Filters
Standard
Type
Topic
clear search
Filters
clear filters
Standard
Type
Topic
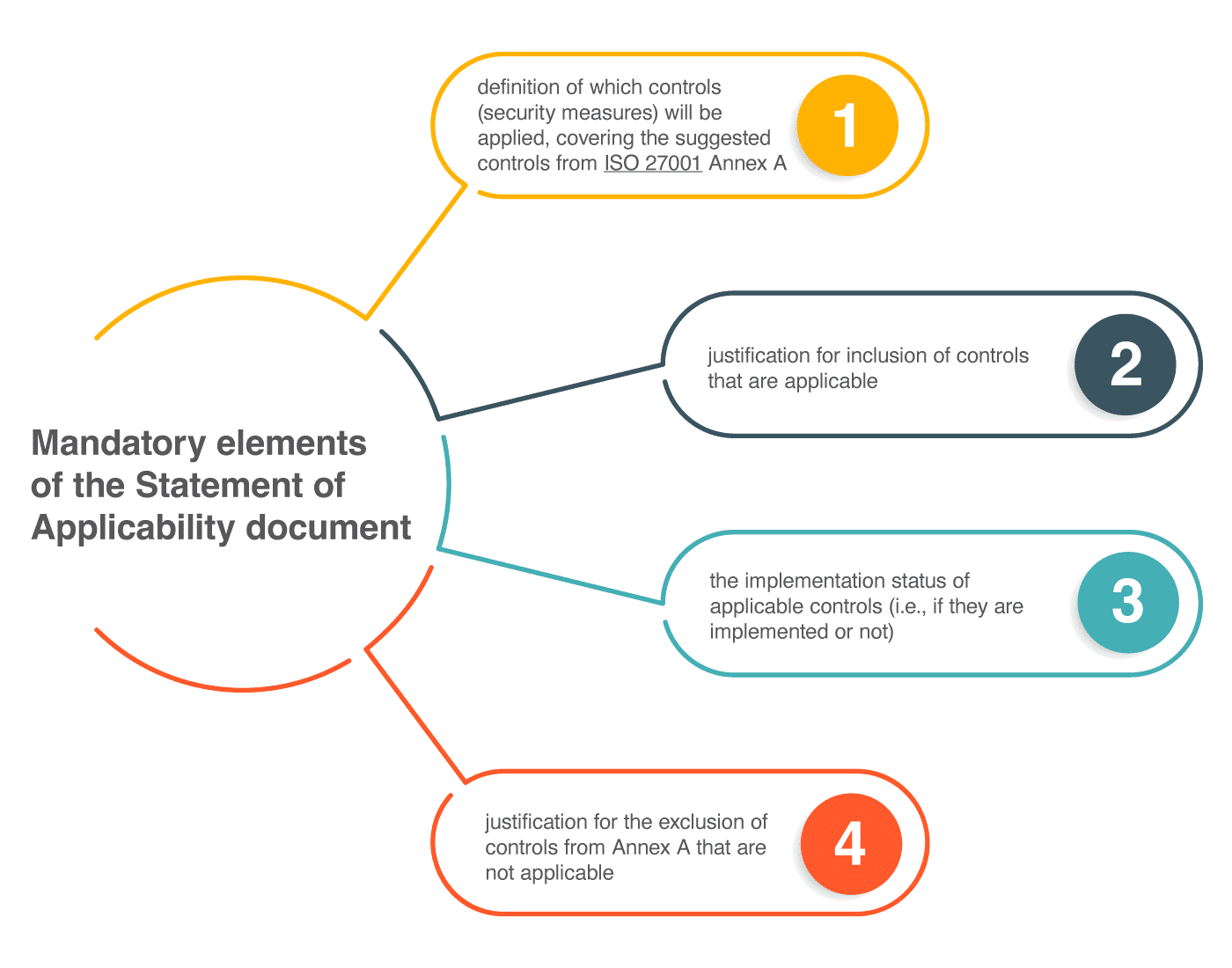
Articles
ISO 27001
Statement of Applicability in ISO 27001 – What is it and why does it matter?
by Dejan Kosutic
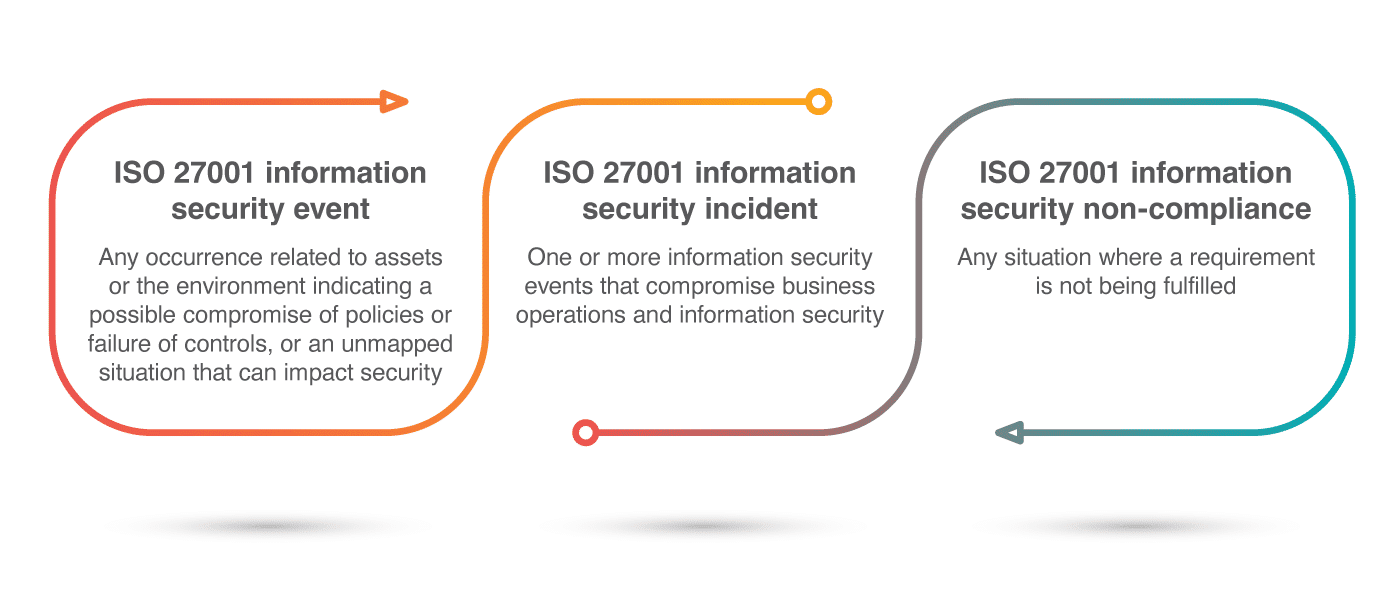
Articles
ISO 27001
ISO 27001 information security event vs. incident vs. non-compliance
