There is no doubt that companies are investing lots of money in cybersecurity lately – of course they are: with so many data breaches and expectations from key clients, this becomes a necessity in doing business. However, most of these cybersecurity investments are perceived to be purely IT costs, very often overhead, with little or no business benefit. So, is cybersecurity nothing but one of those mandatory things that no one likes, or can it produce some greater business good?
I’m arguing that yes – cybersecurity can help companies achieve much more than only produce a cost: it can help companies achieve sustainable competitive advantage, much like Apple is using it to differentiate itself from competitors by placing a much greater emphasis on the protection of personal data of users of its mobile devices and cloud services.
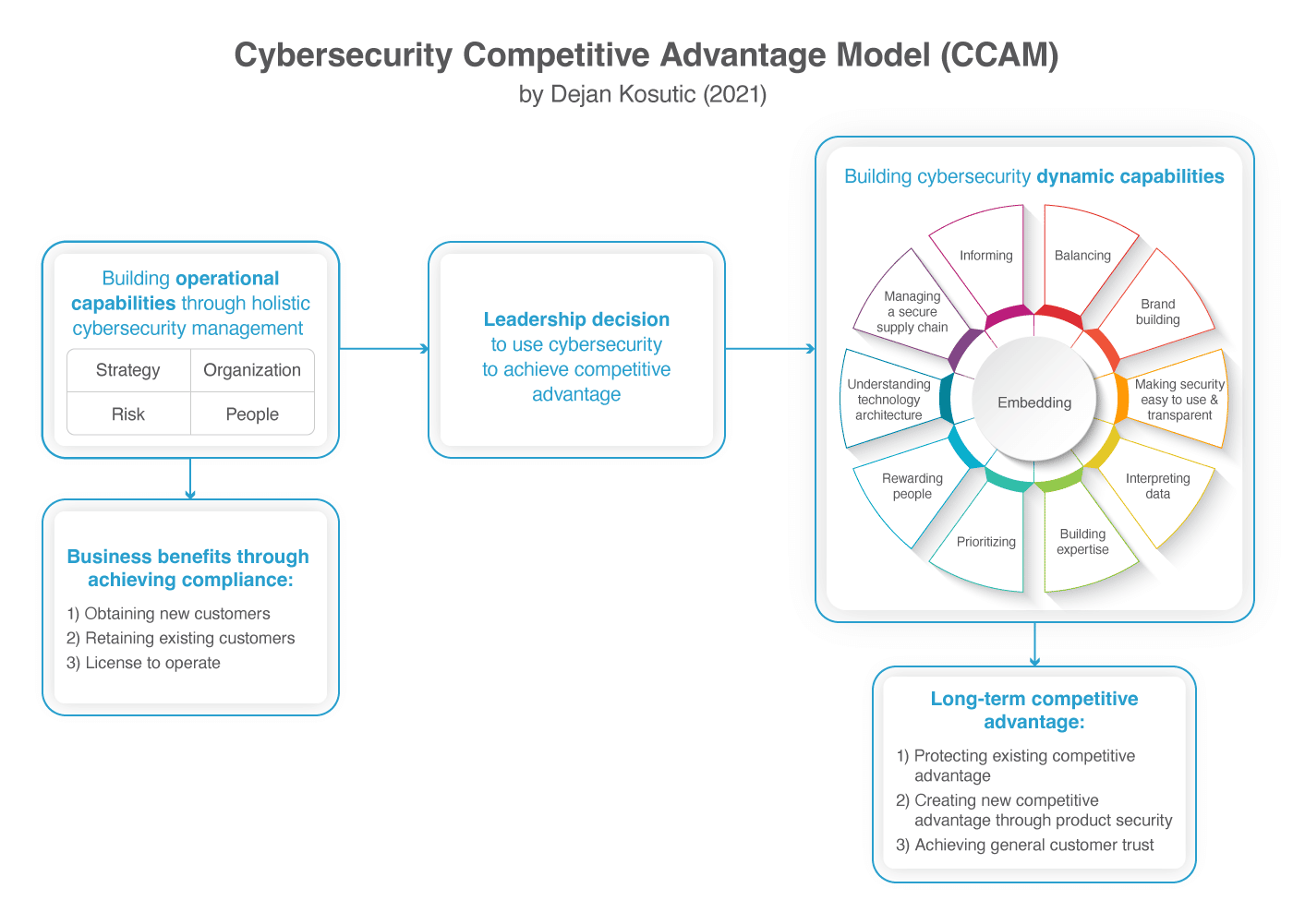
- Protecting existing competitive advantage
- Creating new competitive advantage through product security
- Achieving general customer trust
Most companies associate cybersecurity with compliance
In reality, most companies that invest in cybersecurity do so because of compliance – they want to become compliant with ISO 27001, SOC 2, NIST Cybersecurity Framework, PCI DSS, or some other standard or regulation.
