 Neven Zitek
Neven Zitek
February 12, 2014

Implementation, maintenance, training, and knowledge products for Information Security Management Systems (ISMS) according to the ISO 27001 standard.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
All required policies, procedures, and forms to implement an ISMS according to ISO 27001.
Train your key people about ISO 27001 requirements and provide cybersecurity awareness training to all of your employees.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance and training products for critical infrastructure organizations for the European Union’s Network and Information Systems cybersecurity directive.
All required policies, procedures, and forms to comply with the NIS 2 cybersecurity directive.
Company-wide training program for employees and senior management to comply with Article 20 of the NIS 2 cybersecurity directive.
Compliance and training products for financial entities for the European Union’s DORA regulation.
All required policies, procedures, and forms to comply with the DORA regulation.
Company-wide cybersecurity and resilience training program for all employees, to train them and raise awareness about ICT risk management.
Accredited courses for individuals and DORA professionals who want the highest-quality training and certification.
Training products for Artificial Intelligence Management Systems (AIMS) and AI governance according to the ISO 42001 standard.
Accredited courses for individuals, consultants, and AI professionals who want the highest-quality training and certification in AI governance and compliance.
Train your key people on ISO 42001 requirements and provide company-wide AI governance training so employees learn how to use AI responsibly and in compliance with your policies.
Compliance and training products for personal data protection according to the European Union’s General Data Protection Regulation.
All required policies, procedures, and forms to comply with the EU GDPR privacy regulation.
Train your key people about GDPR requirements to ensure awareness of data protection principles, privacy rights, and regulatory compliance.
Accredited courses for individuals and privacy professionals who want the highest-quality training and certification.
Implementation, training, and knowledge products for Quality Management Systems (QMS) according to the ISO 9001 standard.
All required policies, procedures, and forms to implement a QMS according to ISO 9001.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for Environmental Management Systems (EMS) according to the ISO 14001 standard.
All required policies, procedures, and forms to implement an EMS according to ISO 14001.
Accredited courses for individuals and environmental professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 14001 and the EMS using Advisera’s proprietary AI-powered knowledge base.
Implementation and training products for Occupational Health & Safety Management Systems (OHSMS) according to the ISO 45001 standard.
All required policies, procedures, and forms to implement an OHSMS according to ISO 45001.
Accredited courses for individuals and health & safety professionals who want the highest-quality training and certification.
Implementation and training products for medical device Quality Management Systems (QMS) according to the ISO 13485 standard.
All required policies, procedures, and forms to implement a medical device QMS according to ISO 13485.
Accredited courses for individuals and medical device professionals who want the highest-quality training and certification.
Compliance products for the European Union’s Medical Device Regulation.
All required policies, procedures, and forms to comply with the EU MDR.
Implementation products for Information Technology Service Management Systems (ITSMS) according to the ISO 20000 standard.
All required policies, procedures, and forms to implement an ITSMS according to ISO 20000.
Implementation products for Business Continuity Management Systems (BCMS) according to the ISO 22301 standard.
All required policies, procedures, and forms to implement a BCMS according to ISO 22301.
Implementation products for testing and calibration laboratories according to the ISO 17025 standard.
All required policies, procedures, and forms to implement ISO 17025 in a laboratory.
Implementation products for automotive Quality Management Systems (QMS) according to the IATF 16949 standard.
All required policies, procedures, and forms to implement an automotive QMS according to IATF 16949.
Implementation products for aerospace Quality Management Systems (QMS) according to the AS9100 standard.
All required policies, procedures, and forms to implement an aerospace QMS according to AS9100.
Implementation, maintenance, training, and knowledge products for consultancies.
Handle multiple ISO 27001 projects by automating repetitive tasks during ISMS implementation.
All required policies, procedures, and forms to implement various standards and regulations for your clients.
Grow your business by organizing cybersecurity and compliance training for your clients under your own brand using Advisera’s learning management system platform.
Accredited Lead Auditor and Lead Implementer courses for ISO standards and DORA, and an advanced course to help consultants grow their business.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Find new clients, potential partners, and collaborators and meet a community of like-minded professionals locally and globally.
Implementation, maintenance, training, and knowledge products for the IT industry.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), NIS 2 (critical infrastructure cybersecurity), and DORA (cybersecurity for financial sector).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance, training, and knowledge products for essential and important organizations.
Documentation to comply with NIS 2 (cybersecurity), GDPR (privacy), ISO 27001 (cybersecurity), and ISO 22301 (business continuity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for manufacturing companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for transportation & distribution companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for schools, universities, and other educational organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), and GDPR (privacy).
Company-wide cybersecurity and AI governance awareness program for all employees, to decrease incidents, support a successful cybersecurity program, and ensure responsible use of AI.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for telecoms.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for banks, insurance companies, and other financial organizations.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with DORA (cybersecurity for financial sector), ISO 27001 (cybersecurity), ISO 22301 (business continuity), and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for local, regional, and national government entities.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for hospitals and other health organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity and AI governance awareness program for all employees, to decrease incidents, support a successful cybersecurity program, and ensure responsible use of AI.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the medical device industry.
