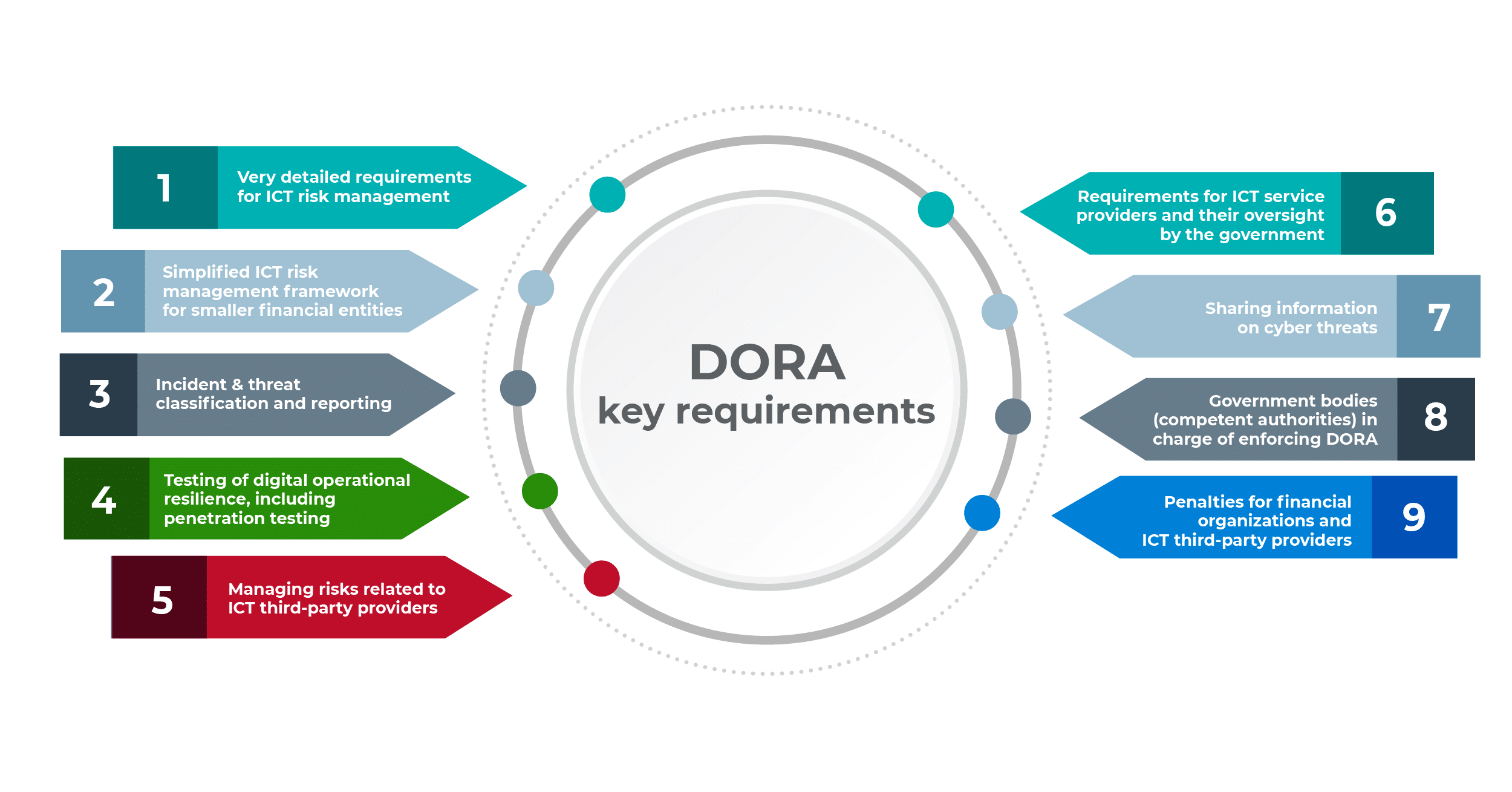
The DORA regulation is quite lengthy: 106 preamble items and 64 articles, altogether 79 pages — it would probably take you a couple of days (if not weeks) to read it through. To save you some reading time, this article summarizes the most important points from DORA.
- requirements for ICT risk management
- simplified ICT risk management framework for smaller financial entities
- incident & threat classification and reporting
- testing of digital operational resilience, including penetration testing
- managing risks related to ICT third-party providers
- etc.
In the text below, you’ll find nine key requirements specified in DORA — please keep in mind these are requirements from the point of view of financial organizations and their IT suppliers that need to comply with DORA, not from the viewpoint of competent authorities (i.e., government bodies in charge of enforcing this regulation).
1) Very detailed requirements for ICT risk management
The requirements for ICT risk management are described in DORA’s Chapter II, and in CDR 2024/1774 Regulatory technical standards specifying ICT risk management tools, methods, processes, and policies and the simplified ICT risk management framework; altogether 54 articles in 42 pages — a lot to take in.
