- Products
Products by framework:
-
ISO 27001
-
NIS 2
-
DORA
-
EU GDPR
-
ISO 9001
-
ISO 14001
-
ISO 45001
-
ISO 13485
-
EU MDR
-
ISO 20000
-
ISO 22301
-
ISO 17025
-
IATF 16949
-
AS9100
-
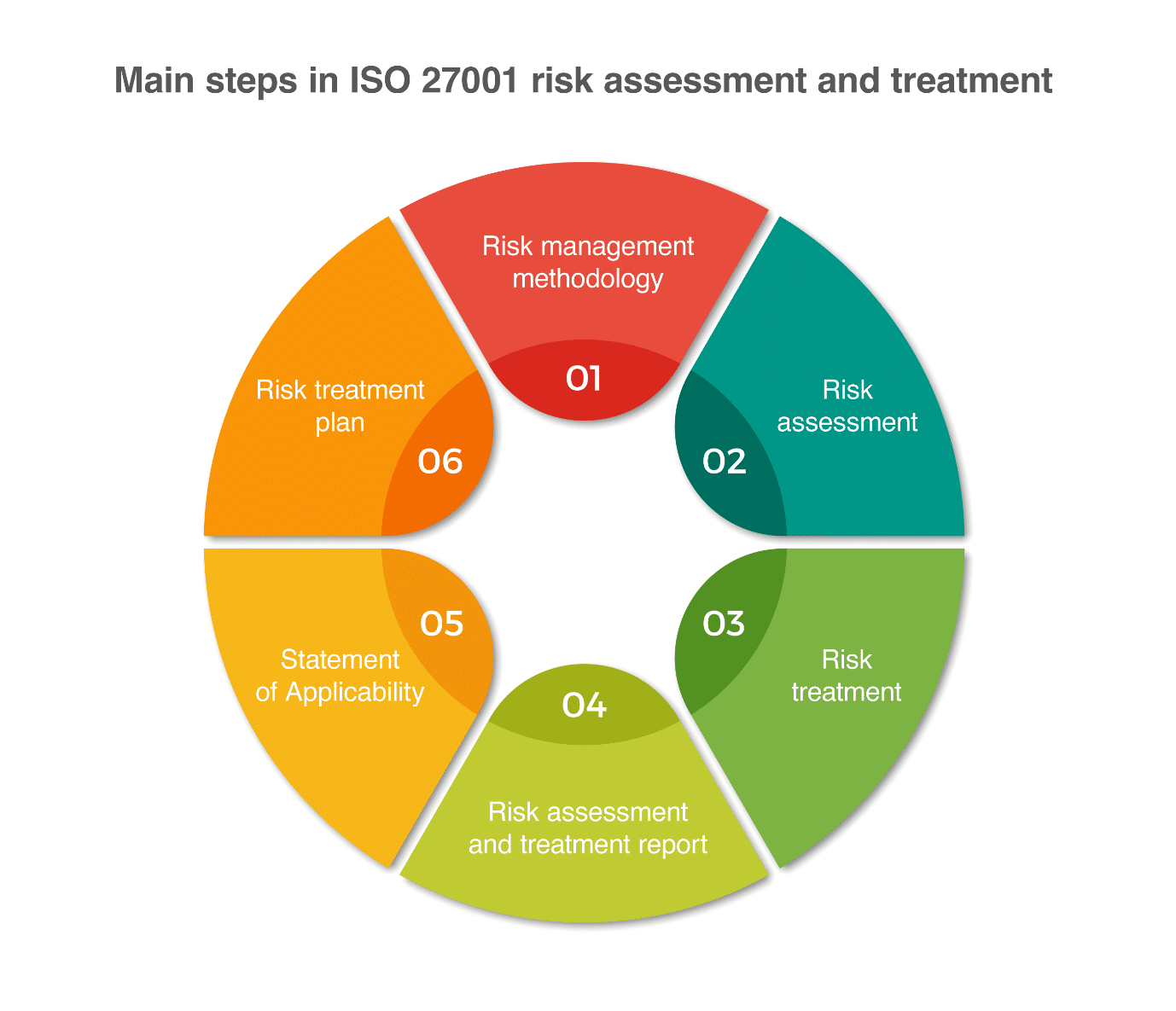
ISO 27001
Implementation, maintenance, training, and knowledge products for Information Security Management Systems (ISMS) according to the ISO 27001 standard.