by Rhand Leal
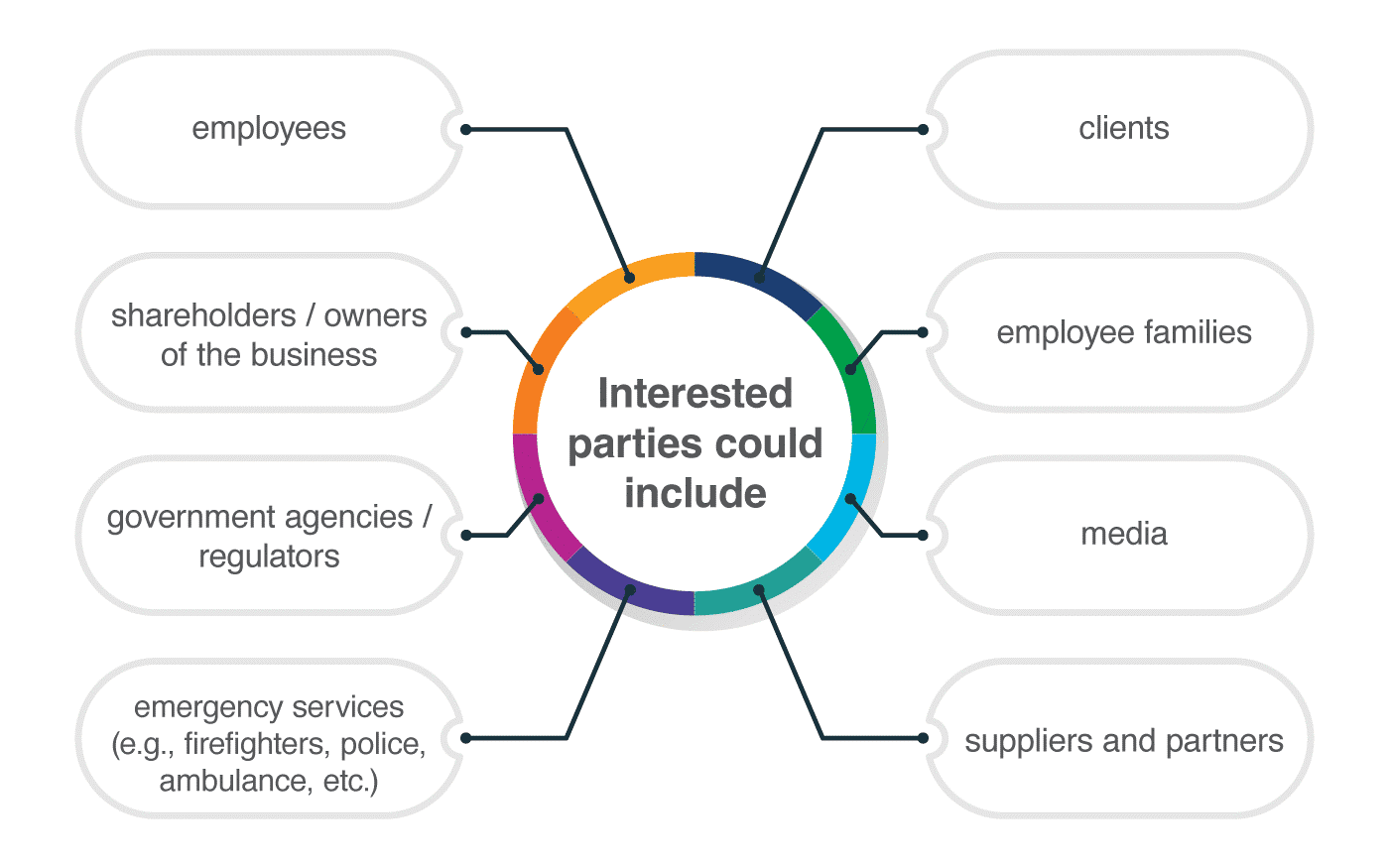
Articles
ISO 27001
Who are interested parties, and how can you identify them according to ISO 27001 and ISO 22301?
by Dejan Kosutic

