Updated: December 12, 2022., according to the ISO 27001:2022 revision.
Annex A of ISO 27001 is probably the most famous annex of all the ISO standards – this is because it provides an essential tool for managing information security risks: a list of security controls (or safeguards) that are to be used to improve the security of information assets.
This article will provide you with an understanding of how Annex A is structured, as well as its relationship with the main part of ISO 27001, and with ISO 27002.
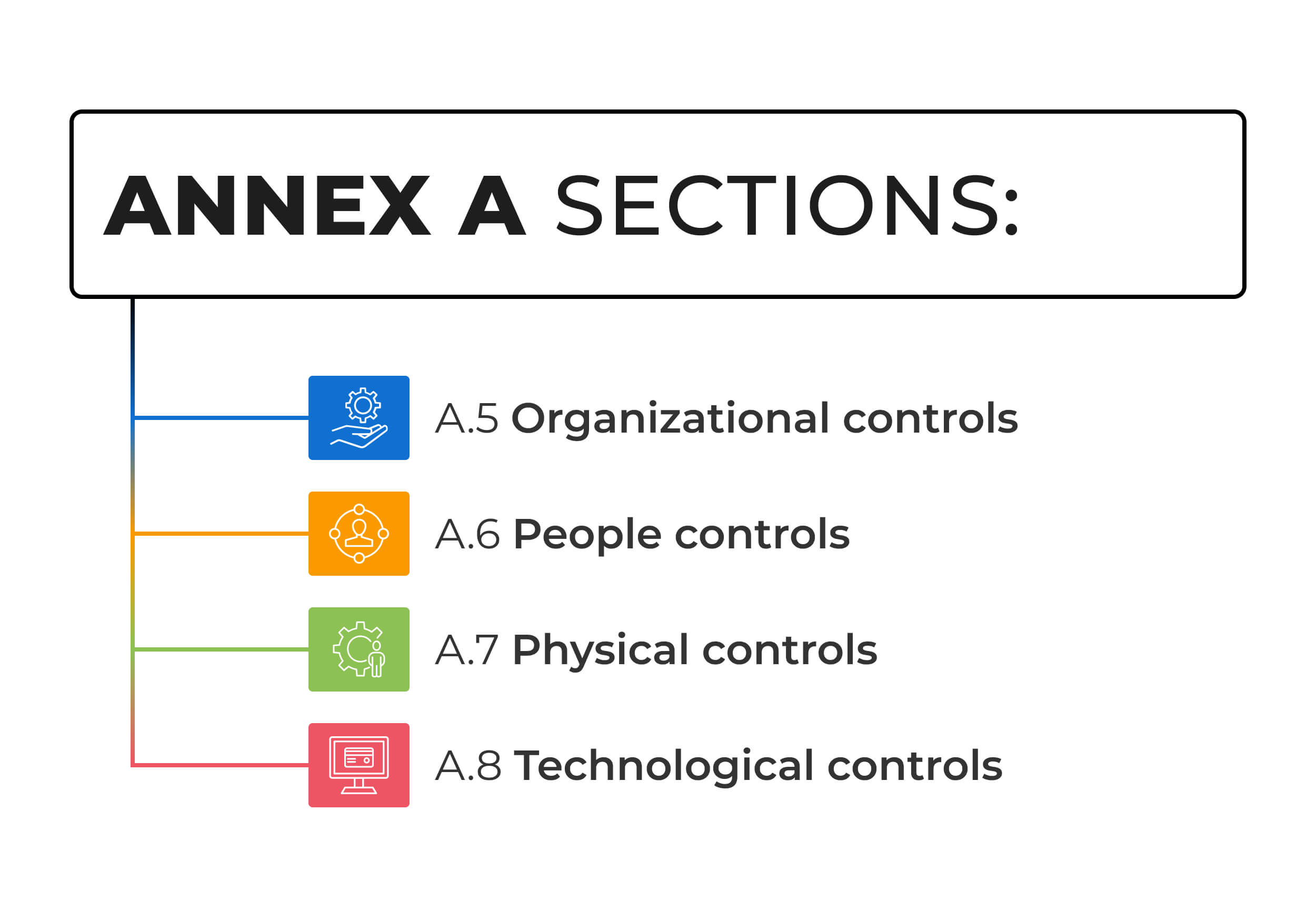
- A.5 Organizational controls
- A.6 People controls
- A.7 Physical controls
- A.8 Technological controls
How many domains are there in ISO 27001?