-
Conformio ISO 27001 Software
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
-
ISO 27001 Documentation Toolkits
All required policies, procedures, and forms to implement an ISMS according to ISO 27001.
-
ISO 27001 Training & Awareness
Train your key people about ISO 27001 requirements and provide cybersecurity awareness training to all of your employees.
-
ISO 27001 Online Courses
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
-
Experta ISO 27001 Knowledge Base
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
-
NIS 2
Compliance and training products for critical infrastructure organizations for the European Union’s Network and Information Systems cybersecurity directive.
-
NIS 2 Documentation Toolkit
All required policies, procedures, and forms to comply with the NIS 2 cybersecurity directive.
-
NIS 2 Cybersecurity Training & Awareness
Company-wide training program for employees and senior management to comply with Article 20 of the NIS 2 cybersecurity directive.
-
DORA
Compliance and training products for financial entities for the European Union’s DORA regulation.
-
DORA Documentation Toolkit
All required policies, procedures, and forms to comply with the DORA regulation.
-
DORA Training & Awareness
Company-wide cybersecurity and resilience training program for all employees, to train them and raise awareness about ICT risk management.
-
DORA Online Courses
Accredited courses for individuals and DORA professionals who want the highest-quality training and certification.
-
EU GDPR
Compliance and training products for personal data protection according to the European Union’s General Data Protection Regulation.
-
EU GDPR Documentation Toolkits
All required policies, procedures, and forms to comply with the EU GDPR privacy regulation.
-
EU GDPR Training & Awareness
Train your key people about GDPR requirements to ensure awareness of data protection principles, privacy rights, and regulatory compliance.
-
EU GDPR Online Courses
Accredited courses for individuals and privacy professionals who want the highest-quality training and certification.
-
ISO 9001
Implementation, training, and knowledge products for Quality Management Systems (QMS) according to the ISO 9001 standard.
-
ISO 9001 Documentation Toolkits
All required policies, procedures, and forms to implement a QMS according to ISO 9001.
-
ISO 9001 Online Courses
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
-
Experta ISO 9001 Knowledge Base
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
-
ISO 14001
Implementation, training, and knowledge products for Environmental Management Systems (EMS) according to the ISO 14001 standard.
-
ISO 14001 Documentation Toolkits
All required policies, procedures, and forms to implement an EMS according to ISO 14001.
-
ISO 14001 Online Courses
Accredited courses for individuals and environmental professionals who want the highest-quality training and certification.
-
Experta ISO 14001 Knowledge Base
Get instant answers to any questions related to ISO 14001 and the EMS using Advisera’s proprietary AI-powered knowledge base.
-
ISO 45001
Implementation and training products for Occupational Health & Safety Management Systems (OHSMS) according to the ISO 45001 standard.
-
ISO 45001 Documentation Toolkits
All required policies, procedures, and forms to implement an OHSMS according to ISO 45001.
-
ISO 45001 Online Courses
Accredited courses for individuals and health & safety professionals who want the highest-quality training and certification.
-
ISO 13485
Implementation and training products for medical device Quality Management Systems (QMS) according to the ISO 13485 standard.
-
ISO 13485 Documentation Toolkits
All required policies, procedures, and forms to implement a medical device QMS according to ISO 13485.
-
ISO 13485 Online Courses
Accredited courses for individuals and medical device professionals who want the highest-quality training and certification.
-
EU MDR
Compliance products for the European Union’s Medical Device Regulation.
-
EU MDR Documentation Toolkits
All required policies, procedures, and forms to comply with the EU MDR.
-
ISO 20000
Implementation products for Information Technology Service Management Systems (ITSMS) according to the ISO 20000 standard.
-
ISO 20000 Documentation Toolkits
All required policies, procedures, and forms to implement an ITSMS according to ISO 20000.
-
ISO 22301
Implementation products for Business Continuity Management Systems (BCMS) according to the ISO 22301 standard.
