The NIS 2 Directive states very clearly that all employees, including the senior management, need to go through cybersecurity training. So, where should you start – which topics should be covered, and how should the whole process be organized?
- Which topics to cover in the training
- How to set up the training process
- Which method to use to deliver the training on a regular basis
Which topics to cover in NIS2 cybersecurity training and awareness
In Chapter IV — Cybersecurity risk-management measures and reporting obligations, NIS2 specifies various activities and security measures that need to be performed.
The best approach to defining topics for cybersecurity training and awareness is to cover each of these activities and measures. However, not all of these topics will be appropriate for everyone in the company — therefore, you will see below that I have separated the topics according to the target audience.
Topics for all employees (including the mid-level and senior management)
- The basics of the NIS2 Directive (cover all relevant articles)
- Basic cyber hygiene practices (Article 21 paragraph 2 point g)
- Incident handling (Article 21 paragraph 2 point b)
- Backup (Article 21 paragraph 2 point c)
- Business continuity (Article 21 paragraph 2 point c)
- The use of multi-factor authentication and continuous authentication solutions (Article 21 paragraph 2 point j)
Topics for IT employees and security managers
- Policy on information system security (Article 21 paragraph 2 point a)
- Disaster recovery (Article 21 paragraph 2 point c)
- Security in network and information systems acquisition, development, and maintenance (Article 21 paragraph 2 point e)
- Policies and procedures regarding the use of cryptography and encryption (Article 21 paragraph 2 point h)
- Access control (Article 21 paragraph 2 point i)
- Asset management (Article 21 paragraph 2 point i)
- Secured voice, video, and text communications (Article 21 paragraph 2 point j)
- Secured emergency communication systems (Article 21 paragraph 2 point j)
Topics specific to security managers
- Steps for NIS 2 compliance (relevant articles in Chapter IV)
- How is NIS 2 related to ISO 27001? (Preamble recital (79), Article 21 paragraph 1, Article 25)
- How is NIS 2 related to DORA? (Preamble recital (28))
- How is NIS 2 related to CER? (Article 2 paragraph 3, Article 3 paragraph 1 point f)
- How is NIS 2 related to the EU GDPR? (Preamble recital (121), Article 35)
- Certification of IT products and services (Article 24)
- Government bodies defined in NIS 2 (several articles)
