If your financial organization needs to comply with the DORA regulation, you need a comprehensive approach to make sure you comply with all the requirements. The steps in this article present the best practice to cover all of those complex requirements.
From my experience, the following 18 steps will enable you to comply with DORA efficiently. Before I present the steps, a couple of important notes:
- The steps below are designed for financial organizations, whereas for IT companies that need to comply with DORA, see this article: Which IT companies need to comply with DORA, and how?
- In its Article 16, DORA specifies special rules for smaller financial organizations called the “simplified ICT risk management framework” — nevertheless, even for such smaller organizations, the 18 steps listed below are valid, the only difference being that the requirements might be somewhat less strict. See which financial entities qualify for simplified risk management here: Who must comply with the DORA regulation?
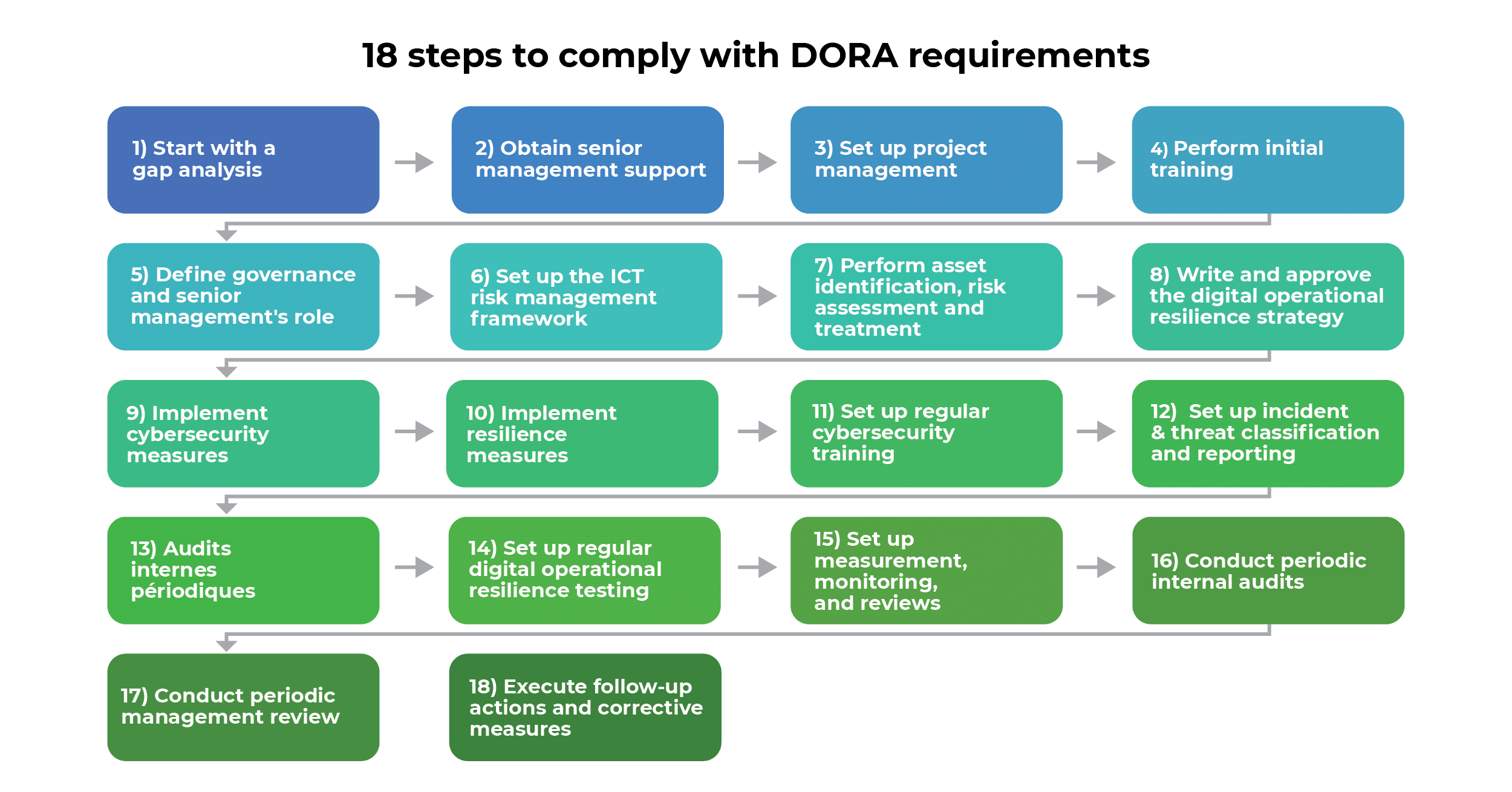
1) Start with a gap analysis
First, since your financial entity probably already does comply with many DORA requirements, it is useful to find out what are you missing.