-
ISO 22301 Documentation Toolkits
All required policies, procedures, and forms to implement a BCMS according to ISO 22301.
-
ISO 17025
Implementation products for testing and calibration laboratories according to the ISO 17025 standard.
-
ISO 17025 Documentation Toolkit
All required policies, procedures, and forms to implement ISO 17025 in a laboratory.
-
IATF 16949
Implementation products for automotive Quality Management Systems (QMS) according to the IATF 16949 standard.
-
IATF 16949 Documentation Toolkits
All required policies, procedures, and forms to implement an automotive QMS according to IATF 16949.
-
AS9100
Implementation products for aerospace Quality Management Systems (QMS) according to the AS9100 standard.
-
AS9100 Documentation Toolkits
All required policies, procedures, and forms to implement an aerospace QMS according to AS9100.
-
- Free ResourcesResources
- Industries
Solutions for industries:
-
Consultants
-
IT & SaaS companies
-
Critical infrastructure
-
Manufacturing
-
Transportation & distribution
-
Education
-
Telecommunications
-
Banking & finance
-
Government
-
Health organizations
-
Medical device
-
Aerospace
-
Automotive
-
Laboratories
-
Implementation, maintenance, training, and knowledge products for consultancies.
-
Conformio for Consultants
Handle multiple ISO 27001 projects by automating repetitive tasks during ISMS implementation.
-
Consultant Toolkits
All required policies, procedures, and forms to implement various standards and regulations for your clients.
-
Company Training Academy for Consultants
Grow your business by organizing cybersecurity and compliance training for your clients under your own brand using Advisera’s learning management system platform.
-
Lead Auditor and Lead Implementer Courses
Accredited DORA, ISO 27001, 9001, 14001, 45001, and 13485 courses for professionals who want the highest-quality training and recognized certification.
-
Experta ISO Knowledge Base
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
-
Consultant Directory
Find new clients, potential partners, and collaborators and meet a community of like-minded professionals locally and globally.
-
IT & SaaS companies
Implementation, maintenance, training, and knowledge products for the IT industry.
-
Conformio ISO 27001 Software
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
-
ISO 27001, 22301, 20000, GDPR, NIS 2 and DORA Documentation Toolkits
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), NIS 2 (critical infrastructure cybersecurity), and DORA (cybersecurity for financial sector).
-
NIS 2, DORA, ISO 27001, GDPR, and Security Awareness Training
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
ISO 27001, DORA and GDPR Online Courses
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
-
Experta ISO 27001 Knowledge Base
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
-
Critical infrastructure
Compliance, training, and knowledge products for essential and important organizations.
-
NIS 2, GDPR, ISO 27001, and ISO 22301 Documentation Toolkits
Documentation to comply with NIS 2 (cybersecurity), GDPR (privacy), ISO 27001 (cybersecurity), and ISO 22301 (business continuity).
-
NIS 2, GDPR, and Cybersecurity Training & Awareness
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
ISO 27001 and GDPR Online Courses
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
-
Experta ISO 27001 Knowledge Base
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
-
Manufacturing
Implementation, training, and knowledge products for manufacturing companies.
-
ISO 9001, 14001, 45001, and NIS 2 Documentation Toolkits
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
-
NIS 2 and Security Awareness Training
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
ISO 9001, 14001, and 45001 Online Courses
Accredited courses for individuals and professionals who want the highest-quality training and certification.
-
Experta ISO 9001 and 14001 Knowledge Base
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
-
Transportation & distribution
Implementation, training, and knowledge products for transportation & distribution companies.
-
ISO 9001, 14001, 45001, and NIS 2 Documentation Toolkits
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
-
NIS 2 and Security Awareness Training
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
ISO 9001, 14001, and 45001 Online Courses
Accredited courses for individuals and professionals who want the highest-quality training and certification.
-
Experta ISO 9001 and 14001 Knowledge Base
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
-
Education
Implementation, training, and knowledge products for schools, universities, and other educational organizations.
-
ISO 27001, 9001, and GDPR Documentation Toolkits
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), and GDPR (privacy).
-
ISO 27001, GDPR, and Security Awareness Training
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
ISO 27001, 9001, and GDPR Online Courses
Accredited courses for individuals and professionals who want the highest-quality training and certification.
