Tolga Aktaş
Tolga Aktaş
October 27, 2021
Implementation, maintenance, training, and knowledge products for Information Security Management Systems (ISMS) according to the ISO 27001 standard.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
All required policies, procedures, and forms to implement an ISMS according to ISO 27001.
Train your key people about ISO 27001 requirements and provide cybersecurity awareness training to all of your employees.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance and training products for critical infrastructure organizations for the European Union’s Network and Information Systems cybersecurity directive.
All required policies, procedures, and forms to comply with the NIS 2 cybersecurity directive.
Company-wide training program for employees and senior management to comply with Article 20 of the NIS 2 cybersecurity directive.
Compliance and training products for financial entities for the European Union’s DORA regulation.
All required policies, procedures, and forms to comply with the DORA regulation.
Company-wide cybersecurity and resilience training program for all employees, to train them and raise awareness about ICT risk management.
Accredited courses for individuals and DORA professionals who want the highest-quality training and certification.
Compliance and training products for personal data protection according to the European Union’s General Data Protection Regulation.
All required policies, procedures, and forms to comply with the EU GDPR privacy regulation.
Train your key people about GDPR requirements to ensure awareness of data protection principles, privacy rights, and regulatory compliance.
Accredited courses for individuals and privacy professionals who want the highest-quality training and certification.
Implementation, training, and knowledge products for Quality Management Systems (QMS) according to the ISO 9001 standard.
All required policies, procedures, and forms to implement a QMS according to ISO 9001.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for Environmental Management Systems (EMS) according to the ISO 14001 standard.
All required policies, procedures, and forms to implement an EMS according to ISO 14001.
Accredited courses for individuals and environmental professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 14001 and the EMS using Advisera’s proprietary AI-powered knowledge base.
Implementation and training products for Occupational Health & Safety Management Systems (OHSMS) according to the ISO 45001 standard.
All required policies, procedures, and forms to implement an OHSMS according to ISO 45001.
Accredited courses for individuals and health & safety professionals who want the highest-quality training and certification.
Implementation and training products for medical device Quality Management Systems (QMS) according to the ISO 13485 standard.
All required policies, procedures, and forms to implement a medical device QMS according to ISO 13485.
Accredited courses for individuals and medical device professionals who want the highest-quality training and certification.
Compliance products for the European Union’s Medical Device Regulation.
All required policies, procedures, and forms to comply with the EU MDR.
Implementation products for Information Technology Service Management Systems (ITSMS) according to the ISO 20000 standard.
All required policies, procedures, and forms to implement an ITSMS according to ISO 20000.
Implementation products for Business Continuity Management Systems (BCMS) according to the ISO 22301 standard.
All required policies, procedures, and forms to implement a BCMS according to ISO 22301.
Implementation products for testing and calibration laboratories according to the ISO 17025 standard.
All required policies, procedures, and forms to implement ISO 17025 in a laboratory.
Implementation products for automotive Quality Management Systems (QMS) according to the IATF 16949 standard.
All required policies, procedures, and forms to implement an automotive QMS according to IATF 16949.
Implementation products for aerospace Quality Management Systems (QMS) according to the AS9100 standard.
All required policies, procedures, and forms to implement an aerospace QMS according to AS9100.
Implementation, maintenance, training, and knowledge products for consultancies.
Handle multiple ISO 27001 projects by automating repetitive tasks during ISMS implementation.
All required policies, procedures, and forms to implement various standards and regulations for your clients.
Grow your business by organizing cybersecurity and compliance training for your clients under your own brand using Advisera’s learning management system platform.
Accredited Lead Auditor and Lead Implementer courses for ISO standards and DORA, and an advanced course to help consultants grow their business.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Find new clients, potential partners, and collaborators and meet a community of like-minded professionals locally and globally.
Implementation, maintenance, training, and knowledge products for the IT industry.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), NIS 2 (critical infrastructure cybersecurity), and DORA (cybersecurity for financial sector).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance, training, and knowledge products for essential and important organizations.
Documentation to comply with NIS 2 (cybersecurity), GDPR (privacy), ISO 27001 (cybersecurity), and ISO 22301 (business continuity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for manufacturing companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for transportation & distribution companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for schools, universities, and other educational organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for telecoms.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for banks, insurance companies, and other financial organizations.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with DORA (cybersecurity for financial sector), ISO 27001 (cybersecurity), ISO 22301 (business continuity), and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for local, regional, and national government entities.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for hospitals and other health organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the medical device industry.
Documentation to comply with MDR and ISO 13485 (medical device), ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the aerospace industry.
Documentation to comply with AS9100 (aerospace), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the automotive industry.
Documentation to comply with IATF 16949 (automotive), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for laboratories.
Documentation to comply with ISO 17025 (testing and calibration laboratories), ISO 9001 (quality), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
 Tolga Aktaş
Tolga Aktaş
In the past, working from home was an option for freelancers and companies who were willing to cut operational costs and improve employee work-life balance. But COVID-19 has changed the way we work and forced many companies to adapt quickly and support remote working. They had to create a virtual work environment that allowed teleworking to be productive and keep their jobs safe, while also addressing the information security challenges of remote work.
With the help of the requirements of ISO 27001 for information security risk management, and the security controls of its Annex A, this task can become less complex and allow you to take full advantage of teleworking with the least risk.
Besides its many benefits, remote working has some challenges and information security risks. These include unauthorized access, breach of sensitive information, and modification or even destruction of data. Considering that employees are outside the organization’s environment, they will be using mobile devices for remote access from home or public networks, which may not have the best security controls. Insufficient information and communication policies, along with a lack of clearly defined procedures, can cause nightmares for companies, including financial loss and non-compliance with regulations such as the EU GDPR.
