ISO 27001 IT Security Controls
Sort by:
Filters
Standard
Type
Topic
clear search
Filters
clear filters
Standard
Type
Topic

Articles
ISO 27001
How to set security requirements and test systems according to ISO 27001
by Rhand Leal

Articles
ISO 27001
How to protect against external and environmental threats according to ISO 27001 A.11.1.4
by Rhand Leal

Articles
ISO 27001
How to use penetration testing for ISO 27001 A.12.6.1
by Antonio Jose Segovia

Articles
ISO 27001
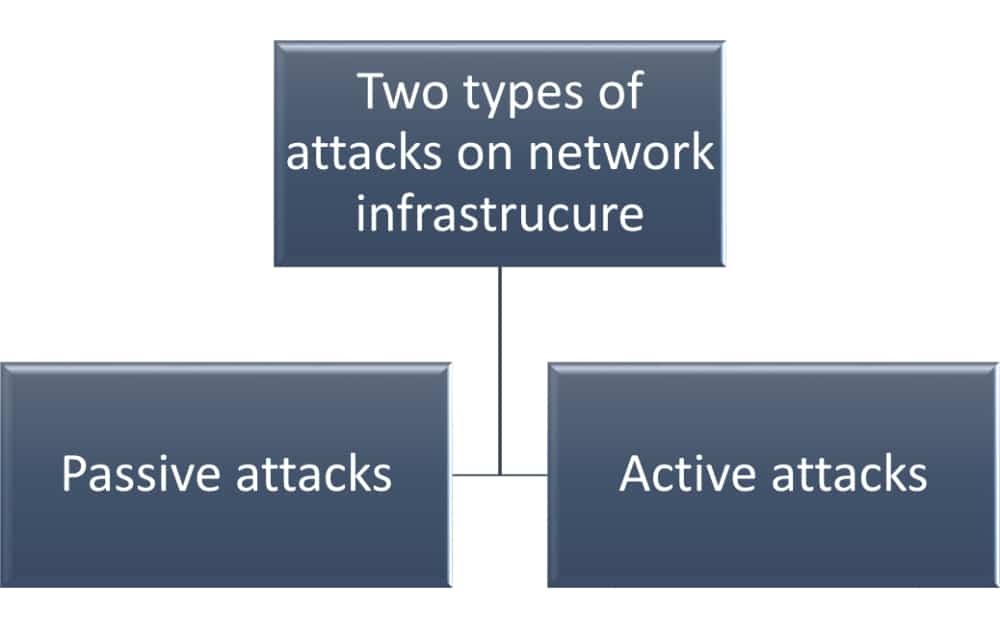
Using Intrusion Detection Systems and Honeypots to comply with ISO 27001 A.13.1.1 network controls
by Rhand Leal

