TABLE OF CONTENTS
Who does NIS2 apply to? What are essential and important entities, and what is the difference? What is the structure of NIS 2? What are the main cybersecurity requirements of NIS 2? What are the reporting obligations of essential and important entities? How to implement cybersecurity according to NIS 2
Updated on February 08, 2025 (transposition in Member States)
NIS2 Directive summary
The “NIS 2 Directive,” or simply “NIS2,” is a European Union directive that specifies cybersecurity requirements that need to be implemented by EU companies that are considered to be critical infrastructure.
Its full name is “Directive (EU) 2022/2555 on measures for a high common level of cybersecurity across the Union,” and it was published on December 14, 2022.
Since NIS 2 is a directive, this means that each EU country will define its own cybersecurity laws based on NIS 2, whereas NIS 2 specifies the minimum level of cybersecurity to be achieved. In practice, this means that companies in some countries will have to comply with the minimum specified in NIS 2, and in other countries they will have to comply with more strict cybersecurity requirements specified in local laws.
NIS 2 has the mark “2” because it replaces the old NIS directive.
The NIS2 Directive could become for cybersecurity what the EU GDPR has become for privacy — a worldwide standard that other countries use as a best practice for their own legislation.
What is the old NIS directive, and how is NIS 2 different?
The old NIS directive (Directive 2016/1148) also specified cybersecurity for critical infrastructure, but it did not manage to introduce the same level of cybersecurity across all Member States, resulting in a fragmented approach.
The new NIS2 introduces a wider array of industries (sectors) that must be compliant, better cooperation between the Member States, new timelines for reporting incidents, more focus on supply chains, the responsibility on the top management of entities, stricter penalties, etc.
NIS 2 replaces the old NIS on October 18, 2024.
What does “NIS” stand for?
The full title of the old NIS directive was: “Directive (EU) 2016/1148 concerning measures for a high common level of security of network and information systems across the Union.”
Therefore, “NIS” is an abbreviation of “Network and Information Systems.”
Why is NIS 2 important?
NIS 2 is important because it sets very strict cybersecurity requirements for a large number of companies in the European Union – by some estimates, more than 100,000 companies in the European Union will have to become NIS 2 compliant.