Documentation to comply with MDR and ISO 13485 (medical device), ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the aerospace industry.
Documentation to comply with AS9100 (aerospace), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the automotive industry.
Documentation to comply with IATF 16949 (automotive), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity and AI program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for laboratories.
Documentation to comply with ISO 17025 (testing and calibration laboratories), ISO 9001 (quality), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
 Neven Zitek
Neven Zitek
As part of an IT organization, how would you rate your relationship with the Human Resources (HR) department? If your answer is “good,” I’ll assume that you joined your IT organization very recently. As far as I can tell, it has been a constant battle between HR and IT regarding granting and revoking user rights within IT systems when a new employee is hired, promoted, demoted or leaving the company. HR considers access to IT resources to be purely an IT topic, and IT expects that HR will provide timely and informed feedback regarding IT services and user access rights within those services required for the employee in question.
To make things even worse, if there is no IT Service Catalogue defined, it’s almost impossible to maintain any form of Access Management. Ten years ago, when I shifted my carrier direction from telecom into the IT industry, I was amazed by IT staffs’ ability to maintain records about who needs to access what – just by memorizing their organization’s internal structure and employees’ functions within the company. And we’re talking about a company with 1000+ employees. Wow.
The first issues began to surface when the next generation of IT staff started to replace older colleagues – as they weren’t so familiar with the delicate eco-system that their predecessors nourished, and weren’t willing to take any responsibility for possible mistakes within access configuration.
The role of Access Management is to enable users (and groups of users) with appropriate levels of access to the services presented in the IT Service Catalogue. Access is the term that describes the level and extent of the service functionality available to the user, and is related to the user identity, which uniquely distinguishes one individual from another, verifying / confirming their status within the organization. User rights (or privileges) refer to actual settings within a service that are granted to the user or user group, e.g. read, write, list, execute, delete, change, etc. With all necessary basics covered, lets look at process activities of the Access Management.
It all starts with requesting access to the service by using any of these common methods:
Rules about how to access services are generally described within the Service Catalogue.
Access Management should verify each request from the two following perspectives:
We check the identity of the requester by username / password combination, or by any other method (e.g. using biometric data). However, in order to verify a request for legitimacy, we need something more than the user request, such as: notification from HR, approval from process owner / manager, submission of Change Management RFC, or a policy that defines access to the service in question without the need for any previous means of confirmation.
It’s important to note that Access Management doesn’t decide who gets access to a particular service, but executes policies and regulations defined during the Service Strategy phase. Access Management will provide necessary rights by sending a request to every department responsible for the service(s) in question. If possible, those tasks should be automated.
Working within any organization means that employees will come and go, and change functions and positions; therefore, their needs for IT services will change accordingly. Access Management should understand the lifecycle of a typical user of IT services in order to prepare and automate its own processes accordingly.
When preparing such processes, Access Management is responsible to design them in such a manner that will enable an easy change of user status, or group transfer, with a clear and recorded audit trail.
Ensuring that rights provided are used properly, Access Monitoring and Control must be included in monitoring activities of all Service Operation processes. Information Security plays a vital role in detecting unauthorized access, compared to access rights granted by Access Management – therefore, IS should include Access Management in its definition of parameters in Intrusion Detection and Prevention tools.
Just as Access Management is responsible for providing proper rights to access service, it’s also responsible for revoking or restricting them. In short, removing rights is the same as (3) Providing Rights, but in reverse.
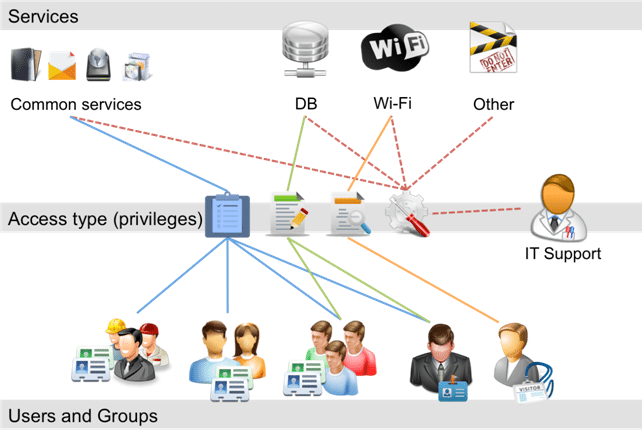
Even if you work in a somewhat smaller organization, you’ll notice that Access Management, Change Management, Incident Management, and all the other processes are nothing more than individual threads in your great tapestry called Service Management. In this example, Access Management is closely dependent on Change Management, Information Security, etc., in order to fulfill its purpose. Therefore, when your processes include or depend on other processes outside the IT organization (e.g. HR), make sure they understand the importance of that single thread in your tapestry. Otherwise, your tapestry may end up being used as a rug.
* Latin proverb
To implement ISO 20000 easily and efficiently, use our ISO 20000 Documentation Toolkit that provides step-by-step guidance for full ISO 20000 compliance.

You may unsubscribe at any time. For more information please see our privacy notice.