-
Experta ISO 27001 and 9001 Knowledge Base
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
-
Telecommunications
Implementation, maintenance, training, and knowledge products for telecoms.
-
Conformio ISO 27001 Software
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
-
ISO 27001, 22301, 20000, GDPR, and NIS 2 Documentation Toolkits
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
-
NIS 2, GDPR, ISO 27001, and Security Awareness Training
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
ISO 27001 and GDPR Online Courses
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
-
Experta ISO 27001 Knowledge Base
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
-
Banking & finance
Implementation, maintenance, training, and knowledge products for banks, insurance companies, and other financial organizations.
-
Conformio ISO 27001 Software
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
-
DORA, ISO 27001, 22301 and GDPR Documentation Toolkits
Documentation to comply with DORA (cybersecurity for financial sector), ISO 27001 (cybersecurity), ISO 22301 (business continuity), and GDPR (privacy).
-
DORA, NIS 2, GDPR, ISO 27001, and Security Awareness Training
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
DORA, ISO 27001 and GDPR Online Courses
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
-
Experta ISO 27001 Knowledge Base
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
-
Government
Implementation, training, and knowledge products for local, regional, and national government entities.
-
ISO 27001, 9001, GDPR, and NIS 2 Documentation Toolkits
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
-
NIS 2, ISO 27001, GDPR, and Security Awareness Training
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
ISO 27001, 9001, and GDPR Online Courses
Accredited courses for individuals and professionals who want the highest-quality training and certification.
-
Experta ISO 27001 and 9001 Knowledge Base
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
-
Health organizations
Implementation, training, and knowledge products for hospitals and other health organizations.
-
ISO 27001, 9001, 14001, 45001, NIS 2, and GDPR Documentation Toolkits
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
-
NIS 2, GDPR, and Security Awareness Training
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
ISO 27001, 9001, 14001, 45001, and GDPR Online Courses
Accredited courses for individuals and professionals who want the highest-quality training and certification.
-
Experta ISO 27001, 9001, and 14001 Knowledge Base
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
-
Medical device
Implementation, training, and knowledge products for the medical device industry.
-
ISO 13485, 27001, 9001, 14001, 45001, NIS 2, and GDPR Documentation Toolkits
Documentation to comply with MDR and ISO 13485 (medical device), ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
-
NIS 2, ISO 27001, GDPR, and Security Awareness Training
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
ISO 13485, 27001, 9001, 14001, 45001, and GDPR Online Courses
Accredited courses for individuals and professionals who want the highest-quality training and certification.
-
Experta ISO 27001, 9001, and 14001 Knowledge Base
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
-
Aerospace
Implementation, training, and knowledge products for the aerospace industry.
-
AS9100, ISO 9001, 14001, 45001, and NIS 2 Documentation Toolkits
Documentation to comply with AS9100 (aerospace), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
-
NIS 2 and Security Awareness Training
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
ISO 9001, 14001, and 45001 Online Courses
Accredited courses for individuals and professionals who want the highest-quality training and certification.
-
Experta ISO 9001 and 14001 Knowledge Base
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
-
Automotive
Implementation, training, and knowledge products for the automotive industry.
-
IATF 16949, ISO 9001, 14001, 45001, and NIS 2 Documentation Toolkits
Documentation to comply with IATF 16949 (automotive), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
-
NIS 2, ISO 27001, and Security Awareness Training
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
ISO 9001, 14001, and 45001 Online Courses
Accredited courses for individuals and professionals who want the highest-quality training and certification.
-
Experta ISO 9001 and 14001 Knowledge Base
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
-
Laboratories
Implementation, training, and knowledge products for laboratories.
-
ISO 17025, 9001, and NIS 2 Documentation Toolkits
Documentation to comply with ISO 17025 (testing and calibration laboratories), ISO 9001 (quality), and NIS 2 (critical infrastructure cybersecurity).
-
NIS 2 and Security Awareness Training
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
-
ISO 9001 Online Courses
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
-
Experta ISO 9001 Knowledge Base
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
-
- About Us
ISO 27001 Expert - About Us
- Contact Us




 Dejan Kosutic
Dejan Kosutic