Articles
ISO 27001
How to deal with insider threats?
by Dejan Kosutic

Articles
ISO 27001
The most common physical and network controls when implementing ISO 27001 in a data center
by Neha Yadav
Articles
ISO 27001
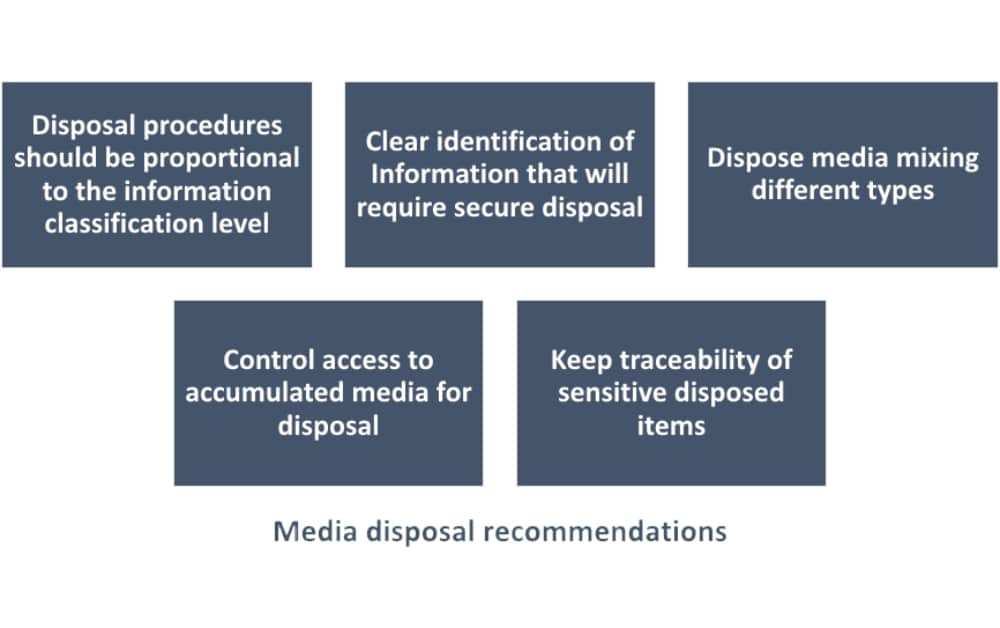
Media & equipment disposal – what is it and how to do it in line with ISO 27001
by Rhand Leal
Articles
ISO 27001
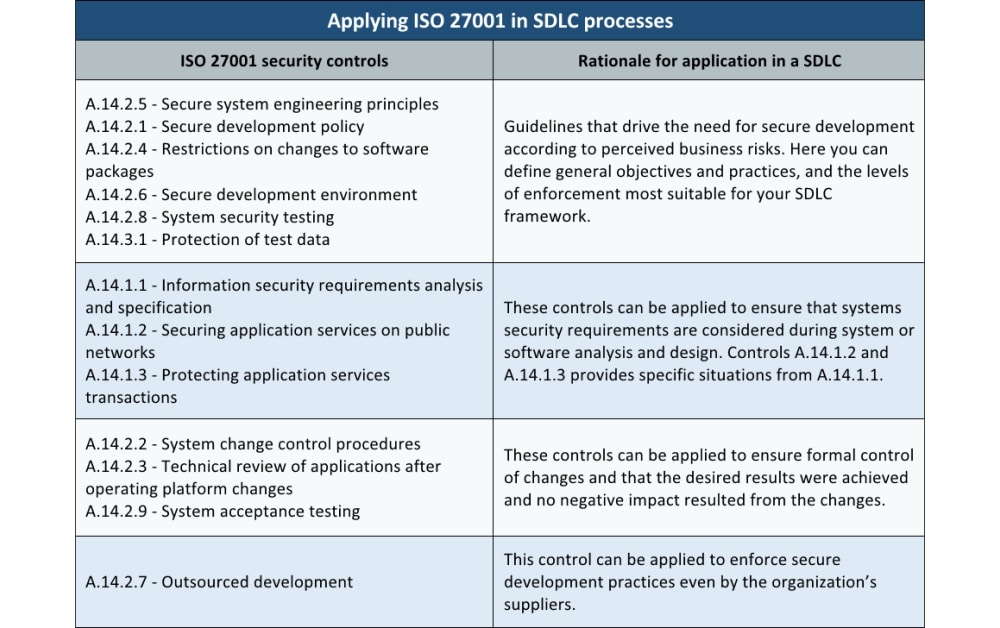
How to integrate ISO 27001 A.14 controls into the system/software development life cycle (SDLC)
by Rhand Leal
Articles
ISO 27001
Implementing capacity management according to ISO 27001:2013 control A.12.1.3
by Ranko Njegovan
Articles
ISO 27001
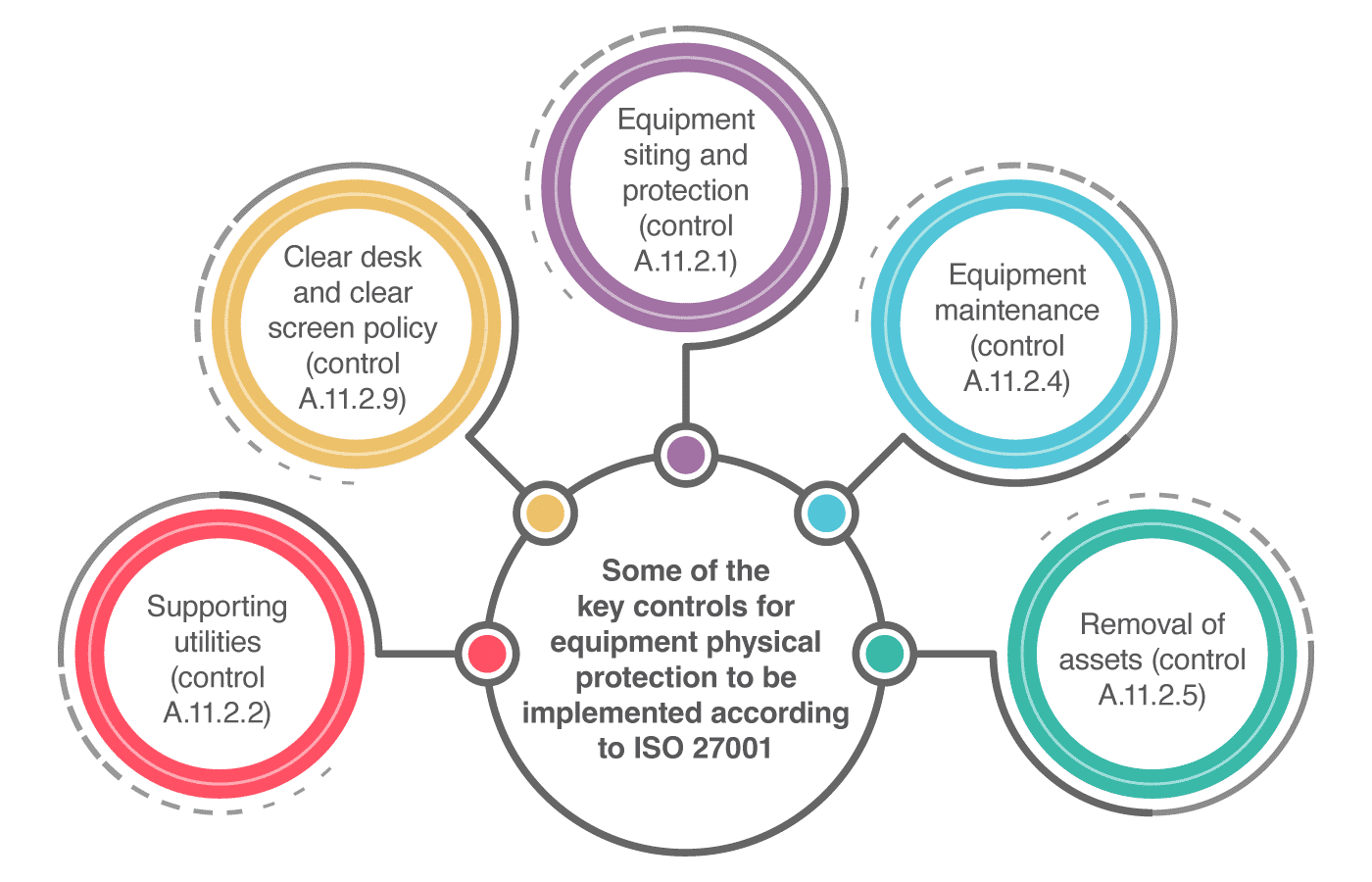
How to implement equipment physical protection according to ISO 27001 A.11.2
by Antonio Jose Segovia