Articles
ISO 27001
How to manage security in project management according to ISO 27001 A.5.8
by Antonio Jose Segovia

Articles
ISO 27001
How to create a Communication Plan according to ISO 27001
by Jean-Luc Allard
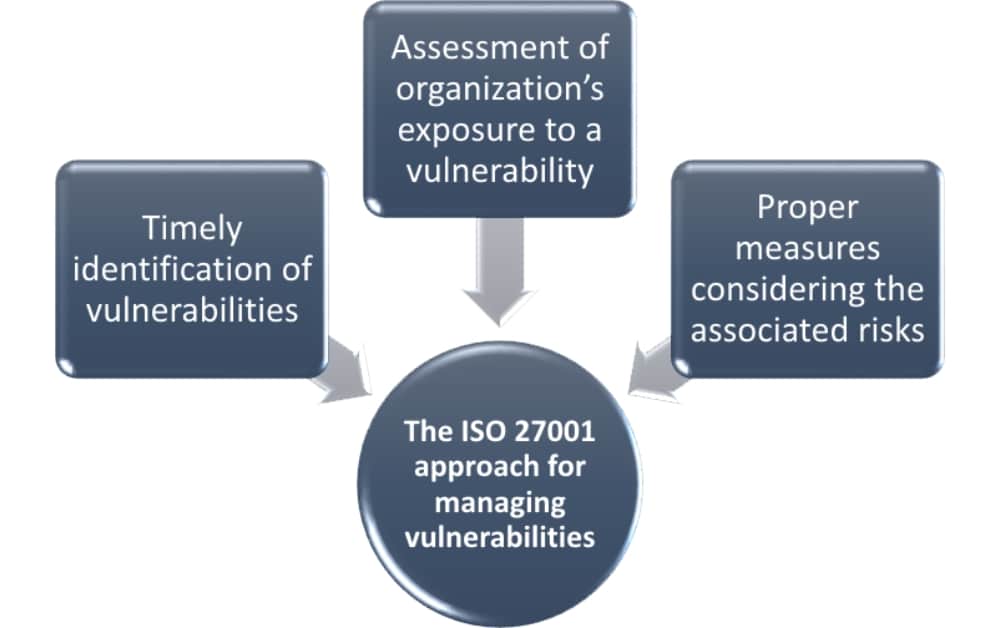
Articles
ISO 27001
How to manage technical vulnerabilities according to ISO 27001 control A.12.6.1
by Rhand Leal

