 Branimir Valentic
Branimir Valentic
December 6, 2017
Implementation, maintenance, training, and knowledge products for Information Security Management Systems (ISMS) according to the ISO 27001 standard.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
All required policies, procedures, and forms to implement an ISMS according to ISO 27001.
Train your key people about ISO 27001 requirements and provide cybersecurity awareness training to all of your employees.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance and training products for critical infrastructure organizations for the European Union’s Network and Information Systems cybersecurity directive.
All required policies, procedures, and forms to comply with the NIS 2 cybersecurity directive.
Company-wide training program for employees and senior management to comply with Article 20 of the NIS 2 cybersecurity directive.
Compliance and training products for financial entities for the European Union’s DORA regulation.
All required policies, procedures, and forms to comply with the DORA regulation.
Company-wide cybersecurity and resilience training program for all employees, to train them and raise awareness about ICT risk management.
Accredited courses for individuals and DORA professionals who want the highest-quality training and certification.
Compliance and training products for personal data protection according to the European Union’s General Data Protection Regulation.
All required policies, procedures, and forms to comply with the EU GDPR privacy regulation.
Train your key people about GDPR requirements to ensure awareness of data protection principles, privacy rights, and regulatory compliance.
Accredited courses for individuals and privacy professionals who want the highest-quality training and certification.
Implementation, training, and knowledge products for Quality Management Systems (QMS) according to the ISO 9001 standard.
All required policies, procedures, and forms to implement a QMS according to ISO 9001.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for Environmental Management Systems (EMS) according to the ISO 14001 standard.
All required policies, procedures, and forms to implement an EMS according to ISO 14001.
Accredited courses for individuals and environmental professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 14001 and the EMS using Advisera’s proprietary AI-powered knowledge base.
Implementation and training products for Occupational Health & Safety Management Systems (OHSMS) according to the ISO 45001 standard.
All required policies, procedures, and forms to implement an OHSMS according to ISO 45001.
Accredited courses for individuals and health & safety professionals who want the highest-quality training and certification.
Implementation and training products for medical device Quality Management Systems (QMS) according to the ISO 13485 standard.
All required policies, procedures, and forms to implement a medical device QMS according to ISO 13485.
Accredited courses for individuals and medical device professionals who want the highest-quality training and certification.
Compliance products for the European Union’s Medical Device Regulation.
All required policies, procedures, and forms to comply with the EU MDR.
Implementation products for Information Technology Service Management Systems (ITSMS) according to the ISO 20000 standard.
All required policies, procedures, and forms to implement an ITSMS according to ISO 20000.
Implementation products for Business Continuity Management Systems (BCMS) according to the ISO 22301 standard.
All required policies, procedures, and forms to implement a BCMS according to ISO 22301.
Implementation products for testing and calibration laboratories according to the ISO 17025 standard.
All required policies, procedures, and forms to implement ISO 17025 in a laboratory.
Implementation products for automotive Quality Management Systems (QMS) according to the IATF 16949 standard.
All required policies, procedures, and forms to implement an automotive QMS according to IATF 16949.
Implementation products for aerospace Quality Management Systems (QMS) according to the AS9100 standard.
All required policies, procedures, and forms to implement an aerospace QMS according to AS9100.
Implementation, maintenance, training, and knowledge products for consultancies.
Handle multiple ISO 27001 projects by automating repetitive tasks during ISMS implementation.
All required policies, procedures, and forms to implement various standards and regulations for your clients.
Grow your business by organizing cybersecurity and compliance training for your clients under your own brand using Advisera’s learning management system platform.
Accredited Lead Auditor and Lead Implementer courses for ISO standards and DORA, and an advanced course to help consultants grow their business.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Find new clients, potential partners, and collaborators and meet a community of like-minded professionals locally and globally.
Implementation, maintenance, training, and knowledge products for the IT industry.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), NIS 2 (critical infrastructure cybersecurity), and DORA (cybersecurity for financial sector).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Compliance, training, and knowledge products for essential and important organizations.
Documentation to comply with NIS 2 (cybersecurity), GDPR (privacy), ISO 27001 (cybersecurity), and ISO 22301 (business continuity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for manufacturing companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for transportation & distribution companies.
Documentation to comply with ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for schools, universities, and other educational organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for telecoms.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with ISO 27001 (cybersecurity), ISO 22301 (business continuity), ISO 20000 (IT service management), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, maintenance, training, and knowledge products for banks, insurance companies, and other financial organizations.
Automate your ISMS implementation and maintenance with the Risk Register, Statement of Applicability, and wizards for all required documents.
Documentation to comply with DORA (cybersecurity for financial sector), ISO 27001 (cybersecurity), ISO 22301 (business continuity), and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and security professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 and the ISMS using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for local, regional, and national government entities.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), GDPR (privacy), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS) and ISO 9001 (QMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for hospitals and other health organizations.
Documentation to comply with ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the medical device industry.
Documentation to comply with MDR and ISO 13485 (medical device), ISO 27001 (cybersecurity), ISO 9001 (quality), ISO 14001 (environmental), ISO 45001 (health & safety), NIS 2 (critical infrastructure cybersecurity) and GDPR (privacy).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 27001 (ISMS), ISO 9001 (QMS), and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the aerospace industry.