Even though NIS 2 does not apply to as many companies as, e.g., the EU GDPR, it will certainly become a de facto standard for critical infrastructure that other (non-EU) countries will emulate – a very similar scenario has happened already in non-EU countries with privacy regulations that are very similar to the EU GDPR.
Where can I find the full text of NIS 2?
You can find the official text here: https://eur-lex.europa.eu/eli/dir/2022/2555.
You can also find the full text here, arranged by chapters and articles, and with the ability to search by keyword: Full Text of NIS 2 Directive.
When does NIS2 come into effect?
NIS 2 will take effect on October 18, 2024 – this is also the deadline for EU countries to define their own laws and regulations based on NIS 2.
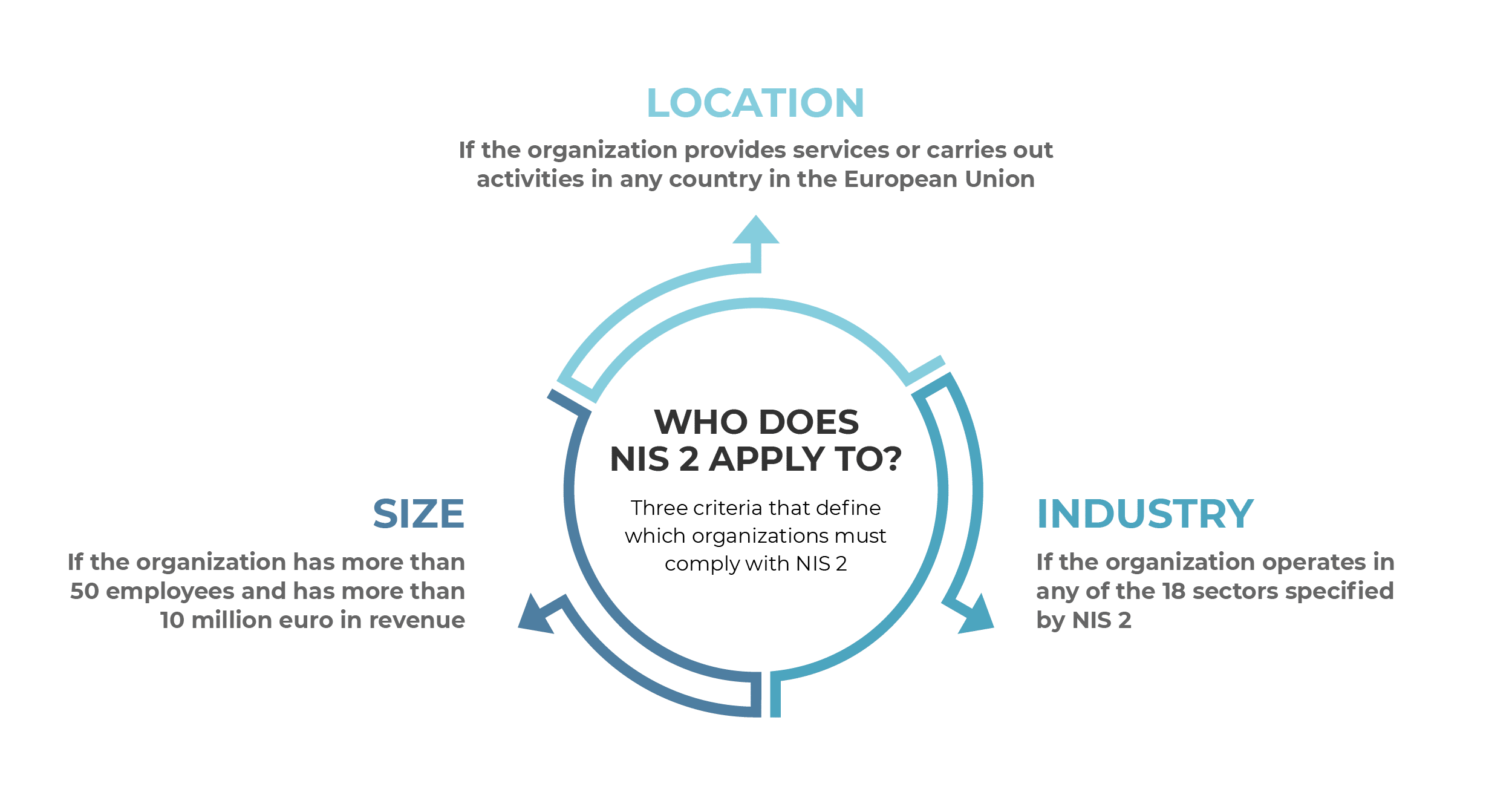
Who does NIS2 apply to?
There are 3 criteria that define which organizations (NIS 2 calls them “essential entities” and “important entities”) must comply with NIS 2:
- 1) Location – if they provide services or carry out activities in any country of the European Union (no matter if they are based in the EU or not); and
- 2) Size – if they have more than 50 employees and have more than 10 million euro in revenue; and
- 3) Industry – if they operate in any of these sectors:
- Energy
- Transport
- Banking
- Financial market infrastructures
- Health
- Drinking water
- Waste water
- Digital infrastructure
- ICT service management (business-to-business)
- Public administration
- Space
- Postal and courier services
- Waste management
- Manufacture, production, and distribution of chemicals
- Production, processing, and distribution of food
- Manufacturing
- Digital providers
- Research
This article will provide you with a detailed breakdown on companies that must be compliant in each sector: Which companies must comply with NIS 2? Essential vs. important entities.
What are essential and important entities, and what is the difference?
“Essential entities” and “important entities” are what NIS 2 calls companies and other organizations that need to comply with NIS 2.
Essential entities are as follows:
- Companies that have more than 250 employees or 50 million euro of revenue and that are in one of the following sectors: energy, transport, banking, financial market infrastructures, health, drinking water, waste water, digital infrastructure, ICT service management (business-to-business), public administration, or space
- Trust service providers
- DNS service providers
- Public electronic communication networks
- Public administration entities
- Any critical entity according to Critical Entities Resilience (CER) Directive (EU) 2022/2557
- Other entities specified by Member States
Important entities are all other organizations that are not essential entities, but that fall under the 3 criteria mentioned in the previous section.
