Rhand Leal
Rhand Leal
September 7, 2015

Implementation, maintenance, training, and knowledge products for Information Security Management Systems (ISMS) according to the ISO 27001 standard.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
All required policies, procedures, and forms to implement an ISMS according to ISO 27001.
Train your key people about ISO 27001 requirements and provide cybersecurity awareness training to all of your employees.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance and training products for critical infrastructure organizations for the European Union’s Network and Information Systems cybersecurity directive.
All required policies, procedures, and forms to comply with the NIS 2 cybersecurity directive.
Company-wide training program for employees and senior management to comply with Article 20 of the NIS 2 cybersecurity directive.
Compliance and training products for financial entities for the European Union’s DORA regulation.
All required policies, procedures, and forms to comply with the DORA regulation.
Company-wide cybersecurity and resilience training program for all employees, to train them and raise awareness about ICT risk management.
Accredited courses for individuals and DORA professionals who want the highest-quality training and certification.
Training products for Artificial Intelligence Management Systems (AIMS) and AI governance according to the ISO 42001 standard.
Accredited courses for individuals, consultants, and AI professionals who want the highest-quality training and certification in AI governance and compliance.
Train your key people on ISO 42001 requirements and provide company-wide AI governance training so employees learn how to use AI responsibly and in compliance with your policies.
Compliance and training products for personal data protection according to the European Union’s General Data Protection Regulation.
All required policies, procedures, and forms to comply with the EU GDPR privacy regulation.
Train your key people about GDPR requirements to ensure awareness of data protection principles, privacy rights, and regulatory compliance.
Accredited courses for individuals and privacy professionals who want the highest-quality training and certification.
Implementation, training, and knowledge products for Quality Management Systems (QMS) according to the ISO 9001 standard.
All required policies, procedures, and forms to implement a QMS according to ISO 9001.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for Environmental Management Systems (EMS) according to the ISO 14001 standard.
All required policies, procedures, and forms to implement an EMS according to ISO 14001.
Accredited courses for individuals and environmental professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 14001 and the EMS using Advisera’s proprietary AI-powered knowledge base.
Implementation and training products for Occupational Health & Safety Management Systems (OHSMS) according to the ISO 45001 standard.
All required policies, procedures, and forms to implement an OHSMS according to ISO 45001.
Accredited courses for individuals and health & safety professionals who want the highest-quality training and certification.
Implementation and training products for medical device Quality Management Systems (QMS) according to the ISO 13485 standard.
All required policies, procedures, and forms to implement a medical device QMS according to ISO 13485.
Accredited courses for individuals and medical device professionals who want the highest-quality training and certification.
Compliance products for the European Union’s Medical Device Regulation.
All required policies, procedures, and forms to comply with the EU MDR.
Implementation products for Information Technology Service Management Systems (ITSMS) according to the ISO 20000 standard.
All required policies, procedures, and forms to implement an ITSMS according to ISO 20000.
Implementation products for Business Continuity Management Systems (BCMS) according to the ISO 22301 standard.
All required policies, procedures, and forms to implement a BCMS according to ISO 22301.
Implementation products for testing and calibration laboratories according to the ISO 17025 standard.
All required policies, procedures, and forms to implement ISO 17025 in a laboratory.
Implementation products for automotive Quality Management Systems (QMS) according to the IATF 16949 standard.
All required policies, procedures, and forms to implement an automotive QMS according to IATF 16949.
Implementation products for aerospace Quality Management Systems (QMS) according to the AS9100 standard.
All required policies, procedures, and forms to implement an aerospace QMS according to AS9100.
Implementation, maintenance, training, and knowledge products for consultancies.
Handle multiple ISO 27001 projects by automating repetitive tasks during ISMS implementation.
All required policies, procedures, and forms to implement various standards and regulations for your clients.
Grow your business by organizing cybersecurity and compliance training for your clients under your own brand using Advisera’s learning management system platform.
Accredited Lead Auditor and Lead Implementer courses for ISO standards and DORA, and an advanced course to help consultants grow their business.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Find new clients, potential partners, and collaborators and meet a community of like-minded professionals locally and globally.
Implementation, maintenance, training, and knowledge products for the IT industry.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), NIS 2 (critical infrastructure cybersecurity), and DORA (cybersecurity for financial sector).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance, training, and knowledge products for essential and important organizations.