They do so because they want to achieve some of the following:
- Get new clients – by certifying against, e.g., ISO 27001, they can get a contract with a new client who is very sensitive about keeping their data safe, especially if other bidders competing for the same client do not have such certificate.
- Keep existing clients – if a software company has a very important client who requires, e.g., SOC 2 compliance as a condition to renew their contract, then compliance becomes a tool to keep the client.
- Obtain a license to operate in a certain market – for example, if a company wants to collect credit card information, it must be compliant with PCI DSS; otherwise, it will not be allowed to perform these activities.
In other words, cybersecurity compliance will either bring new sources of revenue to companies, or prevent a loss of revenue – this kind of argument is something that every CEO likes to hear.
This kind of approach is fine if a company has a short-term view; however, compliance will not provide a long-term competitive advantage because competitors will find it rather easy to comply with the same standards and regulations, and then compliance will no longer provide advantage in the marketplace.
Why is this so?
Key elements for achieving cybersecurity compliance
When companies want to be successful in their compliance projects, they should not focus on technology alone; rather, they need to manage cybersecurity in a holistic way and balance 4 key aspects:
- The strategic aspect means that the security personnel need to learn about the company’s mission, vision, and strategy, and direct security activities to support these business goals. With such an approach, companies can find market opportunities that did not exist before.
- The organizational aspect means that companies need to use policies and procedures to define security governance, introduce interdepartmental coordination on security-related activities, have an independent person or organizational unit that manages security, use project management techniques, and be prepared to go through continuous organizational changes.
- The people aspect includes showing the top management’s commitment to security, implementing security awareness and training, and using adequate communication channels to explain security – all of these will contribute to building up a security culture.
- The risk management & technological aspect includes finding out which risks exist related to the company’s sensitive information, and then defining which IT, legal, organizational, human resource, and physical safeguards are needed to mitigate those risks.
In other words, if a company focuses on, e.g., technology, and neglects other aspects, their cybersecurity compliance project will most likely fail because they will be missing certain “ingredients” crucial for the success of such projects. On the other hand, companies that balance all four key aspects will find compliance projects much easier to manage.
And this will be enough for most companies – if they only want to achieve the compliance benefits and do not have the ambition to use cybersecurity for something else.
However, very soon they will not be alone – competitors will hire a consultant or will use some kind of cybersecurity tool to run cybersecurity projects. This means they will be able to acquire the operational capabilities needed to manage the four key aspects listed above rather easily, and any competitive advantage created by compliance will erode just as quickly.
So, is cybersecurity only a temporary fix?
Long-term competitive advantage from cybersecurity
For companies that want more from cybersecurity, their top management needs to make a strategic decision to build up new capabilities that will push the company beyond the four aspects explained in the previous section.
Why would the executives make such a big effort? Because they could outmatch their competitors not only in the short term, but achieve a long-term competitive advantage by achieving 3 specific strategic values:
Protecting existing competitive advantage. Since intellectual property is the basis of competitive advantage for lots of companies (e.g., high-tech, pharmaceuticals, etc.), the leakage of such information could ruin a company; so, when cybersecurity becomes part of strategic decision making, it can prevent costly business decisions and protect intellectual property and trade secrets. When I interviewed a CISO of a high-tech company, he explained that his company planned to open a research facility in a country where the government controls the flow of data through the Internet; when he presented the possibility that their sensitive R&D information might leak to local competitors because of their connections with the government, the board of the company abandoned the idea of expanding into this country and, by doing so, kept their most valuable asset better protected.