What is the structure of NIS 2?
NIS 2 starts with a preamble where, in 144 points, it explains the background and provides some guidelines for the main part of the Directive. The main part of NIS 2 has 46 articles that are structured in the following chapters:
- Chapter I — General provisions
- Chapter II — Coordinated cybersecurity frameworks
- Chapter III — Cooperation at union and international level
- Chapter IV — Cybersecurity risk-management measures and reporting obligations
- Chapter V — Jurisdiction and registration
- Chapter VI — Information sharing
- Chapter VII — Supervision and enforcement
- Chapter VIII — Delegated and implementing acts
- Chapter IX — Final provisions
- Annex I — Sectors of high criticality
- Annex II — Other critical sectors
- Annex III — Correlation table between NIS 2 and NIS
You can read all the NIS 2 articles here: Full Text of NIS 2 Directive.
What are the main cybersecurity requirements of NIS 2?
Surprisingly, only Chapter IV, called “Cybersecurity risk-management measures and reporting obligations,” defines what essential and important entities must do to comply with NIS 2. All the other chapters are not relevant for these companies, because they specify the obligations of the EU countries (Member States), and what government agencies must do to enforce NIS 2.
Chapter IV has the following articles:
- Article 20 - Governance
- Article 21 - Cybersecurity risk-management measures
- Article 22 - Union level coordinated security risk assessments of critical supply chains
- Article 23 - Reporting obligations
- Article 24 - Use of European cybersecurity certification schemes
- Article 25 - Standardisation
For a detailed description of Chapter IV requirements, read this article: The 8 most important cybersecurity and reporting requirements in NIS2.
What are the reporting obligations of essential and important entities?
Essential and important entities must send notifications about significant incidents to:
- A computer security incident response team (CSIRT) or competent authority
- Recipients of their services
Entities need to submit several types of reports to the CSIRT: an early warning, an incident notification, an intermediate report, a final report, and a progress report.
Learn more here: What are reporting obligations according to NIS 2?
How to implement cybersecurity according to NIS 2
To comply with NIS 2, the best practice for essential and important entities is to follow these implementation steps:
- Obtain senior management support.
- Set up project management.
- Perform initial training.
- Write a top-level Policy on information system security.
- Define the Risk Management Methodology.
- Perform risk assessment and treatment.
- Write and approve the Risk Treatment Plan.
- Implement cybersecurity measures.
- Set up supply chain security.
- Set up the assessment of cybersecurity effectiveness.
- Set up incident notifications.
- Set up continual cybersecurity training.
- Conduct periodic internal audits.
- Conduct periodic management review.
- Execute corrective actions.
This article will explain the steps in more detail: 16 implementation steps for NIS 2 cybersecurity risk management measures, while this article will describe how to write all the documents: List of required documents according to NIS 2.
What are NIS 2 fines and liability?
For companies that are not NIS 2 compliant, the fines are as follows:
- For essential entities – up to 10 million euros or 2% of the total annual turnover.
- For important entities – up to 7 million euros or 1.4% of the total annual turnover.
It is important to note that Article 20 requires the top management of essential and important entities to approve the cybersecurity risk management measures and oversee their implementation, and it specifies that top management can be held liable if cybersecurity is not compliant with Article 21.
NIS 2 certification
NIS 2 does not require essential and important entities to get certified.
However, Member States (or the EU commission) may require those entities to use particular IT products or services that are certified in accordance with the European cybersecurity certification scheme according to the Cybersecurity Act (EU Regulation 2019/881).
Which government bodies are defined in NIS 2?
- “Member States” are countries that are members of the European Union – they must publish their own cybersecurity laws and regulations based on NIS 2.
- “Competent authorities” are designated by Member States to supervise the essential and important entities that must be compliant with NIS 2 and local cybersecurity laws.
- “Single points of contact” are established by Member States to enable cross-border cooperation between authorities.
- “Cyber crisis management authorities” are competent authorities, designated by Member States, which are responsible for the management of large-scale cybersecurity incidents and crises.
- “Computer security incident response teams” (CSIRTs) are designated by Member States in order to handle incidents in accordance with defined processes.
