans
- have in place ICT security measures, tools, and policies that provide an appropriate level of security for the provision of services by the financial entity
- participate and fully cooperate in the threat-led penetration testing of a financial entity
- unrestricted rights of access, inspection, and audit by the financial entity
- obligation to fully cooperate during the onsite inspections and audits
- continuing to provide the ICT services during a period of cancellation of the agreement
- allowing the financial entity to migrate to another ICT third-party service provider
Treatment of non-EU suppliers. Article 31 says that if the critical service provider is based in a non-EU country, then it must establish a subsidiary within the EU.
Article 36 specifies that the Lead Overseer may exercise the powers “on any premises located in a third-country which is owned, or used in any way, for the purposes of providing services to Union financial entities, by a critical ICT third-party service provider.”
Fines and penalties. In its Article 35, DORA is quite specific on fines that critical ICT third-party service providers need to pay if they are not compliant: This is up to 1% of their worldwide annual turnover, and the amount of the fine depends on the number of days that the service provider was not compliant. Further, the Lead Overseer must issue a public notice that reveals the name of the service provider that was fined.
Article 42 specifies perhaps the worst penalty — a competent authority can require a financial organization that is a client of an IT service provider that is not compliant with DORA to stop using their services.
Get prepared
So, if your IT company is providing services to financial organizations, you’ll have to prepare for DORA. You might start considering ISO 27001, since most IT companies go for it, and it covers all the requirements listed above — you can find more details here: ISO 27001 Implementation Guide: Checklist of Steps, Timing, and Costs Involved.
To get all the ISO 27001 documents required for the certification, check out this ISO 27001 Documentation Toolkit.

 Dejan Kosutic
Dejan Kosutic