Documentation to comply with NIS 2 (cybersecurity), GDPR (privacy), ISO 27001 (cybersecurity), and ISO 22301 (business continuity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for manufacturing companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for transportation & distribution companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for schools, universities, and other educational organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), and GDPR (privacy).
Company-wide cybersecurity and AI governance awareness program for all employees, to decrease incidents, support a successful cybersecurity program, and ensure responsible use of AI.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for telecoms.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for banks, insurance companies, and other financial organizations.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with DORA (cybersecurity for financial sector), ISO 27001 (cybersecurity), ISO 22301 (business continuity), and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for local, regional, and national government entities.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for hospitals and other health organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity and AI governance awareness program for all employees, to decrease incidents, support a successful cybersecurity program, and ensure responsible use of AI.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the medical device industry.
Documentation to comply with MDR and ISO 13485 (medical device), ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity, privacy, and AI program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the aerospace industry.
Documentation to comply with AS9100 (aerospace), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the automotive industry.
Documentation to comply with IATF 16949 (automotive), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity and AI program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for laboratories.
Documentation to comply with ISO 17025 (testing and calibration laboratories), ISO 9001 (quality), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
 Rhand Leal
Rhand Leal
One would expect that ISO 27001, the leading information security standard, would have strict requirements regarding BYOD. However, you would be surprised – such requirements do not exist, and what’s more, BYOD is ever mentioned in the standard.
BYOD is, of course, unavoidable in a modern company, so how do you make yourself compliant with ISO 27001?
BYOD stands for Bring Your Own Device, referring to a trend where employees make use of their own personal devices (e.g., smartphones, laptops, tablets, USB drives, etc.) to connect to their employers’ organizations’ networks and information systems.
Main reasons for to adopting BYOD in companies are related to:
Main risks related to the adoption of BYOD are:
To achieve the benefits of BYOD, while minimizing the potential risks of information compromise, organizations define rules for the use of personal devices in the workplace in documents commonly called a BYOD policy.
By adopting and communicating a BYOD policy, organizations define boundaries for access and use of personal devices, as well as potential consequences to employees for the misuse of information and damages to the organization’s networks and information systems.
First, let’s see which ISO 27001 controls are the closest to BYOD.
A.6.2.1 Mobile device policy – this control requires development of a security policy for using mobile devices in order to reduce risks. Therefore, the BYOD policy must be based on identified risks.
A.6.2.2 Teleworking – since employees’ personal mobile devices are used not only in company offices, but also at home, this control is also applicable for BYOD. The control requires the implementation of security measures for information access, processing, and storage – this means that the BYOD policy must cover all of those three areas.
A.13.2.1 Information transfer policies and procedures – this control requires writing documentation for the protection of information that is transferred through any communication equipment, including employees’ personal mobile devices. So, if you didn’t write separate policies or procedures for information transfer, you can cover these requirements in the BYOD policy.
A.13.2.3 Electronic messaging – again, if you didn’t define through some other document how electronic messages will be protected, then the BYOD policy is the right place to do it.
There are some other controls that are not so directly related to BYOD, like A.8.1.3 Acceptable use of assets (defining rules on how each asset is to be used), A.8.2.3 Handling of assets (defining rules on which protection measures are to be used according to information classification), and at least a dozen other controls. However, I think the four controls I listed above are the most relevant in terms of BYOD, so let’s focus on them.
Creating a 20-page policy with detailed rules that will cover every security detail might seem attractive to you, but believe me, it’s not going to work.
When starting to write this policy, you should keep the main goal in mind: to change the behavior of the BYOD users in your company. And, if you want to change someone’s behavior, especially if this change involves the hassle of using some additional security rules, then you need to make the rules easily understandable and short. See also: Seven steps for implementing policies and procedures.