Articles
ISO 27001
How two-factor authentication enables compliance with ISO 27001 access controls
by Rhand Leal
Articles
ISO 27001
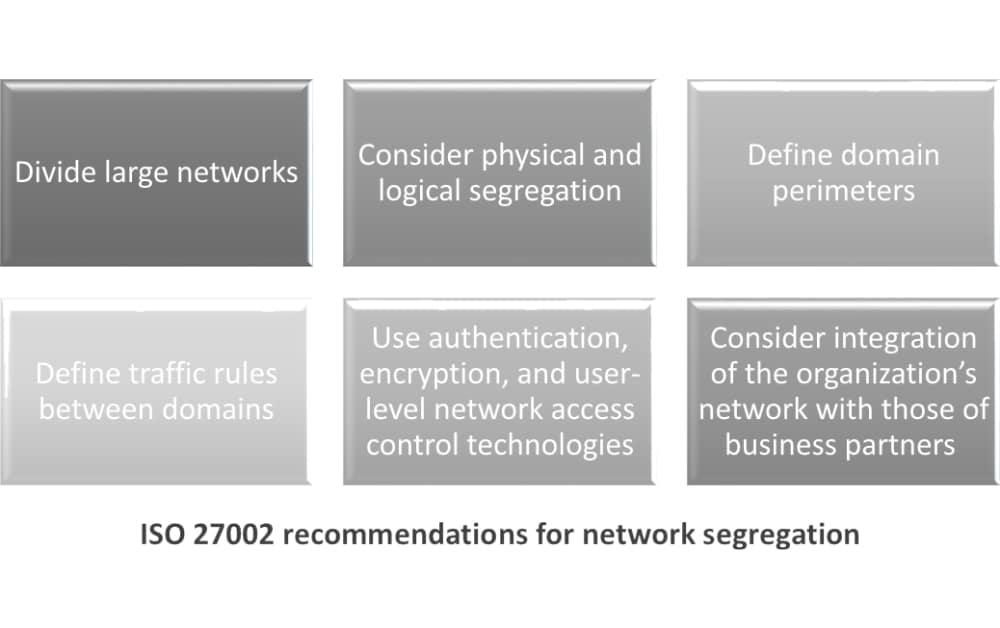
How to implement network segregation according to ISO 27001 control A.13.1.3
by Rhand Leal

Articles
ISO 27001
How to manage the security of network services according to ISO 27001 A.13.1.2
by Antonio Jose Segovia

Articles
ISO 27001
Implementing restrictions on software installation using ISO 27001 control A.12.6.2
by Antonio Jose Segovia

Articles
ISO 27001
How to use firewalls in ISO 27001 and ISO 27002 implementation
by Antonio Jose Segovia
Sort by:
We couldn't find anything
Try adjusting filters or let us help you quickly find what you need by answering a few questions.