Once you know your gap, you can decide which of the following steps are applicable to you.
2) Obtain senior management support
Even though compliance with DORA is mandatory, you still might have problems with implementing various aspects of it — this is why it is important to have formal approval from the top management for the project, together with enough time, people, and budget to implement it.
This way, you will be able to overcome most of the problems that you will face during the project.
3) Set up project management
To make your project run more smoothly, you need to define:
- Responsibilities — who is in charge (project manager), who from the senior management will help you if you get stuck (project sponsor), and with whom from the mid-level management you need to cooperate the most (project team). If you already have a security committee, this might serve as your project team.
- Milestones — define the major steps in your project, and their timing.
- Project outcomes — define exactly what kinds of documents, activities, and other things will be produced during the project.
4) Perform initial training
Since DORA and its related Commission Delegated Regulations are quite complex, you should train the project team at the very early stage of the project. In the beginning, it makes sense to start with introductory topics on DORA, and later on focus on specific DORA requirements.
This way, you will have a knowledgeable team of people that will execute the project in a much more efficient way.
See also: How to organize DORA training and awareness
5) Define governance and senior management’s role
In its Article 5, DORA is quite specific regarding the responsibilities of the senior management, and how to set up the governance of ICT risks. This includes setting up policies, roles, and responsibilities; approving the strategy, audit plans, and budget; setting up reporting channels, etc.
Such governance is the foundation upon which the ICT risk management is built.
6) Set up the ICT risk management framework
Article 6 specifies what the risk management framework looks like — according to it, you need to establish appropriate “… strategies, policies, procedures, ICT protocols and tools that are necessary to duly and adequately protect all information assets and ICT assets.”
This kind of documented framework will enable you to perform the next steps, starting with risk assessment and treatment.
7) Perform asset identification, risk assessment, and treatment
In its Article 8, DORA requires financial organizations to “identify, classify and adequately document all ICT supported business functions, roles and responsibilities, the information assets and ICT assets supporting those functions, and their roles and dependencies,” and, on top of this, to identify threats, vulnerabilities, and risks.
Further, it requires classifying those assets that are considered critical, and identifying if ICT third-party service providers support any critical or important functions.
This kind of analysis is important to decide which cybersecurity measures need to be implemented.
8) Write and approve the digital operational resilience strategy
Article 8(6) requires a comprehensive document to be written, called the digital operational resilience strategy — it must include several elements, including how the risk management framework supports business strategy and objectives, risk tolerance level, and security objectives, and it needs to explain how the risk management framework needs to be implemented.
This is a crucial step because it sets in motion the implementation of concrete cybersecurity and resilience measures.
9) Implement cybersecurity measures
Articles 9 and 10 specify various cybersecurity measures that must be implemented, including network management, access control, authentication, change management, patches and updates, detection of anomalous activities, etc.
These will probably take the longest time to implement, but this is, in fact, the core of cybersecurity.
10) Implement resilience measures
Articles 11 and 12 are oriented towards business continuity, and include a top-level ICT business continuity policy, business impact analysis (BIA), response and recovery plans, crisis management and communication, and testing, but also backup and restoration.