Articles
ISO 27001
How to use Open Web Application Security Project (OWASP) for ISO 27001?
by Antonio Jose Segovia
Articles
ISO 27001
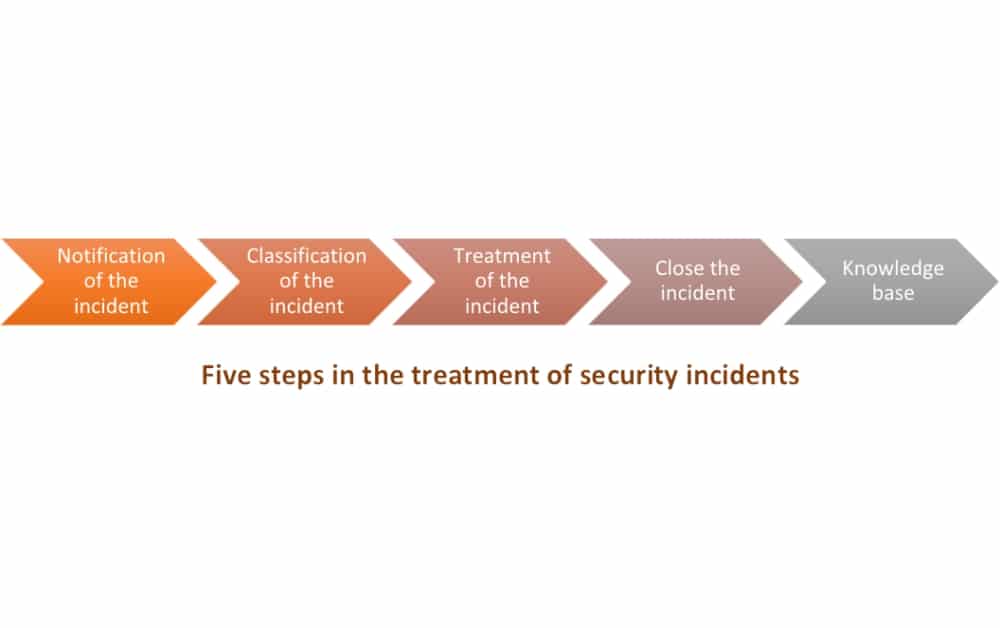
How to handle incidents according to ISO 27001 A.16
by Antonio Jose Segovia
Articles
ISO 27001
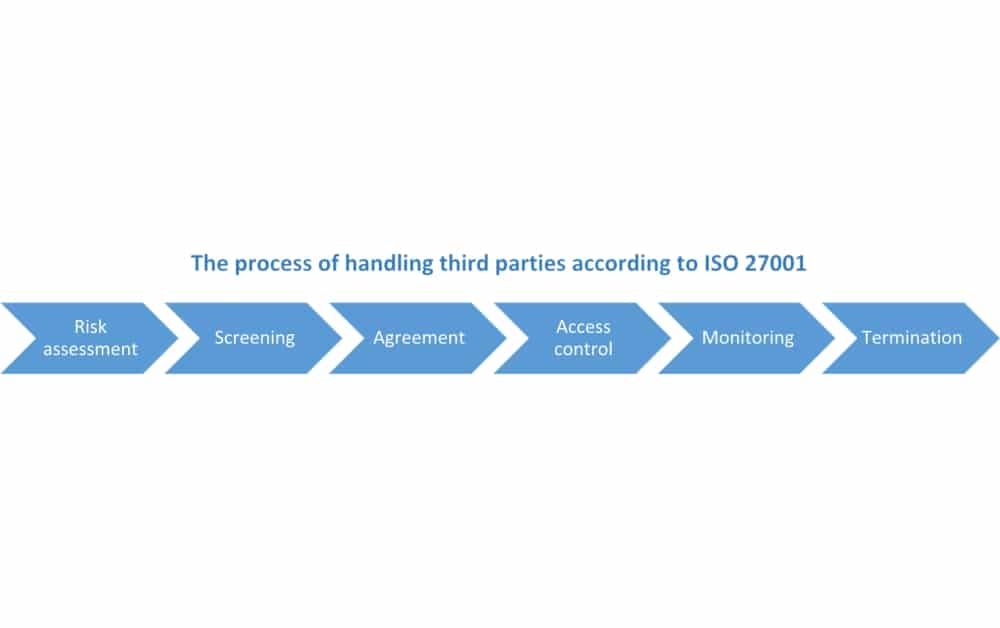
6-step process for handling supplier security according to ISO 27001
by Dejan Kosutic
Articles
ISO 27001
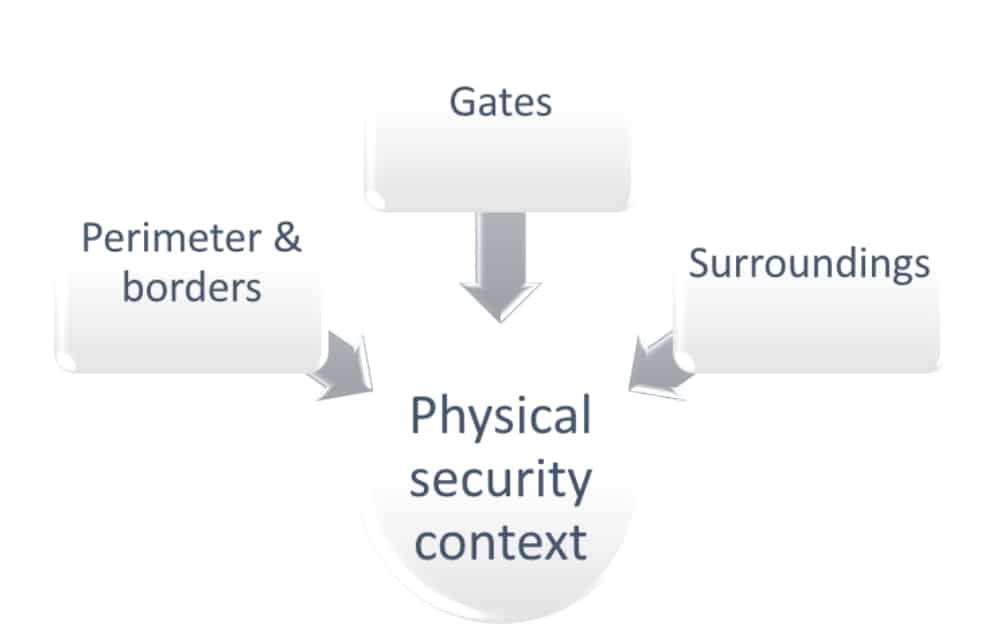
Physical security in ISO 27001: How to protect the secure areas
by Jean-Luc Allard