Documentation to comply with AS9100 (aerospace), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for the automotive industry.
Documentation to comply with IATF 16949 (automotive), ISO 9001 (quality), ISO 14001 (environmental), and ISO 45001 (health & safety), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 (QMS) and ISO 14001 (EMS) using Advisera’s proprietary AI-powered knowledge base.
Implementation, training, and knowledge products for laboratories.
Documentation to comply with ISO 17025 (testing and calibration laboratories), ISO 9001 (quality), and NIS 2 (critical infrastructure cybersecurity).
Company-wide cybersecurity awareness program for all employees, to decrease incidents and support a successful cybersecurity program.
Accredited courses for individuals and quality professionals who want the highest-quality training and certification.
Get instant answers to any questions related to ISO 9001 and the QMS using Advisera’s proprietary AI-powered knowledge base.
 Branimir Valentic
Branimir Valentic
After years in IT Service Management (ITSM), now I know that the first Information Security Policy that came into my hands was – a miss. It was more like a small book. That document (I wouldn’t even call it a “policy”) contained all that was relevant for information security management. Did I read it? No, at least, not much of it. After many years dealing with policies, processes, and ITSM in general, I know that documents need to be fit for purpose. Policies are not lengthy documents.
In the case of an Information Security Policy, such document needs to give a general approach and direction for information security management. Let’s see how ITIL and ISO 20000 tackle this topic so you can use the requirements (section 6.6, in the case of ISO 20000 implementation) and/or recommendations (in the case of ITIL implementation) to build a strong foundation for information security management.
The Information Security Policy can be seen as the driver of all information security activities. Based on the requirements set in the policy, the company will implement and maintain information security controls in order to preserve the confidentiality, integrity, and availability of information assets of the company (see the article If anything shouldn’t be taken for granted… it’s Information Security Management to learn more).
The Information Security Policy is high-level (meaning, no details) or top-level policy. That means that this policy will provide general guidelines and direction for how to approach information security inside the organization, or in the SMS (if you are implementing ISO 20000).
That fact opens the following consideration – information security has to cover a broad scope and a large number of topics (e.g., access to the system/premise, communication security, security of people, etc.), and the Information Security Policy doesn’t go deep into details. How do you regulate all the needed areas of information security? Well, this is why the Information Security Policy is called a “top-level” policy – based on it, the organization will create other, more detailed policies (e.g., Access control policy, Information classification policy, Password policy, etc.).
Neither ISO 20000 nor ITIL are very prescriptive (in details) about the content of the Information Security Policy. But, there are some requirements that need to be addressed by the policy:
Responsibility – The Information Security Policy is the responsibility of the management accountable for the SMS or IT Service Management (ITSM) in the company. Although ISO 20000 requires that “management with appropriate authority approve” the policy, that shouldn’t be some operative guy (e.g., network administrator), but rather someone from high (or top) management. That’s because the Information Security Policy has company-wide reach and, in order to implement it, you need a strong sponsor.
Requirements and obligations – All relevant statutory and regulatory requirements and contractual obligations must be taken into consideration while creating the policy. Also, don’t forget to consider service requirements that can affect the policy.
Risks – Management of information security risks is at the core of information security management. Therefore, management of risks needs to be defined and conducted (e.g., risk methodology, criteria for acceptable/non-acceptable risks, etc.). The policy must define intervals for information security risk assessment.
Audit – The policy must ensure that internal audits are performed regularly (e.g., defining interval and plan for audits, responsibility to appoint auditor, where to save results, etc.). Once the internal audit is conducted, the Information Security Policy must ensure that results, particularly nonconformities and opportunities for improvements, are identified and acted upon (e.g., by defining where to record them, who is responsible, etc.).
The Information Security Policy is important for all employees of the company, but also for all other parties involved in service management. These are your suppliers, customers, and sub-contractors. So, it’s advisable to define, in the policy, who the users of the policy are (i.e., for whom it is intended), as well as who communicates the policy, and how. But, be careful. If there are customer- or supplier-specific aspects that the policy needs to address, then you need to define these in the policy, and apply them in the SMS.
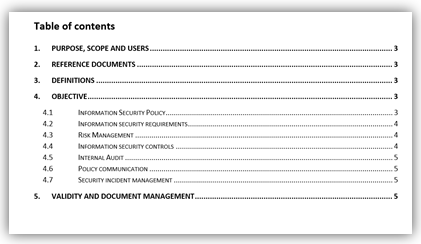
As you could see, the Information Security Policy doesn’t go into processes and related activities or technology. It includes mechanisms that (top) management needs in order to be sure that information security is managed. Therefore, management needs to be involved in the creation of the policy, and for that, they need to understand it.
Avoid a lengthy document (no one reads them, anyway), make it easy to understand, and align it with corporate goals – and you’ve taken the first step in the right direction. Continue making small steps (specific information security policies),and that will get you to the end of the road.
To implement ISO 20000 easily and efficiently, use our ISO 20000 Documentation Toolkit that provides step-by-step guidance for full ISO 20000 compliance.


You may unsubscribe at any time. For more information please see our privacy notice.