These measures are a bit more abstract than the cybersecurity measures from the previous step, but are nevertheless equally important, especially when a financial organization needs to deal with larger incidents.
11) Set up risk management for ICT third-party risk
DORA dedicates Articles 28 to 30 to how to handle IT companies that provide their services to financial organizations. This includes assessing the risks related to a particular IT provider, specific contractual obligations, defining the exit strategy, etc.
DORA recognizes that managing supply chain risk is of greatest importance, because it introduces a government oversight of critical IT service providers, although financial organizations are not directly impacted by such oversight.
12) Set up regular cybersecurity training
Articles 5, 13, and 16 require financial organizations to set up regular training and awareness for all employees, including the senior management. Articles 13 and 30 go a step further, and require financial entities to “include ICT third-party service providers in their relevant training schemes.”
This step is pretty obvious — with all these complex rules and requirements, it would be hard to expect that people would follow them without being trained and aware.
Read more here: Options for delivering NIS 2, DORA, and ISO 27001 training
13) Set up incident & threat classification and reporting
Articles 17 to 19 require financial organizations to “define, establish and implement an ICT-related incident management process to detect, manage and notify ICT-related incidents,” including their classification and reporting to authorities.
Despite all the (preventive) cybersecurity measures, it will be impossible to avoid every incident — this is why the response to them needs to be effective, and all interested parties need to be informed.
14) Set up regular digital operational resilience testing
The whole Chapter IV is dedicated to digital operational resilience testing and requires “the execution of appropriate tests, such as vulnerability assessments and scans, open source analyses, network security assessments, gap analyses, physical security reviews, questionnaires and scanning software solutions, source code reviews where feasible, scenario-based tests, compatibility testing, performance testing, end-to-end testing and penetration testing,” “for the purpose of assessing preparedness for handling ICT-related incidents, of identifying weaknesses, deficiencies and gaps in digital operational resilience, and of promptly implementing corrective measures.” This also includes the “Threat-Led Penetration Testing.”
This kind of testing is crucial in order to find out what the real situation is. The internal audit explained in step #16 has a similar purpose, but is done in a different way.
15) Set up measurement, monitoring, and reviews
It is impossible to manage anything, let alone cybersecurity and resilience in a financial entity, if you’re not informed about its performance. This is why Article 13 requires several types of reports and information to reach appropriate managers, including post-incident reviews, lessons from operational testing, effectiveness of the implementation of the digital operational resilience strategy, technological developments, etc.
This way, the management can react quickly and appropriately to any trend or risk.
16) Conduct periodic internal audits
Articles 5 and 6 require financial entities to perform regular internal audits by auditors that have enough independence, and “sufficient knowledge, skills and expertise in ICT risk.”
Such audits are crucial to find out what the reality is in a company, because very often policies and procedures define one thing, but in reality employees might be doing something very different.
17) Conduct periodic management review
Article 5 specifies several review activities that need to be performed regularly by the senior management — these include reviewing the business continuity policy, response and recovery plans, policy for the use of third-party ICT services, various reports, internal audits, digital resilience budget, etc.
Such reviews are crucial, because this is how the senior management is informed about key risks and activities related to cybersecurity and resilience.
18) Execute follow-up actions and corrective measures
Follow-up actions and corrective measures are mentioned in different contexts in DORA — e.g., Article 6 requires a follow-up process after an internal audit, Article 17 requires a follow-up after incidents, Article 24 requires corrective measures after digital operational resilience testing, while Article 30 requires corrective actions to be included in the contracts with IT suppliers.
All of these are crucial for ICT risk management to be continually improved and, consequently, digital operational resilience to be raised to a better level.
To find all the documents needed for complying with the DORA Regulation, check out this DORA Documentation Toolkit that includes all policies, procedures, plans, and other templates.

 Dejan Kosutic
Dejan Kosutic