Articles
ISO 27001
What to consider in case of termination or change of employment according to ISO 27001
by Rhand Leal

Articles
ISO 27001
How to maintain the ISMS after the certification
by Dejan Kosutic

ISO 27001
ISO 27001 project management: Implementing complex security controls using Work Breakdown Structure (WBS)
by Rhand Leal

Articles
ISO 27001
What to consider in security terms and conditions for employees according to ISO 27001
by Rhand Leal

Articles
ISO 27001
Aligning information security with the strategic direction of a company according to ISO 27001
by Dejan Kosutic

Articles
ISO 27001
Problems with defining the scope in ISO 27001
by Dejan Kosutic

Articles
ISO 27001
How to identify ISMS requirements of interested parties in ISO 27001
by Rhand Leal

Articles
ISO 27001
How to use Scrum for the ISO 27001 implementation project
by Antonio Jose Segovia

Articles
ISO 27001
How to gain employee buy-in when implementing cybersecurity according to ISO 27001
by Hannah Churchman

Articles
ISO 27001
Main obstacles to the implementation of ISO 27001
by Dejan Kosutic

Articles
ISO 27001
Information classification according to ISO 27001
by Dejan Kosutic
Articles
ISO 27001
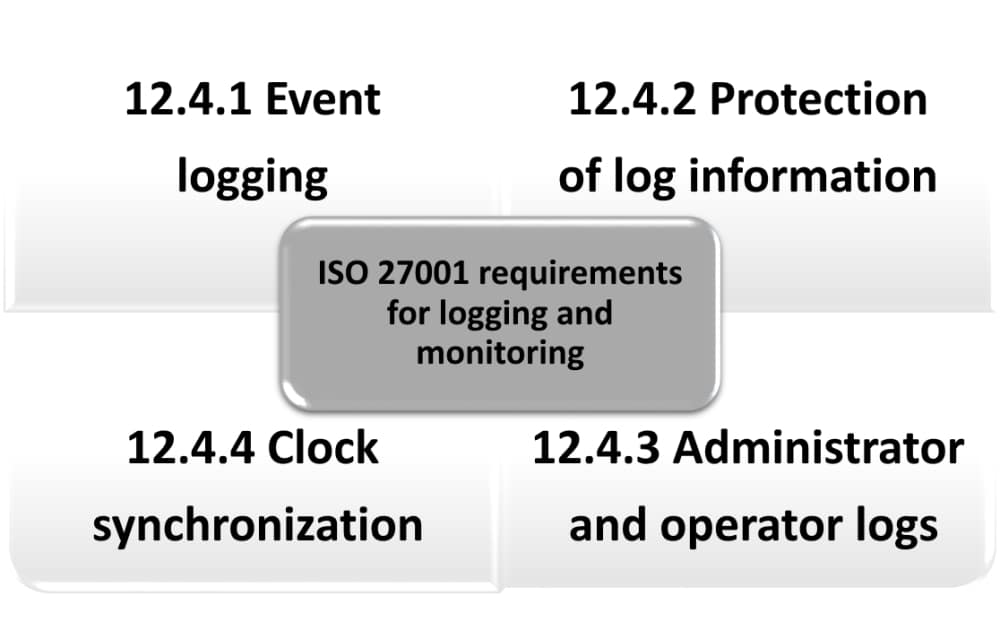
Logging and monitoring according to ISO 27001 A.12.4
by Antonio Jose Segovia
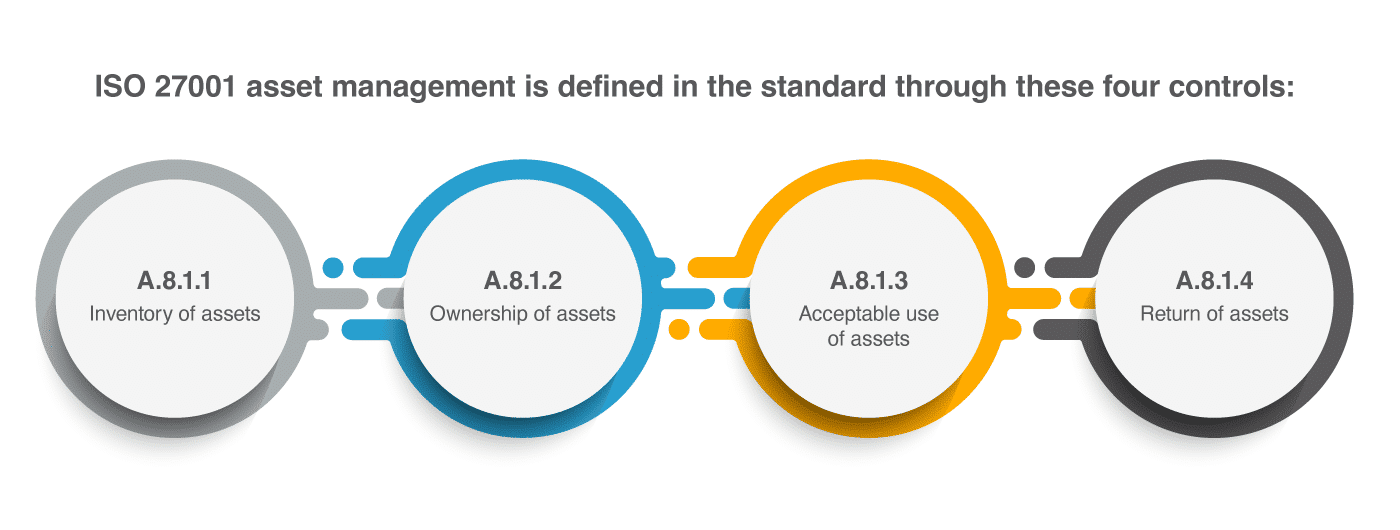
Articles
ISO 27001
Asset management according to ISO 27001: How to handle an asset register / asset inventory
by Dejan Kosutic
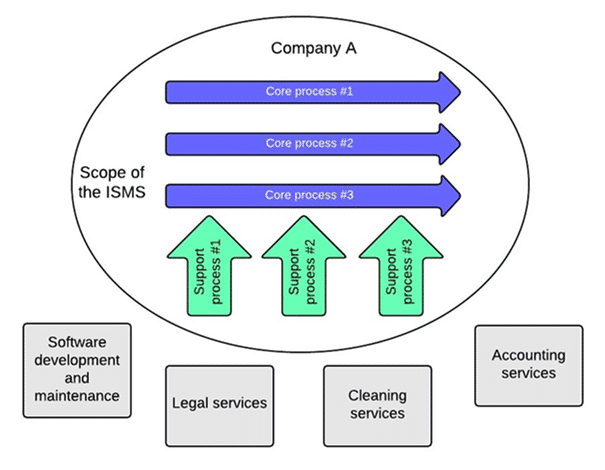
Articles
ISO 27001
How to define the ISMS scope
by Dejan Kosutic
Articles
ISO 27001
How to manage changes in an ISMS according to ISO 27001 A.12.1.2
by Antonio Jose Segovia
Sort by:
We couldn't find anything
Try adjusting filters or let us help you quickly find what you need by answering a few questions.