Updated: March 23, 2023, according to the ISO 27001 2022 revision.
According to Experian 2023 Second Annual Data Breach Industry Forecast, the largest number of data security breaches are happening because of human error and malicious insiders: “… 82% of data breaches involved a human element. It comes as no surprise as cybercriminals have unleashed an onslaught of phishing emails. They deployed new technology to target employees, gain access to their credentials, and infiltrate systems.” The research also adds that there are about 700,000 unfilled cybersecurity roles in the private sector.
This means that the shortage in cybersecurity professionals requires an alternative approach to solve the main cause of incidents: employee behavior.
To reduce security breaches, besides investing in technology, an organization must set the right processes and properly manage its people. ISO 27001 provides a clue on how to connect all these three elements.
The organizational approach to reduce security incidents
So, how do you approach this problem with employees? ISO 27001, the leading information security standard, offers a less attractive, yet much more effective approach to this problem: (1) strictly defining the security processes, and (2) investing in security training & awareness.
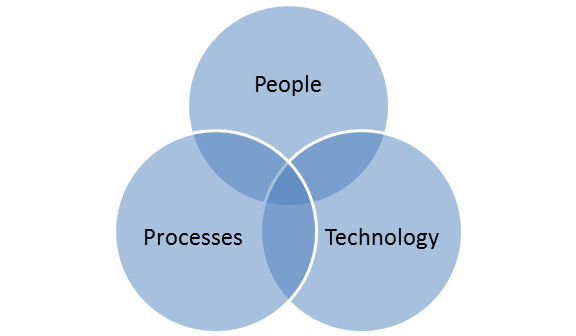
The security experts who developed this standard long ago realized that the technology itself cannot resolve the organizational and the people issues: technology is only a tool; it is only a part of the wider picture. Or, to view this issue from the management theory point of view, the organization is basically a mixture of three essential elements: people, processes, and technology.
Therefore, to resolve the security problems, besides investing in technology, an organization must set the right processes and then manage the people in the proper way. Let’s see how it’s done according to ISO 27001.
Setting the security processes
The first step when setting up the security processes (that is, how the security is organized) is to perform the risk assessment – such an analysis will tell you which potential incidents can happen, and which kind of safeguards are needed to prevent or reduce such incidents. (To learn more about this concept, see this article: The basic logic of ISO 27001: How does information security work?)
For instance, you might identify the risk of losing your data due to inadequate backup – however, it might turn out that you already do have the backup software, but it is not clear who has to configure it (lack of procedure), and/or the employees don’t know how to use it (lack of training).
ISO 27001 suggests 93 safeguards (or controls), which are arranged into these four sections:
- Organizational controls (Annex A section A.5 – 37 controls) are implemented by defining the rules to be followed, as well as expected behavior from users, equipment, software, and systems. E.g., Access Control Policy, BYOD Policy, etc.
- People controls (Annex A section A.6 – 8 controls) are implemented by providing knowledge, education, skills, or experience to enable persons to perform their activities in a secure way. E.g., ISO 27001 awareness training, ISO 27001 internal auditor training, etc.
- Physical controls (Annex A section A.7 – 14 controls) are primarily implemented by using equipment or devices that have a physical interaction with people and objects. E.g., CCTV cameras, alarm systems, locks, etc.
- Technological controls (Annex A section A.8 – 34 controls) are primarily implemented in information systems, using software, hardware, and firmware components added to the system. E.g., backup, antivirus software, etc.
As you’ll notice, a smaller part of these controls are IT-related – most of them are focused on organizational issues, which are resolved by writing various security policies and procedures – for example, Acceptable Use Policy, Classification Policy, BYOD Policy, Access Policy, etc.
See this article to learn how to decide which policies and procedures to write: How to structure the documents for ISO 27001 Annex A controls.
Security training & awareness
The most important rule about training & awareness is that they must be performed in parallel to the implementation of any safeguards (both organizational and technology-based). For instance, if you publish a new Classification Policy without explaining to your employees why it is important and how to classify your documents, such a policy will never take hold in your company; similarly, if you implement new software for tracking incidents, without awareness and training it probably won’t be used too much.
The basic difference between training and awareness is the following: training explains to your employees how to perform a certain activity, while awareness-raising tells them why this is important – both of them have equal importance, and have to be performed in balance.
Here are a couple of training methods you can use:
- Courses – see this article for more information: How to learn about ISO 27001.
- Reading literature – there are many information security books available, as well as magazines.
- Participating in expert forums on the Internet – in some of those you can get very concrete answers to your questions – for example, ISO 27001 security.
- In-house trainings – delivered either by in-house experts, or by hiring consultants, certification bodies, or similar.
For raising awareness, you can use several methods:
- Include employees in documentation development
- Presentations
- Articles on your intranet or newsletter
- Discussions through internal forums
- E-learning
- Videos
- Occasional messages via email or via your intranet
- Gatherings
- Day-to-day in-person communication
For more detailed guidance on these awareness methods, read this article: How to perform training & awareness for ISO 27001 and ISO 22301.
A change in thinking is necessary
It is true that investing in some new and shiny piece of software and/or hardware seems like a much nicer way of resolving security problems, and dealing with processes and people is a much harder thing to do.
But, what we really need is the shift in thinking from “we’ll resolve all the security issues by purchasing technology” to “let’s start thinking about how to use our technology in a secure way” – otherwise, lots of money spent on technology will continue to hit the target only partially, while the incidents will only become larger and larger. And more costly.
If you want to set up Security Awareness Training for your employees, sign up for a free trial of the Company Training Academy, the most practical way to make all of your employees aware of cybersecurity threats.

 Dejan Kosutic
Dejan Kosutic