Creating new competitive advantage through product security. Markets are extremely competitive, and companies find it very hard to offer features that their competitors do not have; when cybersecurity becomes part of product development, it stimulates companies to invest more in R&D because companies are assured their innovations will be better protected against leakage to competitors. Even more importantly, cybersecurity enables companies to create security features that appeal to customers, and such differentiation enables them to obtain a long-term source of revenue. For example, Apple invests a lot in data security (e.g., biometrics) and privacy (e.g., limiting access to personal data) because these features are in great demand from a large group of customers – these features, together with others (e.g., ease of use, design, etc.) enable Apple to gain a sizeable market share with high-priced products like the iPhone.
Achieving general customer trust. The willingness of customers to purchase products and services is directly related to their trust in a company, in its brand. When cybersecurity becomes embedded in the everyday processes of a company, it significantly decreases the risk of data breaches and unavailability of their services, both of which would erode customer trust in the company. Further, when cybersecurity becomes part of marketing and communication efforts, the customers who are sensitive about how their data are handled will gain more trust in the company. For example, a manager explained to me how their company is measuring several attributes of the trust in their brand (including security), and then investing more in communicating attributes that increase the chance of converting new customers.
When companies achieve any of these three strategic goals, competitors will find it much more difficult to imitate them. So, what do companies need to do to achieve this sustainable competitive advantage?
Cybersecurity dynamic capabilities for achieving competitive advantage
To be able to achieve long-term competitive advantage, companies must develop specific capabilities that competitors will not be able to match in the short term – these are called cybersecurity dynamic capabilities, and through my research I found that successful companies have the following 11 capabilities:
- Informing – the ability of an organization to disseminate security-relevant information to all concerned actors within the organization and its supply chain.
- Understanding technology architecture – the ability to recognize the direction in which the security technology is developing, and the company’s ability to choose the appropriate technology accordingly.
- Making security easy to use & transparent – the ability to present and implement security rules and technology in such a way that anyone, even a layperson, knows exactly why they exist, and how to use them.
- Brand building – the ability to embed trust as a key feature of their brand.
- Balancing security and business – the ability to apply an optimal number of safeguards strong enough to address security risks, while being unobtrusive enough not to interfere with regular operations.
- Managing a secure supply chain – the ability to keep data secure even when that data are not under the direct control of the company.
- Prioritizing – the ability to focus on the most important cybersecurity activities and products in order to achieve strategic priorities.
- Building expertise – the ability to build cybersecurity know-how within the company in order to get highly satisfied clients and protect their data.
- Rewarding people – the ability to use KPIs and other measurement methods to stimulate security-relevant actors to contribute to the company’s cybersecurity.
- Interpreting data – the ability to find patterns and trends in large amounts of data in order to make informed security decisions.
- Embedding – the ability to make employees use security rules and technology as part of their regular daily operations.
Achieving all 11 of these capabilities is quite a challenge, but I’ve seen companies that have developed at least a couple of them to build a good foundation for long-term competitive advantage.
Cybersecurity Competitive Advantage Model
To summarize, the Cybersecurity Competitive Advantage Model (CCAM) displayed below explains how four key aspects of managing cybersecurity compliance are related to short-term benefits, and what companies need to do to obtain long-term competitive advantage through cybersecurity.
Cybersecurity has come a long way – until only a couple of years ago it was an “IT thing” that only tech departments understood, and was only a black box, while in recent years managers came to realize that they could achieve some business benefits by becoming compliant with cybersecurity standards and regulations.
But will companies go a step further and use cybersecurity for building a sustainable competitive advantage? Rare visionary companies like Apple are doing it, and it remains to be seen if this will become mainstream.
To implement ISO 27001 easily and efficiently, sign up for a free trial of Conformio, the leading ISO 27001 compliance software.
This article is based on Dejan Kosutic’s research that is published in his doctoral thesis “The Impact of Cybersecurity on Competitive Advantage.”

 Dejan Kosutic
Dejan Kosutic