The ISO 27001 controls list can be found in Annex A, and it is organized into four sections (domains). Contrary to what one might think, these are not all IT oriented – the standard strikes a balance between organizational, people, physical, and technological controls.
What are the four domains of ISO 27001?
Here’s a short description of each of the four sections:
- A.5 Organizational controls: This section contains controls for setting the most important security processes and documentation.
- A.6 People controls: This section focuses on controls related to secure management of human resources.
- A.7 Physical controls: This section defines controls related to secure areas and equipment protection.
- A.8 Technological controls: This section focuses on IT and communication controls.
How many controls does ISO 27001 have?
There are 93 ISO 27001 information security controls listed in Annex A of the current 2022 revision of the standard (compared to 114 from the previous 2013 revision of the standard). Here is a breakdown of what types of controls are included:
- Controls related to organizational issues: 37
- Controls related to human resources: 8
- IT-related controls: 34
- Controls related to physical security: 14
The best way to understand Annex A is to think of it as a catalogue of information security controls you can select from – out of the 93 controls that are listed in Annex A, you can choose the ones that are applicable to your company’s scope. Another approach is to use Annex A as an ISO 27001 controls checklist, for an initial evaluation of your organization’s readiness for information security management process.
Relationship with ISO 27001 main clauses
Not all of these ISO 27001:2022 controls are mandatory – organizations can choose for themselves which controls they find applicable, and then they must implement them (in most cases, at least 90% of the controls are applicable); the rest are declared to be non-applicable. For example, control A.8.30 Outsourced development can be marked as non-applicable if a company does not outsource the development of software. The main criterion for selecting the controls is through risk management, which is defined in clauses 6 and 8 of the main part of ISO 27001. Learn more here: ISO 27001 Risk Assessment, Treatment, & Management: The Complete Guide.
Further, clause 5 of the main part of ISO IEC 27001 requires you to define responsibilities for managing those controls, and clause 9 requires you to measure if the controls have fulfilled their purpose. Finally, clause 10 requires you to fix anything that is wrong with those controls, and to make sure that you achieve information security objectives with those controls.
What is the difference between ISO 27001 and ISO 27002?
The truth is that Annex A of ISO27001 does not give much detail about each control. There is usually one sentence for each control, which gives you an idea of what you need to achieve, but not how to do it.
This is why ISO 27002 was published – it has exactly the same structure as ISO 27001 Annex A: each control from Annex A exists in ISO 27002, but it has a much more detailed explanation on how to implement it. But, don’t fall into the trap of using only ISO 27002 for managing your information security risks – it does not give you any clues as to how to select which controls to implement, how to measure them, how to assign responsibilities, etc. Learn more here: ISO 27001 vs. ISO 27002.
Usability of Annex A
There are a couple of things I like about Annex A – it gives you a perfect overview of which controls you can apply so that you don’t forget some that would be important, and it gives you the flexibility to choose only the ones you find applicable to your business so that you don’t have to waste resources on the ones that are not relevant to you.
It is true that Annex A doesn’t give you much detail on implementation, but this is where ISO 27002 comes in; it is also true that some companies might abuse the flexibility of ISO-27001 and aim only for the minimum controls in order to pass the certification, but this is a topic for a different blog post.
To implement policies and procedures for ISO 27001 Annex A controls, sign up for a free trial of Conformio, the leading ISO 27001 compliance software.

 Rhand Leal
Rhand Leal 