DORA has structured the ICT risk management requirements in the following way:
- Governance and organisation
- ICT risk management framework
- ICT systems, protocols and tools
- Identification
- Protection and prevention
- Detection
- Response and recovery
- Backup policies and procedures, restoration and recovery procedures and methods
- Learning and evolving
- Communication
2) Simplified ICT risk management framework for smaller financial entities
The ICT risk management requirements specified above would probably be overwhelming for smaller financial organizations, which is why DORA has specified a “lighter” version of ICT risk management for such entities.
This simplified ICT risk management framework is specified in DORA’s Article 16 and in Title III of CDR 2024/1774 Regulatory technical standards specifying ICT risk management tools, methods, processes, and policies and the simplified ICT risk management framework.
The simplified framework follows a very similar structure to the “regular” ICT risk management specified in DORA’s Chapter II, with the main difference being that the requirements are not as detailed nor as strict.
3) Incident & threat classification and reporting
DORA dedicates the whole of chapter Chapter III to management, classification, and reporting of incidents and threats. It requires setting up an incident management process, defines criteria for classifying incidents and threats, and defines how they need to be reported.
Similar to requirements in NIS 2, financial entities need to submit the following incident reports to competent authorities: initial notification, intermediate report, and a final report; further, they need to inform them about significant cyber threats. Financial organizations also need to inform their clients of any major ICT-related incidents or significant cyber threats.
4) Testing of digital operational resilience, including penetration testing
In its Chapter IV, DORA requires financial entities to execute a digital operational resilience testing program that includes “a range of assessments, tests, methodologies, practices and tools.”
The tests need to be performed at least once a year on all ICT systems supporting critical or important functions. According to Article 25, those tests could include “vulnerability assessments and scans, open source analyses, network security assessments, gap analyses, physical security reviews, questionnaires and scanning software solutions, source code reviews where feasible, scenario-based tests, compatibility testing, performance testing, end-to-end testing and penetration testing.”
Article 26 introduces the concept of Threat-Led Penetration Testing (TLPT) that needs to be carried out at least once every three years, and provides detailed rules for such testing.
5) Managing risks related to ICT third-party providers
DORA specifies very strict rules on how financial entities need to handle their IT providers, in order to reduce third-party risks. Those rules include adopting a strategy on ICT third-party risk and a policy on the use of ICT services, regular review of third-party risks, and preparing an exit strategy (Article 28).
Further, financial entities must perform preliminary assessment of an IT supplier before starting to use their products and services (Article 29) and make sure they comply with information security standards.
Finally, in its article (Article 30), DORA specifies minimum contractual clauses that need to be included in agreements with ICT third-party providers.
6) Requirements for ICT service providers and their oversight by the government
ICT third-party providers that provide their services to financial organizations need to comply with security standards, and with specific contractual requirements. If those service providers are designated as critical, then there are a lot more requirements they have to comply with.
European Supervisory Authorities (ESAs) will appoint a Lead Overseer for each ICT third-party provider that is classified as critical. According to Article 33, the purpose of the Lead Overseer is to continually assess whether such an IT provider has in place “comprehensive, sound and effective rules, procedures, mechanisms and arrangements to manage the ICT risk which it may pose to financial entities.”
Lead Overseers have the right of full access to any information from ICT third-party providers, and they can conduct investigations and issue recommendations, as well as enforce fines and other penalties.
Find out more here: Which IT companies need to comply with DORA, and how?
7) Sharing information on cyber threats
Although Chapter VI is the shortest chapter in DORA, it might introduce quite big changes in how threat intelligence is handled.
It specifies the baseline for exchange of cyber threat information and intelligence, and the role of competent authorities and IT service providers.
8) Government bodies (competent authorities) in charge of enforcing DORA
According to regulations referenced in Article 46, for the majority of financial entities that need to be compliant with DORA, EU Member States designate competent authorities that supervise and enforce financial regulations.
There are a couple of exceptions, where EU authorities directly supervise and enforce financial regulations:
- For credit institutions classified as significant – the European Central Bank (ECB)
- For securitisation repositories – the European Securities and Markets Authority (ESMA)
9) Penalties for financial organizations and ICT third-party providers
For financial entities, DORA does not specify minimum fines — rather, it gives the freedom to Member States to define their own fines in their countries. It does, however, specify other penalties that can be enacted by competent authorities, including giving orders to stop activities not compliant with DORA, defining any measures to make sure entities are compliant with DORA, and issuing public notices.
For critical ICT third-party service providers, DORA specifies a fine of up to 1% of their worldwide annual turnover. Further, the Lead Overseer (the body that supervises critical service providers) must issue public notice that reveals the name of the service provider that was fined.
Finally, a competent authority overseeing a financial organization using the services of a third-party service provider that is not compliant with DORA can order this financial organization to stop using those services.
If you want to organize a cybersecurity training and awareness program for your employees, sign up for a free trial of the Company Training Academy – it will provide you with a series of short videos and enable progress reports.

 Dejan Kosutic
Dejan Kosutic