- Organizing regular cybersecurity trainings for different levels of employees in a company (Article 20 paragraph 2; Article 21 paragraph 2 point g)
- How to perform risk assessment and treatment according to NIS 2 (Article 21 paragraph 1)
- Assessing vulnerabilities and quality of suppliers (Article 21 paragraph 3)
- Human resources security (Article 21 paragraph 2 point i)
- Assessing the effectiveness of cybersecurity risk management measures (Article 21 paragraph 2 point f)
- Taking corrective measures (Article 21 paragraph 4)
Topics for top management and security managers
- What are the essential and important entities that must comply with NIS 2? (Article 3)
- Main cybersecurity requirements of NIS 2 (Article 21)
- Approving and overseeing cybersecurity risk management measures (Article 20 paragraph 1)
- Crisis management (Article 21 paragraph 2 point c)
- Supply chain security (Article 21 paragraph 2 point d)
- Reporting obligations (Article 23)
- NIS 2 fines and liabilities (Article 20 paragraph 1; Article 32 paragraph 6; Article 34)
- Cybersecurity legislation by EU countries (Article 41)
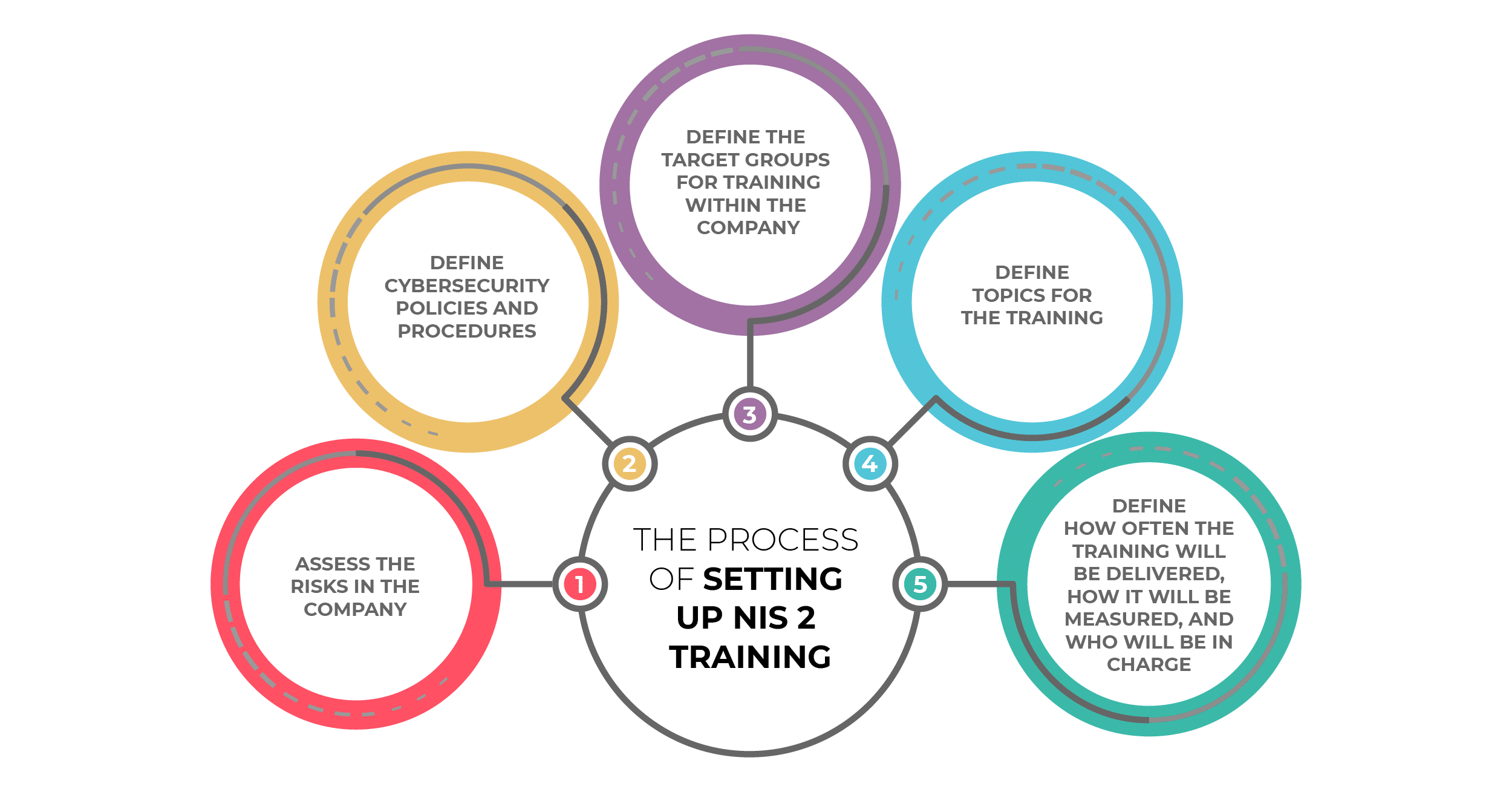
The process of setting up NIS 2 training
Overall, the process of setting up cybersecurity training that is compliant with NIS 2 should follow these steps:
- Assess the risks in the company — this is the basis for writing security documents, and for finding out what to focus on in cybersecurity training.
- Define cybersecurity policies and procedures — this way, cybersecurity roles and responsibilities become clear.
- Define the target groups for training within the company — groups of employees with different cybersecurity roles.
- Define topics for the training – based on risks, roles, and responsibilities – that will differ for various target groups.
- Define how often the training will be delivered, how it will be measured, and who will be in charge.
To learn more about options for delivering NIS 2 cybersecurity training, read this article: Options for delivering NIS 2, DORA, and ISO 27001 training.
Finding the training with the best fit
Ultimately, setting up the training process and selecting the option for delivering training will depend on the circumstances of the particular company — after analyzing your own situation, you can pick the best solutions for you.
To see videos on the above mentioned topics, sign up for a free trial of the Company Training Account to access a series of videos that are designed for a company-wide NIS 2 training program.

 Dejan Kosutic
Dejan Kosutic