- The “European cyber crisis liaison organisation network” (EU-CyCLONe) supports the coordinated management of large-scale cybersecurity incidents and crises.
- The “Cooperation Group” facilitates strategic cooperation and the exchange of information among Member States.
- The “European Union Agency for Cybersecurity” (ENISA) establishes a vulnerability database, creates a biennial report on the state of cybersecurity in the Union, maintains a registry of entities with special status, draws up guidelines regarding the technical areas and existing standards, etc.
Which laws did EU countries publish based on NIS 2? (Transposition of NIS 2)
EU countries (Member States) must publish local laws and regulations related to the NIS 2 Directive by October 17, 2024 – this process of adopting local legislation based on an EU directive is called “transposition.”
As of the date of writing this article, the following Member States have transposed NIS 2 into their local legislation:
- Overview of Croatia’s NIS2 Cybersecurity Regulation
- What are additional requirements of Croatia’s Cybersecurity Act when compared to NIS 2?
- Overview of Lithuania’s Decision on Cybersecurity Requirements
- What are the additional requirements of Lithuania’s Cybersecurity Act when compared to NIS2?
- Overview of the Italian NIS2 law and comparison with the EU NIS2 Directive
- What are the additional requirements of Belgium’s cybersecurity law when compared to NIS 2?
- Overview of Latvia’s Cybersecurity Law and Comparison with the NIS2 Directive
How is NIS2 related to ISO 27001?
NIS 2 does not require the implementation of ISO 27001; however, it does mention the ISO/IEC 27000 series in the preamble as a way to implement cybersecurity risk management measures, and the main part of NIS 2 encourages the use of international standards.
When comparing NIS 2 with ISO 27001 more closely, it becomes clear that ISO 27001 provides an excellent framework for complying with the cybersecurity risk management measures required by NIS 2.
ISO 27001 provides a clear guide on how to define the risk management process, how to combine technical implementation with training and other HR issues, how to involve the top management, etc.
What is the difference between NIS 2 and the EU GDPR?
The full title of the EU GDPR is “Regulation (EU) 2016/679 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data (General Data Protection Regulation).”
Even though both NIS 2 and the GDPR both focus on protection of data, they are quite different:
| NIS 2 | EU GDPR | |
| Type | Directive (companies comply with local legislation that is published) | Regulation (directly applicable to companies) |
| Applies to | Organizations that are considered essential and important entities | Any organization that processes personal data |
| Protection | Cybersecurity measures are applied to all data within the company | Cybersecurity measures apply to personal data only; there is also a legal aspect of protection of personal data |
| Effective from | October 18, 2024 | May 25, 2018 |
What is the difference between NIS 2 and DORA?
The full title of DORA is “Regulation (EU) 2022/2554 on digital operational resilience for the financial sector.”
Although NIS 2 and DORA were both published on the same day (December 27, 2022), there are big differences between them:
| NIS 2 | DORA | |
| Type | Directive (companies comply with local legislation that is published) | Regulation (directly applicable to financial institutions) |
| Applies to | Organizations that are considered essential and important entities | Financial institutions |
| Protection | Emphasis on cybersecurity measures | Besides cybersecurity measures, the emphasis is also on overall resilience of financial institutions |
| Effective from | October 18, 2024 | January 17, 2025 |
What is the difference between NIS 2 and the Critical Entities Resilience Directive (CER)
The full title of CER is “Directive (EU) 2022/2557 on the resilience of critical entities.”
Although NIS 2 and CER (as well as DORA) were published on the same day (December 27, 2022), they have a different focus:
| NIS 2 | CER | |
| Type | Directive (companies comply with local legislation that is published) | Directive (companies comply with local legislation that is published) |
| Applies to | Organizations that are considered essential and important entities | Organizations that are considered critical according to Member State decision |
| Protection | Emphasis on cybersecurity measures | Emphasis on resilience and business continuity |
| Effective from | October 18, 2024 | October 18, 2024; however, critical entities need to become compliant within 10 months from the day they are designated as critical |
To find all the documents needed for complying with the NIS 2 Directive, check out this NIS 2 Documentation Toolkit that includes all policies, procedures, plans, and other templates.

 Dejan Kosutic
Dejan Kosutic