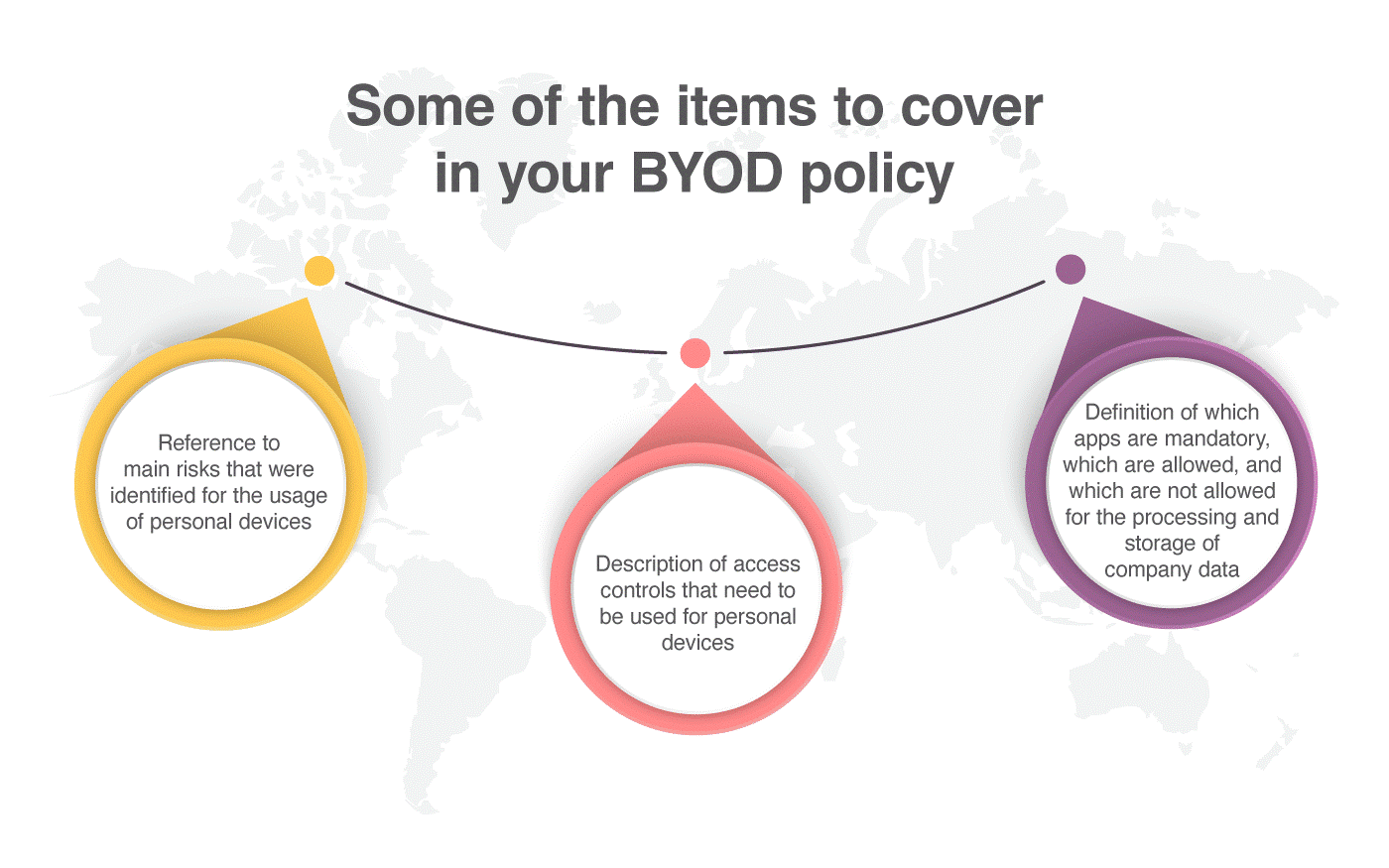
So, from the perspective of the ISO 27001 controls I listed above, in your BYOD policy you should cover the following:
The following items would be useful in the BYOD policy as well:
So, to conclude, although ISO 27001 is not very focused on the Bring Your Own Device concept, taking its appropriate controls can be quite helpful when writing the BYOD policy. And remember: documents are not important; changing the people’s behavior is. Therefore, keep your documents short and simple.
To use a wizard to build your BYOD policy, sign up for a 14-day free trial of Conformio, the leading ISO 27001 compliance software.

Rhand Leal has more than 15 years of experience in information security, and for six years he continuously maintained а certified Information Security Management System based on ISO 27001.
Rhand holds an MBA in Business Management from Fundação Getúlio Vargas. Among his certifications are ISO 27001 Lead Auditor, ISO 9001 Lead Auditor, Certified Information Security Manager (CISM), Certified Information Systems Security Professional (CISSP), and others. He is a member of the ISACA Brasília Chapter.

You may unsubscribe at any time. For more information, please see our privacy notice.