An Information Security Management System based on ISO 27001 requirements and controls helps us to take precautions against these information security risks. ISO 27001 consists of 10 sections and reference control objectives and controls stated in Annex A of the standard. There is also another standard, ISO 27002, which is a code of practice for those controls.
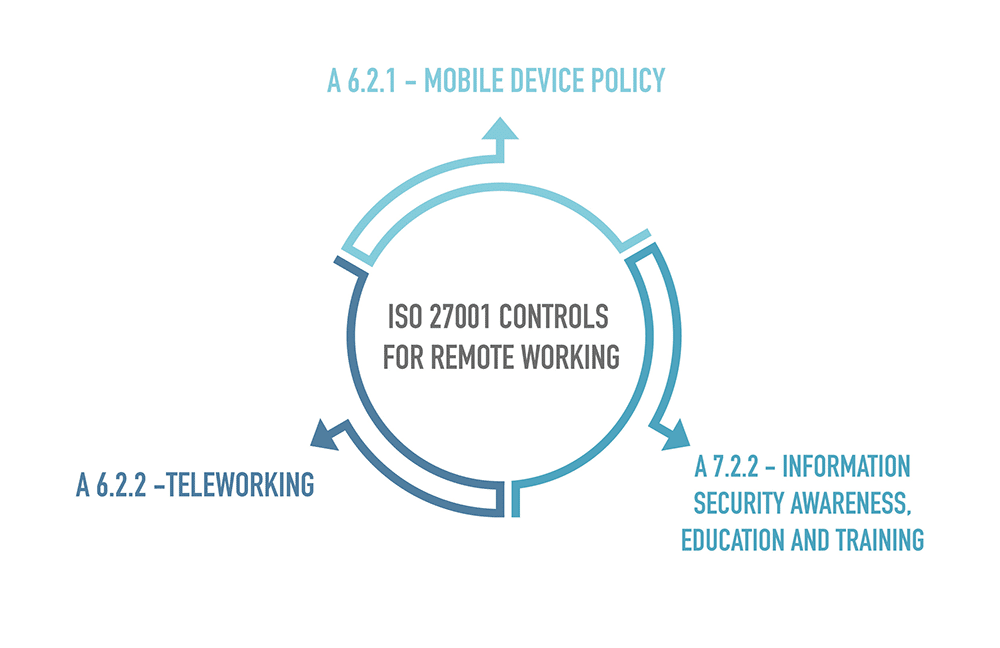
Two of the controls from ISO 27001/ISO 27002 are dedicated to teleworking: A.6.2.1 Mobile device policy, and A.6.2.2 Teleworking.
Teleworking. Control A 6.2.2 states that a policy that defines conditions and restrictions for teleworking should be issued by the organization:
Also, control A.7.2.2 states that all employees of the organization must have appropriate awareness and regularly updated training in order to ensure that policies and procedures are implemented correctly.
No matter what industry you work in, at some point your organization, or at least part of it, will start relying on telework. But, by exposing your infrastructure, systems, and information in this way, your organization needs to take precautions for the high risks involved.
First, devices or users that do not comply with mobile device and teleworking policies should not be allowed to connect. Therefore, organizations must define who may telework and have remote access to which systems and data.
Using a virtual private network (VPN) and 2-factor authentication will improve endpoint security. Scanning network traffic for unusual activities by using a network layer firewall and encrypting sensitive data and communication will enhance security. Continuous monitoring, penetration tests, and audits will help you detect your vulnerabilities and shift your information security strategy.
Data clearance based on the need-to-know principle will prevent intended or unintended compromise of data. This is best provided by restricting the access rights of remote workers only to those systems and information they require for their organizational roles.
To learn more about remote access in teleworking, please read this article: ISO 27001 remote access policy: How to develop it.
It is essential to create sustainable awareness and to stay ISO 27001-compliant with remote workers. ISO 27001 clause 7.2 and control A 7.2.2 put further emphasis on this aspect. A regular and updated training program on policies and procedures regarding teleworking is necessary. Awareness activities can be in any form, including meetings, web-based trainings, use of company intranet, and others. However, it is important to state management’s commitment to information security, the need to comply with information security controls, and remote workers’ accountability for their own actions. It is also essential to assess the understanding of participants after awareness-raising activities. To improve the security awareness of your remote workers, enroll in this free security awareness training – a series of easy-to-understand videos for any employee.
The following methods will also increase awareness and create a safer teleworking environment:
As we have seen, remote work increasingly becoming a part of work life has its advantages. On the other hand, it may cause many problems both for individuals and companies. For all, preference of applying ISO 27001 and its controls will help to switch to remote work easily. Work from home, but safely!
To see how employees can collaborate on ISO 27001 ISMS implementation steps, documents, and all the necessary tasks, sign up for a 14-day free trial of Conformio, the leading ISO 27001 compliance software.

Tolga Aktaş has been working in various disciplines of management systems for more than 15 years. Tolga is an accredited lead auditor for the ISO 9001, 14001, 18295, 22301, 27001, 27701, 37001, and 55001 standards and has conducted audits as a freelancer for internationally accredited conformity assessment companies. He is also an accredited lead auditor trainer for ISO 22301, 27001, and 27701. He conducts workshops and webinars, and provides consultancy services on management systems to organizations mainly in Turkey, the UK, the EU, Qatar, UAE, Germany, and Japan. Tolga holds a Master of Business Administration degree.
You may unsubscribe at any time. For more information, please see our privacy notice.